Traditional arms dealers rely on the production and distribution of physical weaponry, catering to conventional warfare and defense markets. Cyber weapons developers specialize in creating sophisticated digital tools designed to disrupt, infiltrate, or disable enemy systems remotely. The evolving defense landscape increasingly values cyber capabilities for their precision, stealth, and ability to operate in non-physical domains.
Table of Comparison
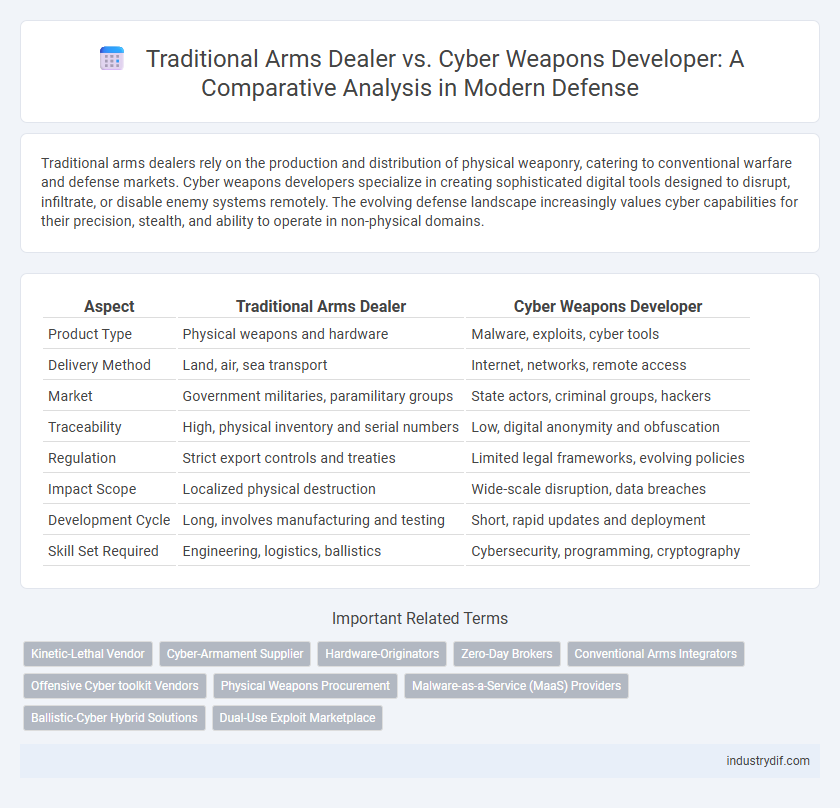
| Aspect | Traditional Arms Dealer | Cyber Weapons Developer |
|---|---|---|
| Product Type | Physical weapons and hardware | Malware, exploits, cyber tools |
| Delivery Method | Land, air, sea transport | Internet, networks, remote access |
| Market | Government militaries, paramilitary groups | State actors, criminal groups, hackers |
| Traceability | High, physical inventory and serial numbers | Low, digital anonymity and obfuscation |
| Regulation | Strict export controls and treaties | Limited legal frameworks, evolving policies |
| Impact Scope | Localized physical destruction | Wide-scale disruption, data breaches |
| Development Cycle | Long, involves manufacturing and testing | Short, rapid updates and deployment |
| Skill Set Required | Engineering, logistics, ballistics | Cybersecurity, programming, cryptography |
Overview: Traditional Arms Dealers vs. Cyber Weapons Developers
Traditional arms dealers primarily supply physical weaponry such as firearms, missiles, and explosives to military and paramilitary forces worldwide. Cyber weapons developers create sophisticated software tools designed to infiltrate, disrupt, or disable digital infrastructure, targeting communication networks, critical systems, and information databases. The shift from tangible arms to digital weapons reflects evolving defense strategies prioritizing cyber warfare capabilities alongside conventional military power.
Evolution of Warfare: From Physical to Digital Battlefields
Traditional arms dealers have historically supplied firearms, artillery, and missiles, facilitating kinetic warfare characterized by physical destruction and territorial control. Cyber weapons developers now create sophisticated malware, ransomware, and hacking tools that disrupt digital infrastructure, signaling a shift to warfare conducted in virtual environments. This evolution from tangible arms to intangible cyber capabilities marks a fundamental transformation in defense strategies, emphasizing information dominance and network security.
