Information Security encompasses broad strategies and technologies designed to protect data confidentiality, integrity, and availability across traditional and modern IT environments. Zero Trust Architecture is a specialized framework within Information Security that operates on the principle of "never trust, always verify," requiring continuous authentication and strict access controls regardless of network location. Implementing Zero Trust Architecture significantly enhances defenses against insider threats and advanced cyberattacks by minimizing implicit trust in users and devices.
Table of Comparison
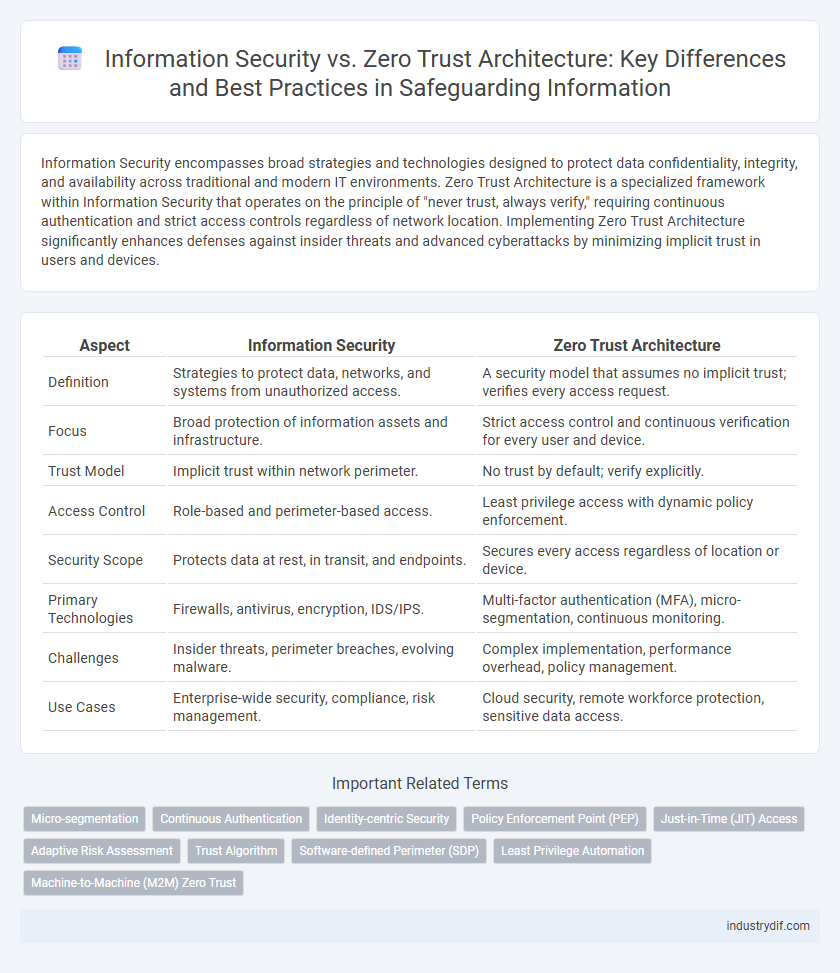
| Aspect | Information Security | Zero Trust Architecture |
|---|---|---|
| Definition | Strategies to protect data, networks, and systems from unauthorized access. | A security model that assumes no implicit trust; verifies every access request. |
| Focus | Broad protection of information assets and infrastructure. | Strict access control and continuous verification for every user and device. |
| Trust Model | Implicit trust within network perimeter. | No trust by default; verify explicitly. |
| Access Control | Role-based and perimeter-based access. | Least privilege access with dynamic policy enforcement. |
| Security Scope | Protects data at rest, in transit, and endpoints. | Secures every access regardless of location or device. |
| Primary Technologies | Firewalls, antivirus, encryption, IDS/IPS. | Multi-factor authentication (MFA), micro-segmentation, continuous monitoring. |
| Challenges | Insider threats, perimeter breaches, evolving malware. | Complex implementation, performance overhead, policy management. |
| Use Cases | Enterprise-wide security, compliance, risk management. | Cloud security, remote workforce protection, sensitive data access. |
Introduction to Information Security and Zero Trust Architecture
Information security focuses on protecting data confidentiality, integrity, and availability through a combination of policies, technologies, and controls. Zero Trust Architecture is a security model that assumes no user or device is trusted by default, enforcing strict identity verification and access controls regardless of network location. This approach minimizes the risk of breaches by continuously validating every access request and segmenting networks to limit the impact of potential attacks.
