Cyber defense involves implementing protective measures such as firewalls, intrusion detection systems, and encryption to safeguard networks against unauthorized access and attacks. Active cyber deception, on the other hand, uses techniques like honeypots, decoys, and misinformation to mislead attackers, disrupt their activities, and gather intelligence on their tactics. Combining cyber defense with active cyber deception enhances overall security by not only preventing breaches but also proactively engaging and analyzing threats.
Table of Comparison
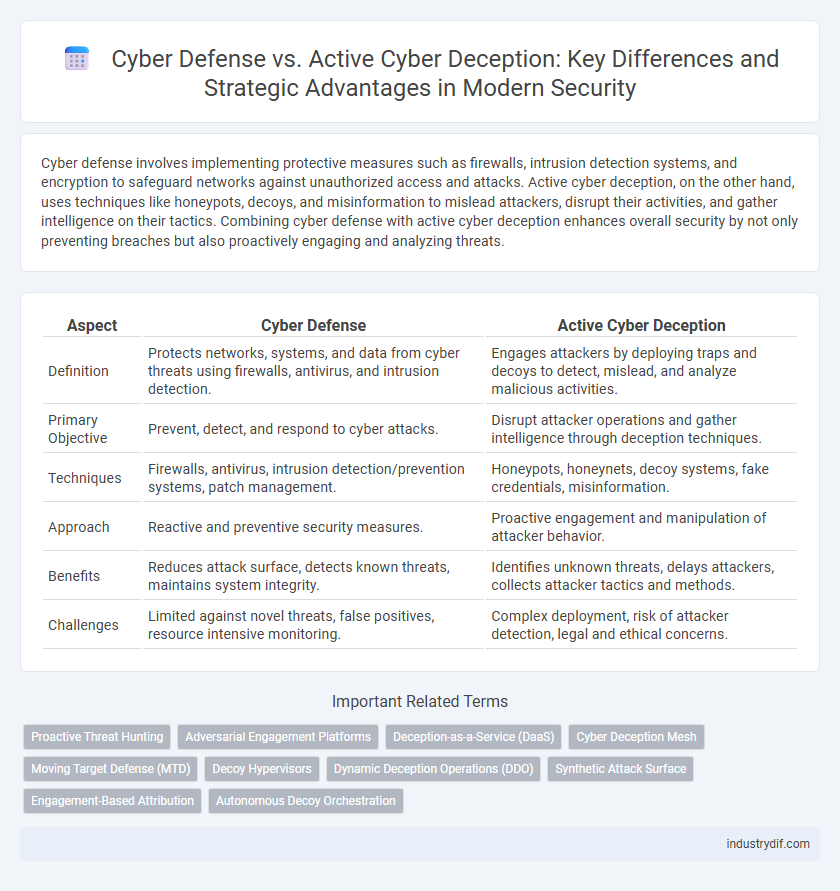
| Aspect | Cyber Defense | Active Cyber Deception |
|---|---|---|
| Definition | Protects networks, systems, and data from cyber threats using firewalls, antivirus, and intrusion detection. | Engages attackers by deploying traps and decoys to detect, mislead, and analyze malicious activities. |
| Primary Objective | Prevent, detect, and respond to cyber attacks. | Disrupt attacker operations and gather intelligence through deception techniques. |
| Techniques | Firewalls, antivirus, intrusion detection/prevention systems, patch management. | Honeypots, honeynets, decoy systems, fake credentials, misinformation. |
| Approach | Reactive and preventive security measures. | Proactive engagement and manipulation of attacker behavior. |
| Benefits | Reduces attack surface, detects known threats, maintains system integrity. | Identifies unknown threats, delays attackers, collects attacker tactics and methods. |
| Challenges | Limited against novel threats, false positives, resource intensive monitoring. | Complex deployment, risk of attacker detection, legal and ethical concerns. |
Introduction to Cyber Defense and Active Cyber Deception
Cyber defense encompasses proactive strategies, technologies, and processes designed to protect networks, systems, and data from cyber threats and unauthorized access. Active cyber deception involves deploying decoys, honeypots, and misleading information to detect, mislead, and disrupt adversaries during cyber attacks. Integrating active cyber deception within cyber defense frameworks enhances threat detection capabilities and strengthens overall cybersecurity posture.
