Cybersecurity encompasses a broad range of practices designed to protect systems, networks, and data from unauthorized access, attacks, and damage. Zero Trust Security is a specialized approach within cybersecurity that operates on the principle of never trusting any user or device by default, requiring continuous verification regardless of location. This model enhances security by minimizing insider threats and limiting lateral movement within networks.
Table of Comparison
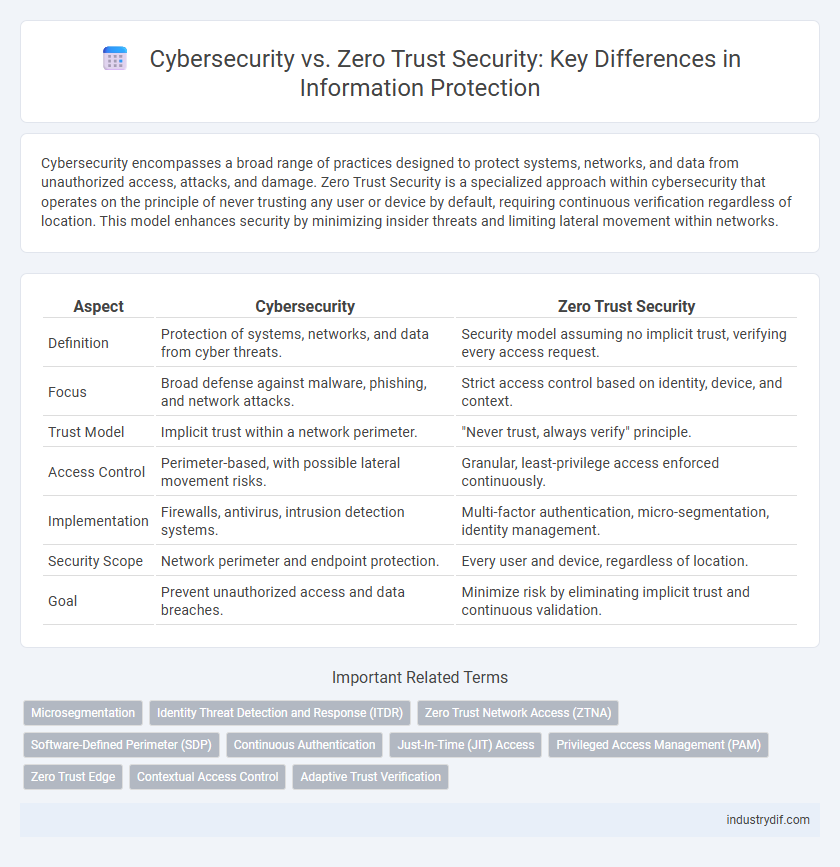
| Aspect | Cybersecurity | Zero Trust Security |
|---|---|---|
| Definition | Protection of systems, networks, and data from cyber threats. | Security model assuming no implicit trust, verifying every access request. |
| Focus | Broad defense against malware, phishing, and network attacks. | Strict access control based on identity, device, and context. |
| Trust Model | Implicit trust within a network perimeter. | "Never trust, always verify" principle. |
| Access Control | Perimeter-based, with possible lateral movement risks. | Granular, least-privilege access enforced continuously. |
| Implementation | Firewalls, antivirus, intrusion detection systems. | Multi-factor authentication, micro-segmentation, identity management. |
| Security Scope | Network perimeter and endpoint protection. | Every user and device, regardless of location. |
| Goal | Prevent unauthorized access and data breaches. | Minimize risk by eliminating implicit trust and continuous validation. |
Understanding Cybersecurity: Core Principles
Cybersecurity encompasses the protection of systems, networks, and data from digital attacks, emphasizing confidentiality, integrity, and availability as core principles. Zero Trust Security is a cybersecurity framework that mandates strict identity verification for every user and device, regardless of network location, to minimize unauthorized access. Understanding these core principles helps organizations implement layered defenses and continuous monitoring to effectively combat evolving cyber threats.
Defining Zero Trust Security: A Paradigm Shift
Zero Trust Security redefines traditional cybersecurity by eliminating implicit trust and enforcing strict identity verification for every user and device attempting to access resources. This paradigm shift emphasizes continuous monitoring, least-privilege access, and micro-segmentation to minimize attack surfaces and prevent lateral movement within networks. By adopting Zero Trust principles, organizations can significantly enhance protection against sophisticated cyber threats and data breaches.
Key Differences Between Cybersecurity and Zero Trust
Cybersecurity encompasses a broad range of practices designed to protect networks, devices, and data from unauthorized access and attacks, while Zero Trust Security is a specific framework that operates on the principle of verifying every user and device regardless of their location. The key difference lies in the approach: traditional cybersecurity often relies on perimeter defenses, whereas Zero Trust eliminates implicit trust and enforces strict access controls based on continuous verification. Zero Trust Security enhances overall cybersecurity by minimizing attack surfaces and assuming breach in every layer of the system.
Traditional Cybersecurity Approaches Explained
Traditional cybersecurity approaches rely heavily on perimeter defenses such as firewalls and intrusion detection systems to protect networks from external threats. These methods assume that users and devices inside the network can be trusted, often leading to vulnerabilities if insider threats or compromised accounts occur. Cybersecurity strategies must evolve beyond these conventional models to address increasingly sophisticated cyberattacks and insider risks effectively.
Zero Trust Architecture: Essential Components
Zero Trust Architecture relies on core components such as continuous authentication, micro-segmentation, and least-privilege access controls to minimize security risks. Network segmentation isolates critical resources while multi-factor authentication verifies user identities consistently. Continuous monitoring and real-time analytics detect suspicious activities, ensuring adaptive and resilient protection against evolving cyber threats.