Overview of Traditional Information Security Approaches
Traditional information security approaches primarily rely on perimeter-based defenses such as firewalls, antivirus software, and intrusion detection systems to protect data and network resources. These methods operate on the assumption that internal network traffic is trustworthy, creating vulnerabilities when unauthorized access occurs within the perimeter. Despite their widespread use, traditional security models struggle to address modern threats like insider attacks and advanced persistent threats, leading organizations to adopt more robust frameworks like Zero Trust Architecture.
Core Principles of Zero Trust Architecture
Zero Trust Architecture centers on the principle of "never trust, always verify," requiring continuous authentication and strict access controls regardless of user location. It emphasizes micro-segmentation, least-privilege access, and real-time monitoring to mitigate risks and prevent lateral movement within networks. Core components include identity verification, device security posture assessment, and encrypted communications to safeguard sensitive information.
Key Differences Between Information Security and Zero Trust
Information Security encompasses a broad set of practices, policies, and technologies aimed at protecting data confidentiality, integrity, and availability across an organization's entire IT environment. Zero Trust Architecture specifically enforces a "never trust, always verify" model by continuously authenticating and authorizing every user and device before granting access to resources, regardless of network location. The key difference lies in Information Security's holistic protective approach compared to Zero Trust's strict, identity-centric access control and micro-segmentation tactics designed to minimize attack surfaces.
Identity and Access Management in Both Models
Information security frameworks emphasize robust Identity and Access Management (IAM) to ensure data confidentiality and integrity, utilizing traditional perimeter defenses and role-based access controls. Zero Trust Architecture redefines IAM by enforcing strict, continuous verification of user identities and device trustworthiness regardless of location, employing principles like least privilege access and micro-segmentation. This approach minimizes insider threats and lateral movement by assuming no implicit trust, thereby enhancing protection in dynamic, cloud-centric environments.
Data Protection Strategies Compared
Information security employs traditional perimeter-based defenses such as firewalls and intrusion detection systems to protect data, while Zero Trust Architecture enforces strict identity verification and micro-segmentation regardless of network location. Data protection strategies under Zero Trust rely heavily on continuous monitoring, least privilege access, and encryption to minimize insider threats and lateral movement. This approach enhances data security by treating all access requests as untrusted until verified, reducing the risk of unauthorized access in dynamic threat environments.
Threat Detection and Response: Traditional vs Zero Trust
Traditional information security relies on perimeter-based defenses that often allow threats to move laterally once inside the network, limiting threat detection to known signatures and reactive response. Zero Trust Architecture enhances threat detection by continuously verifying user and device identities, using micro-segmentation and behavioral analytics to identify anomalies across all access points. This proactive approach enables faster containment and remediation of threats, reducing the risk of breaches and minimizing potential damage.
Implementation Challenges and Best Practices
Implementing Zero Trust Architecture (ZTA) in information security requires overcoming challenges such as legacy system integration, complexity of continuous authentication, and maintaining granular access controls without hindering user productivity. Best practices include adopting a phased approach with comprehensive asset discovery, leveraging micro-segmentation, and implementing robust identity and access management (IAM) solutions to enforce least privilege principles. Continuous monitoring and adaptive security policies enhance resilience against evolving cyber threats while ensuring compliance with industry standards like NIST and ISO 27001.
Industry Adoption Trends and Case Studies
Industry adoption of Zero Trust Architecture (ZTA) is accelerating as organizations prioritize information security to counter increasingly sophisticated cyber threats. Case studies from sectors like finance and healthcare demonstrate that implementing ZTA reduces data breaches by enforcing least-privilege access and micro-segmentation, enhancing protection of critical information assets. Enterprises adopting ZTA report improved compliance with regulations such as GDPR and HIPAA, highlighting its effectiveness in securing sensitive information across complex IT environments.
