Battlefield communications require rapid, reliable, and secure information exchange to maintain tactical advantages, often relying on traditional encryption methods vulnerable to evolving cyber threats. Quantum-secure communications utilize quantum key distribution to provide theoretically unbreakable encryption, protecting sensitive data against future quantum computer attacks. Implementing quantum-secure technologies in battlefield communications enhances data integrity and confidentiality, ensuring operational security amid increasingly sophisticated adversaries.
Table of Comparison
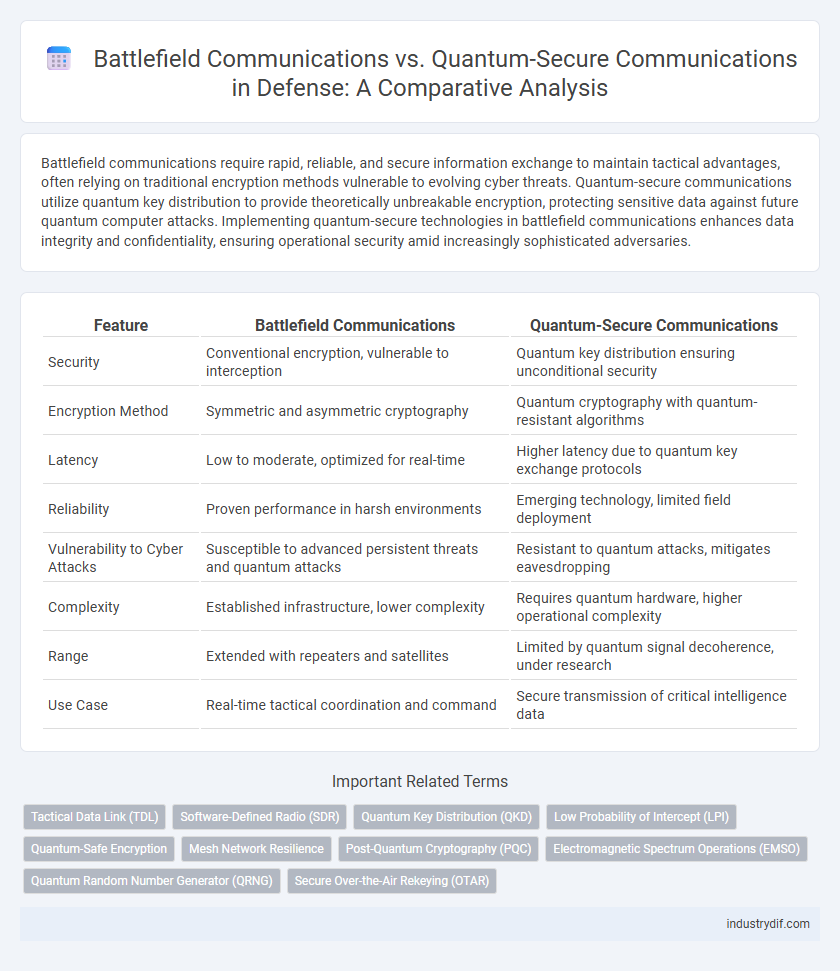
| Feature | Battlefield Communications | Quantum-Secure Communications |
|---|---|---|
| Security | Conventional encryption, vulnerable to interception | Quantum key distribution ensuring unconditional security |
| Encryption Method | Symmetric and asymmetric cryptography | Quantum cryptography with quantum-resistant algorithms |
| Latency | Low to moderate, optimized for real-time | Higher latency due to quantum key exchange protocols |
| Reliability | Proven performance in harsh environments | Emerging technology, limited field deployment |
| Vulnerability to Cyber Attacks | Susceptible to advanced persistent threats and quantum attacks | Resistant to quantum attacks, mitigates eavesdropping |
| Complexity | Established infrastructure, lower complexity | Requires quantum hardware, higher operational complexity |
| Range | Extended with repeaters and satellites | Limited by quantum signal decoherence, under research |
| Use Case | Real-time tactical coordination and command | Secure transmission of critical intelligence data |
Introduction to Modern Battlefield Communications
Modern battlefield communications integrate advanced radio frequency technologies, satellite links, and encrypted digital networks to ensure real-time data exchange among ground troops, air units, and command centers. Quantum-secure communications leverage quantum key distribution (QKD) to provide theoretically unbreakable encryption, enhancing operational security against cyber threats. The combination of conventional and quantum technologies addresses the increasing demand for secure, resilient, and instantaneous communication in complex combat environments.