Business Models: Arms Trade vs. Cyber Arms Market
Traditional arms dealers operate on a supply-driven business model, focusing on manufacturing and distributing physical weaponry such as firearms, missiles, and armored vehicles to governments and armed groups. Cyber weapons developers, in contrast, utilize a service-oriented model that revolves around creating software exploits, malware, and hacking tools sold or leased through covert channels to state actors and advanced persistent threat groups. The cyber arms market is characterized by rapid innovation cycles, subscription-based access, and scalability, whereas the traditional arms trade relies on high-value contracts and logistical infrastructure.
Legal Frameworks and International Regulations
Traditional arms dealers operate under well-established legal frameworks like the Arms Trade Treaty (ATT) and national export control laws that regulate physical weapons transfers between states. In contrast, cyber weapons developers face a complex and evolving regulatory environment as international law lacks clear definitions and enforcement mechanisms specific to cyber weapons, complicating accountability and state responsibility. Both sectors must navigate a patchwork of treaties, domestic laws, and bilateral agreements, but cyber weapons' intangible nature challenges existing arms control regimes and calls for new international norms.
Technologies Involved: Kinetic Weapons vs. Malware and Exploits
Traditional arms dealers specialize in kinetic weapons such as firearms, missiles, and artillery, relying on mechanical engineering, ballistics, and materials science to enhance lethality and precision. In contrast, cyber weapons developers operate in the digital domain, creating malware, exploits, and advanced persistent threats (APTs) that leverage vulnerabilities in software, network protocols, and operating systems to disrupt or gain unauthorized access to critical defense infrastructure. The technological landscape in defense has thus shifted from purely physical destructive systems to complex cyber capabilities requiring expertise in cryptography, malware development, and network infiltration techniques.
Market Dynamics: Accessibility, Demand, and Distribution
Traditional arms dealers operate within established regulatory frameworks, relying on physical supply chains and government contracts that limit accessibility but ensure stable demand from nation-states and defense agencies. Cyber weapons developers leverage digital platforms, enabling rapid distribution and ease of access to a broader spectrum of clients, including state actors, private firms, and non-state entities, driving increased demand in the cyber defense and offense market. Market dynamics shift as cyber weapons evolve with technological advances, reducing barriers to entry and creating a more fragmented, competitive environment compared to the controlled, centralized nature of traditional arms distribution.
Major Players: Traditional Contractors vs. Cybersecurity Firms
Traditional arms dealers like Lockheed Martin and BAE Systems dominate the defense sector with extensive portfolios of physical weaponry and military hardware. Cyber weapons developers such as CrowdStrike and FireEye specialize in offensive and defensive cyber capabilities, leveraging advanced technologies to counter digital threats. The evolving defense landscape increasingly emphasizes the strategic integration of traditional contractors and cybersecurity firms to address multifaceted security challenges.
Risk Factors: Attribution, Escalation, and Collateral Damage
Traditional arms dealers face clear attribution risks tied to physical weapons supply chains, often allowing states to identify sources and actors involved. Cyber weapons developers contend with complex attribution challenges due to anonymized digital environments, increasing the potential for misidentification and unintended geopolitical escalation. Collateral damage from cyber attacks can inadvertently impact civilian infrastructure and global networks, whereas conventional arms typically have localized physical damage, shaping distinct risk profiles in defense strategies.
Arms Control Challenges in the Digital Age
Traditional arms dealers operate within established regulatory frameworks that focus on physical weapon trafficking and export controls, whereas cyber weapons developers exploit the ambiguity surrounding digital tools and software, complicating enforcement of arms control treaties. The rapid evolution of cyber capabilities outpaces legal definitions, making it difficult to classify and monitor cyber weapons under existing agreements such as the Arms Trade Treaty or the Wassenaar Arrangement. Effective arms control in the digital age requires updated international norms and verification mechanisms to address the dual-use nature of cyber tools and prevent their proliferation.
Future Trends: Convergence of Physical and Cyber Weaponry
The future of defense reveals a growing convergence between traditional arms dealers and cyber weapons developers, driven by advancements in integrated warfare technology. Physical weaponry is increasingly embedded with cyber capabilities, enabling real-time data exchange, enhanced targeting precision, and remote operations. This fusion accelerates the evolution of hybrid warfare, where kinetic and digital attacks complement each other to achieve strategic dominance on the battlefield.