Future Outlook: Evolving Information Security with Zero Trust
Zero Trust Architecture represents the future of information security by eliminating implicit trust and enforcing strict identity verification across all network access points. With increasing cyber threats and the expansion of remote work, organizations are adopting Zero Trust to enhance resilience and reduce breach risks. Advancements in AI-driven analytics and continuous monitoring will further optimize Zero Trust frameworks, enabling dynamic threat detection and real-time response.
Related Important Terms
Micro-segmentation
Information security leverages micro-segmentation within Zero Trust Architecture to isolate network segments, minimizing attack surfaces and preventing lateral movement of threats. By enforcing granular, identity-based access controls, micro-segmentation strengthens data protection and mitigates risks associated with unauthorized access in complex enterprise environments.
Continuous Authentication
Continuous authentication within Zero Trust Architecture enhances information security by constantly verifying user identity through behavioral biometrics and contextual data, reducing risks of unauthorized access. This adaptive approach contrasts traditional static authentication methods, ensuring real-time protection against evolving cyber threats in dynamic IT environments.
Identity-centric Security
Identity-centric security within Zero Trust Architecture enforces continuous verification of user identities and access privileges, minimizing risks of unauthorized access and data breaches. Unlike traditional perimeter-based information security, Zero Trust treats every access attempt as potentially hostile, relying on multi-factor authentication and adaptive policies tied directly to identity attributes.
Policy Enforcement Point (PEP)
The Policy Enforcement Point (PEP) serves as a critical control element in both Information Security frameworks and Zero Trust Architecture (ZTA), responsible for enforcing access policies and decisions in real-time. In ZTA, PEP operates by continuously validating user identities and device compliance, ensuring that no implicit trust is granted and all access requests are rigorously verified before granting network resources.
Just-in-Time (JIT) Access
Just-in-Time (JIT) Access in Information Security minimizes attack surfaces by granting users temporary, time-limited permissions aligned with Zero Trust Architecture principles, ensuring access is dynamically adjusted based on real-time verification. This approach reduces the risk of unauthorized data exposure by enforcing least-privilege access and continuous authentication within complex network environments.
Adaptive Risk Assessment
Adaptive Risk Assessment in Information Security dynamically evaluates threats by continuously analyzing user behavior, device status, and network context to enforce Zero Trust Architecture principles. This approach minimizes vulnerabilities by enabling real-time access decisions based on risk levels rather than static credentials, enhancing organizational resilience against cyber threats.
Trust Algorithm
Trust algorithms in Information Security evaluate user behavior, device health, and contextual data continuously to enforce access controls dynamically, minimizing risk exposure. Zero Trust Architecture leverages these trust algorithms to authenticate and authorize every access request, ensuring no implicit trust is granted regardless of network location.
Software-defined Perimeter (SDP)
Software-defined Perimeter (SDP) enhances Information Security by creating dynamic, identity-based access controls that obscure critical resources from unauthorized users, reducing attack surfaces and mitigating insider threats. Unlike traditional perimeter defenses, SDP integrates seamlessly with Zero Trust Architecture, enforcing strict verification for every access attempt to ensure continuous protection across hybrid and cloud environments.
Least Privilege Automation
Least Privilege Automation in Information Security enforces strict access controls by dynamically granting users and systems only the minimum necessary permissions, significantly reducing attack surfaces. Zero Trust Architecture integrates this automation to continuously verify and limit access, ensuring robust protection against insider threats and unauthorized access in real-time.
Machine-to-Machine (M2M) Zero Trust
Machine-to-Machine (M2M) Zero Trust Architecture enhances information security by continuously verifying and authenticating device identities and communication requests, eliminating implicit trust between connected devices. This approach mitigates risks associated with unauthorized access and data breaches by enforcing strict micro-segmentation, encryption, and real-time behavioral analytics in M2M interactions.
Information Security vs Zero Trust Architecture Infographic
 industrydif.com
industrydif.com