Firewalls act as barrier systems that monitor and control incoming and outgoing network traffic based on predefined security rules. Zero Trust architecture goes beyond traditional firewalls by continuously verifying every user and device attempting to access resources, assuming no implicit trust. Combining firewall protection with Zero Trust principles enhances security by minimizing attack surfaces and preventing unauthorized access across all network layers.
Table of Comparison
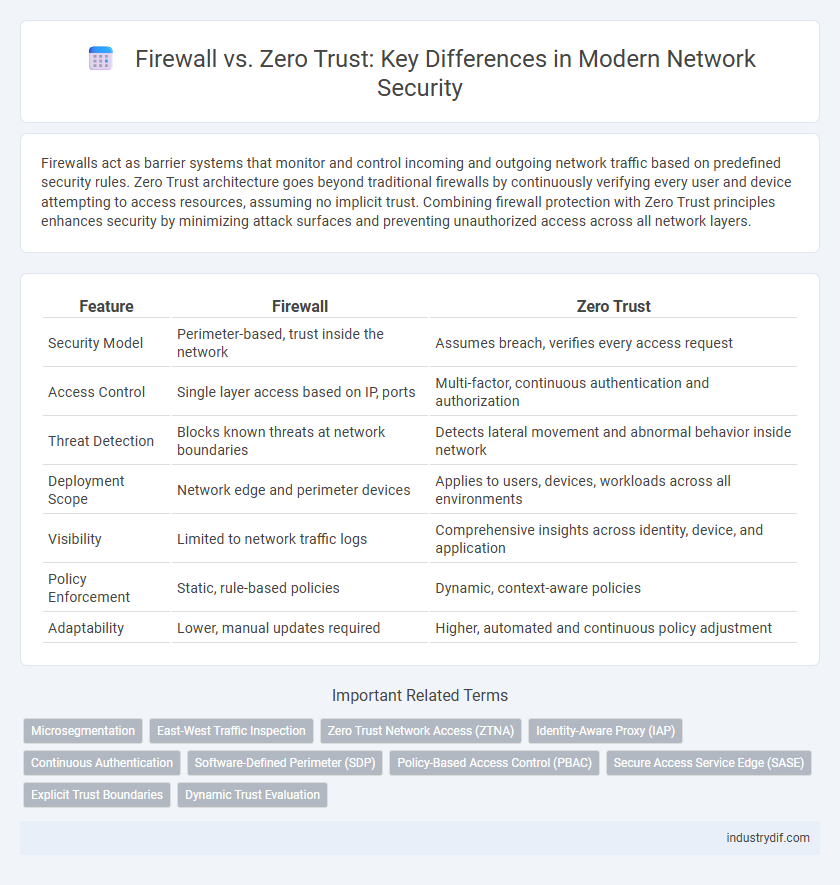
| Feature | Firewall | Zero Trust |
|---|---|---|
| Security Model | Perimeter-based, trust inside the network | Assumes breach, verifies every access request |
| Access Control | Single layer access based on IP, ports | Multi-factor, continuous authentication and authorization |
| Threat Detection | Blocks known threats at network boundaries | Detects lateral movement and abnormal behavior inside network |
| Deployment Scope | Network edge and perimeter devices | Applies to users, devices, workloads across all environments |
| Visibility | Limited to network traffic logs | Comprehensive insights across identity, device, and application |
| Policy Enforcement | Static, rule-based policies | Dynamic, context-aware policies |
| Adaptability | Lower, manual updates required | Higher, automated and continuous policy adjustment |
Introduction to Firewall and Zero Trust
Firewalls are traditional security systems designed to monitor and control incoming and outgoing network traffic based on predetermined security rules, serving as a barrier between trusted internal networks and untrusted external networks. Zero Trust architecture operates on the principle of "never trust, always verify," requiring strict identity verification for every user and device attempting to access resources, regardless of their location within or outside the network perimeter. While firewalls rely on perimeter-based defense, Zero Trust enforces granular, identity-centric security policies across all resources and network segments to minimize exposure and prevent lateral movement of threats.
Core Principles of Firewalls
Firewalls operate on the core principle of establishing a perimeter defense by filtering incoming and outgoing network traffic based on predetermined security rules, primarily focusing on IP addresses, ports, and protocols. They enforce boundary control by permitting or blocking data packets to protect networks from unauthorized access and cyber threats. Unlike Zero Trust, which assumes no implicit trust within the network, traditional firewalls rely heavily on trusted internal network segments and external untrusted zones.
Fundamental Concepts of Zero Trust
Zero Trust architecture operates on the fundamental concept of "never trust, always verify," requiring strict identity verification for every user and device attempting to access resources, regardless of their location within or outside the network perimeter. Unlike traditional firewalls that rely on predefined perimeters and implicit trust for internal traffic, Zero Trust enforces granular access controls, continuous monitoring, and least-privilege principles to minimize risks. Core components of Zero Trust include micro-segmentation, multi-factor authentication (MFA), and real-time analytics to detect and respond to anomalies dynamically.
Key Differences: Firewall vs Zero Trust
Firewalls establish perimeter-based security by filtering incoming and outgoing network traffic based on predefined rules, effectively blocking unauthorized access at network boundaries. Zero Trust architecture eliminates implicit trust and continuously verifies every user and device attempting to access resources, enforcing strict identity verification and least-privilege access controls regardless of location. Unlike traditional firewall models, Zero Trust adopts a micro-segmentation approach, reducing attack surfaces and improving security posture across hybrid and cloud environments.