Core Principles of Cyber Defense
Cyber defense is grounded in the principles of confidentiality, integrity, and availability to protect information systems from unauthorized access and disruptions. Active cyber deception enhances these principles by proactively misleading attackers through techniques like honeypots, decoys, and false data to detect and analyze threats in real time. Integrating deception tactics with traditional defense measures strengthens resilience, reduces attack surfaces, and improves threat intelligence for faster incident response.
Fundamentals of Active Cyber Deception
Active cyber deception employs strategically crafted false information, decoys, and honeytokens to mislead attackers and gather intelligence on threat behaviors, enhancing traditional cyber defense mechanisms. This approach disrupts adversaries by creating dynamic environments that mask real assets, enabling early detection and response to cyber intrusions. Fundamentals of active cyber deception include deploying believable decoy systems, real-time threat intelligence correlation, and adaptive countermeasures that evolve with attacker tactics.
Key Technologies in Cyber Defense
Key technologies in cyber defense include advanced intrusion detection systems, real-time threat intelligence platforms, and machine learning algorithms for anomaly detection, which help identify and mitigate cyber threats efficiently. Active cyber deception leverages honeypots, decoy networks, and behavioral analytics to mislead attackers and gather intelligence on adversary tactics. Integrating deception technologies with conventional cyber defense tools enhances situational awareness and fortifies network resilience against sophisticated cyberattacks.
Tools and Techniques in Active Deception
Active cyber deception employs advanced tools such as honeypots, honeynets, and decoy systems that mimic real network assets to mislead attackers and gather intelligence. Techniques include deploying false data and crafted vulnerabilities to lure adversaries into controlled environments, enabling continuous monitoring and threat analysis. These strategies enhance traditional cyber defense by proactively engaging attackers and disrupting their tactics before they impact critical systems.
Comparative Analysis: Cyber Defense vs Active Deception
Cyber defense primarily relies on perimeter security measures, threat detection systems, and real-time monitoring to prevent unauthorized access and mitigate cyber threats. Active cyber deception employs tactics such as honeypots, decoys, and misinformation to mislead attackers, gather intelligence, and disrupt their operations within the network. While cyber defense emphasizes protection and response, active deception focuses on proactive engagement and adversary manipulation for enhanced threat intelligence and risk reduction.
Benefits and Limitations of Cyber Defense
Cyber defense provides essential protection by detecting and mitigating cyber threats through firewalls, intrusion detection systems, and real-time monitoring, ensuring network integrity and data confidentiality. Its benefits include robust perimeter security and rapid incident response, but limitations arise from evolving attack techniques, limited visibility into sophisticated threats, and potential false positives. Unlike active cyber deception, which proactively misleads attackers, traditional cyber defense primarily relies on passive measures that may not fully prevent advanced persistent threats (APTs) or insider attacks.
Advantages and Challenges of Active Cyber Deception
Active cyber deception offers strategic advantages in defense by preemptively confusing attackers through decoys, honeypots, and misinformation, which enhances threat intelligence and reduces breach impact. However, challenges include the complexity of deploying realistic deceptive environments, the risk of legal and ethical issues, and the potential for attackers to identify and bypass these traps. Despite these hurdles, active deception strengthens proactive cyber defense by increasing attacker uncertainty and extending detection timeframes.
Integration Strategies: Combining Defense and Deception
Integrating cyber defense with active cyber deception involves deploying layered security measures alongside deceptive tactics to create a comprehensive protection framework. This strategy leverages real-time threat intelligence, automated response systems, and decoy assets to mislead attackers and minimize breach impact. Combining defense technologies such as firewalls, intrusion detection systems, and deception platforms enhances detection accuracy and improves overall resilience against advanced persistent threats.