Related Important Terms
Kinetic-Lethal Vendor
Kinetic-lethal vendors specialize in traditional arms manufacturing, producing firearms, missiles, and artillery systems for conventional warfare, emphasizing physical destruction and battlefield dominance. Unlike cyber weapons developers who exploit digital vulnerabilities, kinetic arms rely on tangible hardware with established supply chains and regulatory frameworks within global defense markets.
Cyber-Armament Supplier
Cyber-armament suppliers specialize in advanced digital weaponry, offering sophisticated hacking tools, malware, and cyber-espionage capabilities that outpace traditional arms dealers in stealth and adaptability. Their products enable state and non-state actors to conduct covert operations, disrupt critical infrastructure, and compromise adversaries without physical engagement, revolutionizing modern defense strategies.
Hardware-Originators
Traditional arms dealers specialize in manufacturing and distributing physical weaponry such as firearms, missiles, and armored vehicles, capitalizing on established supply chains and material-based production methods. Cyber weapons developers, unlike hardware-originators, focus primarily on creating software-based offensive tools and exploits, leveraging digital infrastructure and advanced coding techniques rather than traditional hardware manufacturing.
Zero-Day Brokers
Zero-day brokers specializing in undisclosed software vulnerabilities represent a crucial shift in defense strategies, often operating between traditional arms dealers and cyber weapons developers by monetizing exploits before public detection. Their trade not only fuels advanced cyber warfare capabilities but also challenges conventional arms control frameworks by leveraging technology that bypasses physical weapon regulations.
Conventional Arms Integrators
Conventional arms integrators specialize in the assembly and enhancement of traditional weapon systems, providing reliable firepower and proven technology to defense forces worldwide. Their expertise contrasts with cyber weapons developers who focus on digital warfare capabilities, highlighting the strategic importance of physical arms supply chains in maintaining national security.
Offensive Cyber toolkit Vendors
Traditional arms dealers rely on physical weaponry sales and established logistic networks, whereas offensive cyber toolkit vendors specialize in sophisticated software exploits and zero-day vulnerabilities tailored for digital warfare. Cyber weapons developers utilize advanced coding, artificial intelligence, and encryption techniques to create stealthy, persistent tools that can disrupt critical infrastructure, steal sensitive data, or cripple military communications.
Physical Weapons Procurement
Traditional arms dealers specialize in procuring and supplying physical weapons such as firearms, missiles, and armored vehicles, ensuring compliance with international export regulations and logistical challenges. In contrast, cyber weapons developers prioritize software-based tools and digital exploits, relying less on physical procurement and more on advanced coding, cyber intelligence, and network infiltration capabilities.
Malware-as-a-Service (MaaS) Providers
Traditional arms dealers trade physical weaponry such as firearms and explosives, while Cyber weapons developers specialize in creating sophisticated digital tools, notably Malware-as-a-Service (MaaS) platforms that offer scalable, rented access to malicious software. MaaS providers enable state and non-state actors to conduct cyberattacks with minimal technical expertise, significantly expanding the threat landscape beyond conventional arms trafficking.
Ballistic-Cyber Hybrid Solutions
Traditional arms dealers focus on supplying kinetic weaponry such as firearms, missiles, and armored vehicles, emphasizing physical destruction and battlefield dominance. Cyber weapons developers innovate in digital warfare, creating software and cyber tools that disrupt enemy communications, command systems, and critical infrastructure, with Ballistic-Cyber Hybrid Solutions integrating ballistic missile technology and cyber capabilities to enable precise targeting combined with electronic interference for enhanced operational effectiveness.
Dual-Use Exploit Marketplace
Traditional arms dealers primarily trade physical weapons with established global networks, while cyber weapons developers operate in the dual-use exploit marketplace, where software vulnerabilities can be sold for both civilian and military applications. The dual-use exploit marketplace blurs lines between offense and defense, enabling state and non-state actors to acquire sophisticated cyber tools that can disrupt critical infrastructure or bolster cybersecurity capabilities.
Traditional arms dealer vs Cyber weapons developer Infographic
 industrydif.com
industrydif.com