Network Perimeter Security Explained
Firewall technology establishes a defined network perimeter by controlling inbound and outbound traffic based on predetermined security rules. Zero Trust architecture eliminates the traditional perimeter concept by enforcing continuous verification of user identity and device integrity regardless of network location. Network perimeter security shifts from static boundary defense to dynamic, context-aware access controls that adapt to evolving threats and distributed environments.
Identity and Access Management in Zero Trust
Zero Trust architecture redefines Identity and Access Management (IAM) by enforcing strict user verification and continuous authentication before granting access to resources. Unlike traditional firewalls that rely on perimeter defense, Zero Trust uses dynamic policies based on user identity, device posture, and behavioral analytics to minimize insider threats. This granular control ensures that access privileges are limited to the least privilege necessary, reducing the attack surface significantly.
Advantages and Limitations of Firewalls
Firewalls provide a critical security barrier by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules, effectively blocking unauthorized access and threats at the perimeter. They offer straightforward implementation and are efficient in preventing known attacks, but their traditional focus on perimeter defense limits their ability to protect against insider threats and sophisticated lateral movement within the network. Firewalls lack granular user verification and continuous monitoring, which can result in vulnerabilities in dynamic and modern cloud environments.
Benefits and Challenges of Zero Trust Architecture
Zero Trust Architecture enhances cybersecurity by enforcing strict identity verification for every user and device, significantly reducing the risk of unauthorized access and lateral movement within networks. It enables granular access control and continuous monitoring, ensuring that privileges are dynamically adjusted based on real-time context, which improves threat detection and response. Challenges include complex implementation processes, increased operational overhead, and the need for comprehensive integration with existing security infrastructure and legacy systems.
Integration of Zero Trust with Existing Firewalls
Integrating Zero Trust architecture with existing firewall systems enhances network security by enforcing continuous verification and least-privilege access controls beyond traditional perimeter defenses. Firewalls provide essential traffic filtering based on IP and port, while Zero Trust supplements with identity-aware policies, micro-segmentation, and real-time threat analytics. This combined deployment ensures granular access management and reduces attack surfaces in complex IT environments.
Future Trends in Enterprise Security Approaches
Future trends in enterprise security emphasize a shift from traditional firewall-based perimeter defenses to Zero Trust architectures that assume breach and require continuous verification of user and device identities. Enhanced integration of artificial intelligence and machine learning enables dynamic threat detection and response, minimizing reliance on static rules characteristic of firewalls. Enterprises increasingly adopt micro-segmentation, least privilege access, and cloud-native Zero Trust implementations to address evolving cyber threats and support remote workforce security.
Related Important Terms
Microsegmentation
Microsegmentation in Zero Trust architecture enhances security by dividing a network into granular zones to restrict lateral movement, contrasting with traditional firewalls that primarily focus on perimeter defense. This approach reduces attack surfaces more effectively by enforcing strict access controls between workloads regardless of network location.
East-West Traffic Inspection
Firewall architecture primarily emphasizes perimeter defense, often lacking deep inspection of East-West traffic within the network, leading to potential internal threats going unnoticed. Zero Trust frameworks enforce strict verification and micro-segmentation for East-West traffic, enabling granular inspection and preventing lateral movement of attackers inside the network.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) eliminates implicit trust by continuously verifying user identity and device posture before granting access, significantly enhancing security compared to traditional firewalls that rely on perimeter defenses. Unlike firewalls that filter traffic based on static rules, ZTNA enforces granular, context-aware policies across cloud and on-premises environments, reducing attack surfaces and preventing lateral movement.
Identity-Aware Proxy (IAP)
Identity-Aware Proxy (IAP) enhances security frameworks by enforcing user and device identity verification before granting access, contrasting with traditional firewalls that primarily filter traffic based on IP addresses and ports. IAP integrates zero trust principles by providing granular, context-aware access control, reducing attack surfaces and enabling secure remote access without relying on network perimeter defenses.
Continuous Authentication
Firewalls primarily filter network traffic based on predefined rules, while Zero Trust emphasizes continuous authentication by verifying user and device identity dynamically throughout each session. Continuous authentication reduces security risks by constantly validating access permissions, unlike static firewall defenses that assume trust within the network perimeter.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) enhances network security beyond traditional firewalls by enforcing Zero Trust principles, ensuring access is granted based on user identity and device posture rather than network location. SDP dynamically creates individualized perimeters, reducing attack surfaces and mitigating risks associated with implicit trust in conventional firewall architectures.
Policy-Based Access Control (PBAC)
Policy-Based Access Control (PBAC) in zero trust environments enforces granular, context-aware permissions dynamically, whereas traditional firewalls rely on static rule sets that primarily filter traffic based on IP addresses and ports. PBAC integrates user identity, device posture, and real-time risk assessment to ensure least-privilege access, enhancing security beyond the perimeter-focused control of conventional firewalls.
Secure Access Service Edge (SASE)
Secure Access Service Edge (SASE) integrates firewall functions with Zero Trust principles to deliver comprehensive network security by combining identity-driven access controls with cloud-native security services. Unlike traditional firewalls that rely on perimeter-based defense, SASE enforces continuous verification and micro-segmentation, ensuring secure access to applications and data from any location.
Explicit Trust Boundaries
Firewalls establish explicit trust boundaries by controlling traffic between trusted and untrusted networks based on predefined rules and IP addresses. Zero Trust eliminates implicit trust, continuously verifying every user and device regardless of network location to enforce strict, dynamic access controls.
Dynamic Trust Evaluation
Dynamic Trust Evaluation in Zero Trust continuously assesses user and device behaviors to adapt security policies in real-time, unlike traditional firewalls that rely on static perimeter-based rules. This approach enhances threat detection and minimizes lateral movement by granting access strictly based on context and verified trust levels.
Firewall vs Zero Trust Infographic
 industrydif.com
industrydif.com