Evolution of Military Communication Systems
Military communication systems have evolved from traditional battlefield radios to advanced quantum-secure communications that ensure unprecedented levels of encryption and data integrity. Quantum key distribution (QKD) enables real-time, tamper-proof exchange of sensitive information, significantly enhancing operational security in contested environments. This evolution reflects the strategic imperative to counter cyber threats and electronic warfare, paving the way for next-generation defense communication networks.
Vulnerabilities in Traditional Battlefield Networks
Traditional battlefield communications rely heavily on radio frequency transmissions vulnerable to interception, jamming, and spoofing by adversaries. These conventional networks often lack robust encryption protocols, making sensitive military data susceptible to cyber attacks and unauthorized access. Quantum-secure communications utilize principles of quantum key distribution to eliminate eavesdropping risks, significantly enhancing the security and integrity of battlefield information exchange.
Principles of Quantum-Secure Communications
Quantum-secure communications leverage principles of quantum mechanics such as superposition and entanglement to ensure unbreakable encryption, fundamentally enhancing battlefield communication security. Unlike traditional battlefield communications vulnerable to interception and decryption by adversaries, quantum key distribution (QKD) enables the generation of cryptographic keys that cannot be cloned or intercepted without detection. This principle of quantum indeterminacy ensures that any eavesdropping disrupts the quantum state, alerting military operators to potential breaches and preserving the integrity of sensitive defense communications.
Key Technologies: Encryption and Quantum Key Distribution
Battlefield communications rely heavily on advanced encryption techniques such as AES and RSA to protect sensitive information in real-time combat scenarios. Quantum-secure communications leverage Quantum Key Distribution (QKD), enabling theoretically unbreakable encryption by using quantum mechanics to detect eavesdropping attempts on cryptographic keys. Integrating QKD with classical encryption methods significantly enhances security resilience against emerging quantum computing threats on the modern battlefield.
Comparing Reliability: Conventional vs. Quantum-Secure Systems
Conventional battlefield communications rely on well-established encryption methods and infrastructure, offering proven reliability under diverse operational conditions but remain vulnerable to advanced cyber threats and signal interception. Quantum-secure communications leverage quantum key distribution (QKD) and quantum-resistant cryptographic protocols, enhancing security by detecting eavesdropping attempts and ensuring message integrity, though they face challenges in scalability and deployment in dynamic combat environments. The trade-off between the robust maturity of conventional systems and the heightened security potential of quantum-secure communications defines the evolving landscape of battlefield information assurance.
Real-World Applications: Case Studies and Military Use
Battlefield communications enable real-time coordination and situational awareness through encrypted radio and satellite links, essential for conventional military operations. Quantum-secure communications leverage quantum key distribution to protect data against cyber-espionage, demonstrated in secure drone control systems and naval fleet coordination. Case studies in countries like the United States and China showcase quantum communication networks enhancing command integrity and resistance to hacking in contested environments.
Implementation Challenges and Scalability
Battlefield communications face challenges in maintaining reliable, real-time data exchange under dynamic and adversarial conditions, with constraints in bandwidth, latency, and power supply. Quantum-secure communications introduce complexity through the need for quantum key distribution infrastructure, requiring specialized hardware that is currently expensive and difficult to deploy in mobile or hostile environments. Scalability of quantum-secure systems is limited by key generation rates and distance limitations, whereas traditional battlefield communication systems benefit from mature, scalable network protocols optimized for diverse terrains and operational tempos.
Future Roadmap: Integrating Quantum Security in Defense
Future defense communication systems are focused on integrating quantum-secure technologies to enhance battlefield communications, ensuring resilience against cyber threats posed by quantum computing advancements. Efforts prioritize the development of quantum key distribution (QKD) and post-quantum cryptographic protocols to secure sensitive military data transmissions in real-time tactical environments. This roadmap emphasizes collaboration between defense agencies, research institutions, and technology partners to deploy scalable, robust quantum-resistant communication networks on future battlefields.