Threat Identification and Response in Both Models
Cybersecurity frameworks focus on identifying threats through perimeter defense and reactive response mechanisms, relying heavily on known attack signatures and network monitoring tools. Zero Trust Security emphasizes continuous verification and assumes breach scenarios, deploying micro-segmentation and real-time analytics to detect and neutralize threats internally. This proactive model enhances threat identification precision and accelerates incident response times by limiting lateral movement within the network.
Access Management: Perimeter vs. Identity-Based
Cybersecurity traditionally relies on perimeter-based access management, which protects network boundaries to prevent unauthorized entry, but often struggles to secure internal resources once access is granted. Zero Trust Security shifts the focus to identity-based access management, continuously verifying user identities and enforcing least-privilege access across all resources regardless of location. This approach minimizes risks by assuming no implicit trust, ensuring dynamic and granular access control aligned with modern hybrid and cloud environments.
Benefits and Limitations of Cybersecurity Frameworks
Cybersecurity frameworks provide structured guidelines to protect digital assets by identifying risks, implementing controls, and ensuring compliance, enhancing overall organizational security posture. However, traditional cybersecurity frameworks often struggle with evolving threats and insider risks, limiting their effectiveness in dynamic environments. Zero Trust Security addresses these limitations by enforcing strict access controls and continuous verification, but it requires significant cultural and technical shifts that can be complex to implement.
Implementing Zero Trust: Industry Best Practices
Implementing Zero Trust Security requires continuous verification of user identities and strict access controls based on the principle of least privilege. Industry best practices emphasize micro-segmentation, multi-factor authentication (MFA), and real-time monitoring to reduce attack surfaces and detect anomalies swiftly. Integrating Zero Trust frameworks with existing cybersecurity infrastructure enhances resilience against sophisticated threats and insider risks.
Future Trends: Cybersecurity and Zero Trust Convergence
Future trends in cybersecurity emphasize the convergence of traditional cybersecurity frameworks with Zero Trust Security models to enhance threat detection and response. Integrating artificial intelligence and machine learning within Zero Trust architectures enables continuous verification of user identities and device integrity, reducing attack surfaces. This fusion drives a proactive security posture that adapts dynamically to evolving cyber threats in complex digital environments.
Related Important Terms
Microsegmentation
Microsegmentation enhances cybersecurity by dividing a network into isolated segments, limiting lateral movement for potential attackers and reducing attack surfaces in zero trust security models. Implementing microsegmentation is essential for enforcing strict access controls and continuous verification within zero trust architectures, strengthening protection against internal and external threats.
Identity Threat Detection and Response (ITDR)
Identity Threat Detection and Response (ITDR) enhances cybersecurity by continuously monitoring and analyzing identity behaviors to detect anomalies and respond to threats in real time. Zero Trust Security frameworks integrate ITDR to enforce strict identity verification and minimize attack surfaces by assuming no inherent trust within or outside the network perimeter.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) enhances cybersecurity by strictly verifying user identities and device compliance before granting access to applications, reducing the attack surface compared to traditional perimeter-based security models. ZTNA employs continuous authentication and granular policy controls to ensure secure, least-privilege access in dynamic cloud and hybrid environments.
Software-Defined Perimeter (SDP)
Cybersecurity frameworks often integrate Software-Defined Perimeter (SDP) technology to enforce dynamic, identity-centric access controls that minimize attack surfaces by concealing resources from unauthorized users. Zero Trust Security leverages SDP to continuously verify user and device trustworthiness, ensuring strict segmentation and reducing the risk of lateral movement within networks.
Continuous Authentication
Continuous authentication in Zero Trust Security enhances cybersecurity by constantly verifying user identities through behavioral biometrics, device posture, and contextual data, reducing reliance on static credentials. This persistent verification approach mitigates risks of unauthorized access and insider threats, ensuring robust protection in dynamic digital environments.
Just-In-Time (JIT) Access
Just-In-Time (JIT) Access enhances Zero Trust Security by granting users temporary, minimal privileges only when needed, significantly reducing the attack surface compared to traditional cybersecurity models with static access permissions. This dynamic access control limits unauthorized lateral movement and helps prevent privilege escalation in increasingly complex IT environments.
Privileged Access Management (PAM)
Privileged Access Management (PAM) is a critical component in both traditional cybersecurity and Zero Trust Security frameworks, providing controlled access to sensitive systems and minimizing the risk of insider threats or external breaches. Zero Trust Security enhances PAM by enforcing strict verification processes for every access request, ensuring that no user or device is inherently trusted regardless of network location.
Zero Trust Edge
Zero Trust Edge integrates zero trust security principles with edge computing, ensuring continuous verification of users and devices at the network perimeter to prevent unauthorized access. This approach enhances cybersecurity by minimizing attack surfaces and enforcing strict access controls closer to decentralized resources and users.
Contextual Access Control
Cybersecurity frameworks encompass various strategies, with Zero Trust Security emphasizing Contextual Access Control that dynamically adjusts permissions based on user identity, device health, location, and behavior patterns. This approach minimizes attack surfaces by continuously verifying access requests, contrasting traditional perimeter-based defenses that often assume implicit trust within network boundaries.
Adaptive Trust Verification
Cybersecurity frameworks increasingly integrate Adaptive Trust Verification to dynamically assess user credentials and device posture, enhancing protection against evolving threats. Zero Trust Security employs this approach by continuously validating access permissions based on real-time risk factors rather than static trust levels, reducing the attack surface effectively.
Cybersecurity vs Zero Trust Security Infographic
 industrydif.com
industrydif.com