Future Trends in Cyber Defense and Deception
Emerging future trends in cyber defense emphasize the integration of artificial intelligence and machine learning to enhance threat detection and response capabilities. Active cyber deception evolves by deploying sophisticated honeypots and adaptive decoy systems that dynamically mimic real network environments, confusing attackers and gathering intelligence. These advancements drive proactive defense strategies, enabling organizations to anticipate and neutralize cyber threats before they cause significant damage.
Related Important Terms
Proactive Threat Hunting
Proactive threat hunting leverages active cyber deception techniques to identify and neutralize advanced persistent threats before they infiltrate critical defense networks. By integrating real-time analytics with decoy systems, cyber defense teams enhance situational awareness and reduce response times against sophisticated cyber adversaries.
Adversarial Engagement Platforms
Adversarial Engagement Platforms (AEPs) enhance cyber defense by simulating realistic attack scenarios to deceive and analyze adversaries, improving threat detection and response accuracy. Unlike traditional passive cyber defense, active cyber deception leverages dynamic decoys, honeypots, and misinformation to disrupt attacker reconnaissance and decision-making, strengthening overall network resilience.
Deception-as-a-Service (DaaS)
Cyber defense employs traditional methods like firewalls and intrusion detection systems to protect networks, while Active cyber deception leverages Deception-as-a-Service (DaaS) platforms that deploy decoys and traps dynamically to mislead attackers and gather intelligence. DaaS enhances situational awareness with real-time threat detection and response by integrating automated honeypots, fake assets, and behavioral analytics, significantly reducing breach impact.
Cyber Deception Mesh
Cyber defense integrates multiple layers of security measures, while the Cyber Deception Mesh enhances this by deploying dynamic decoys and traps that confuse attackers and reveal their tactics in real-time. Leveraging AI-driven deception technology within the Cyber Deception Mesh significantly reduces breach dwell time and improves incident response efficiency.
Moving Target Defense (MTD)
Moving Target Defense (MTD) enhances cyber defense by continuously shifting system configurations, IP addresses, and network topologies to create uncertainty for attackers, making exploitation significantly harder. Active cyber deception complements MTD by deploying decoys and fake assets that mislead adversaries, increasing the complexity and cost of launching successful cyber attacks.
Decoy Hypervisors
Decoy hypervisors serve as a sophisticated layer of active cyber deception, creating virtualized environments that mislead attackers by simulating real systems while monitoring their tactics and tools. This proactive approach enhances traditional cyber defense by diverting threats away from critical assets and gathering actionable intelligence to strengthen overall security posture.
Dynamic Deception Operations (DDO)
Dynamic Deception Operations (DDO) enhance cyber defense by proactively misleading adversaries through real-time manipulation of network environments and decoy assets. This approach reduces attack surface exposure and improves threat detection accuracy by creating adaptive, interactive traps that divert and analyze attacker behavior.
Synthetic Attack Surface
Cyber defense strategies increasingly integrate synthetic attack surfaces to mislead adversaries by mimicking real network environments, enhancing detection and response capabilities. Active cyber deception leverages these fabricated assets to divert, identify, and analyze threats, reducing the risk to critical infrastructure and improving overall cyber resilience.
Engagement-Based Attribution
Engagement-Based Attribution leverages active cyber deception techniques to mislead adversaries and gather actionable intelligence by carefully monitoring attacker interactions with decoy systems and honeypots. This approach enhances cyber defense by enabling real-time identification, tracking, and attribution of threat actors through behavioral analysis during their engagement with deceptive network assets.
Autonomous Decoy Orchestration
Autonomous Decoy Orchestration enhances cyber defense by deploying intelligent, adaptive decoys that mimic real assets, confusing attackers and gathering critical threat intelligence without human intervention. This proactive strategy not only reinforces perimeter security but also accelerates incident response by autonomously analyzing attacker behavior and dynamically adjusting decoy environments to counter evolving cyber threats.
Cyber defense vs Active cyber deception Infographic
 industrydif.com
industrydif.com