Strategic Implications for National Security
Battlefield communications rely on real-time data exchange and robust encryption to maintain operational effectiveness and troop safety during combat. Quantum-secure communications utilize quantum key distribution to prevent interception by adversaries, offering unprecedented protection against cyber espionage and hacking attempts. Integrating quantum-secure technologies into national defense networks enhances strategic resilience, deters technologically advanced threats, and ensures the confidentiality of critical military intelligence.
Related Important Terms
Tactical Data Link (TDL)
Tactical Data Link (TDL) systems form the backbone of battlefield communications by enabling real-time, secure information exchange among military units, yet they remain vulnerable to sophisticated cyber threats and electronic warfare. Quantum-secure communications leverage quantum key distribution (QKD) and quantum-resistant encryption algorithms to protect TDL networks against interception and hacking, ensuring uncompromised data integrity and confidentiality in contested defense environments.
Software-Defined Radio (SDR)
Software-Defined Radio (SDR) enhances battlefield communications by providing adaptable, multi-frequency transmission and reception capable of integrating quantum-secure algorithms to protect against future quantum threats. This flexible architecture supports real-time reconfiguration, ensuring encrypted, resilient communication channels critical for defense operations in contested environments.
Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) revolutionizes battlefield communications by providing theoretically unbreakable encryption through quantum mechanics, ensuring secure key exchange even in contested environments. Unlike traditional battlefield radio communications susceptible to interception and cyber attacks, QKD enables defense forces to establish cryptographic keys with provable security, thwarting eavesdropping attempts and enhancing operational secrecy.
Low Probability of Intercept (LPI)
Battlefield communications require low probability of intercept (LPI) to prevent enemy detection and ensure operational security, often utilizing frequency hopping, spread spectrum, and directional antennas. Quantum-secure communications enhance LPI by employing quantum key distribution (QKD) protocols that detect eavesdropping attempts, providing theoretically unbreakable encryption resistant to interception and decryption by advanced adversaries.
Quantum-Safe Encryption
Quantum-safe encryption enhances battlefield communications by protecting sensitive data against future quantum computing threats, ensuring secure transmission of command and control information. Integrating quantum-resistant algorithms such as lattice-based cryptography significantly mitigates risks from quantum-enabled adversaries, maintaining operational security in contested environments.
Mesh Network Resilience
Battlefield communications rely on traditional mesh networks that provide robust node connectivity and redundancy but remain vulnerable to interception and cyber attacks. Quantum-secure communications enhance mesh network resilience by integrating quantum key distribution (QKD), enabling unbreakable encryption that safeguards data integrity and ensures secure, real-time information exchange in contested environments.
Post-Quantum Cryptography (PQC)
Post-Quantum Cryptography (PQC) is essential for advancing battlefield communications security by protecting military data against quantum computing attacks that compromise classical encryption methods. Integrating PQC algorithms such as lattice-based or code-based cryptography ensures quantum-resilient encryption, safeguarding tactical communication networks and classified information from future cryptographic threats.
Electromagnetic Spectrum Operations (EMSO)
Battlefield communications rely heavily on traditional electromagnetic spectrum operations (EMSO) to enable real-time data exchange and coordination, but they remain vulnerable to jamming, interception, and exploitation by adversaries. Quantum-secure communications leverage principles like quantum key distribution (QKD) to protect EMSO channels against eavesdropping and cyber threats, ensuring robust encryption and secure transmission in contested or denied electromagnetic environments.
Quantum Random Number Generator (QRNG)
Battlefield communications rely on conventional encryption methods vulnerable to cyberattacks, whereas quantum-secure communications employ Quantum Random Number Generators (QRNG) to produce truly unpredictable keys, enhancing cryptographic strength. QRNGs leverage quantum phenomena, such as photon emission randomness, to ensure unbreakable encryption essential for securing sensitive military data in contested environments.
Secure Over-the-Air Rekeying (OTAR)
Secure Over-the-Air Rekeying (OTAR) in battlefield communications enables dynamic encryption key updates to maintain operational security amid hostile environments and electronic warfare threats. Quantum-secure communications enhance OTAR protocols by integrating quantum-resistant algorithms, ensuring future-proof protection against quantum computing attacks that could compromise conventional cryptographic methods.
Battlefield communications vs Quantum-secure communications Infographic
 industrydif.com
industrydif.com