Backup involves creating copies of data that can be modified or deleted, which helps in data recovery but remains vulnerable to ransomware or accidental changes. Immutable backups, on the other hand, are designed to be tamper-proof and unalterable once created, ensuring data integrity and protection against cyber threats. Implementing immutable backups significantly enhances data security by preventing unauthorized modification or deletion of critical backup files.
Table of Comparison
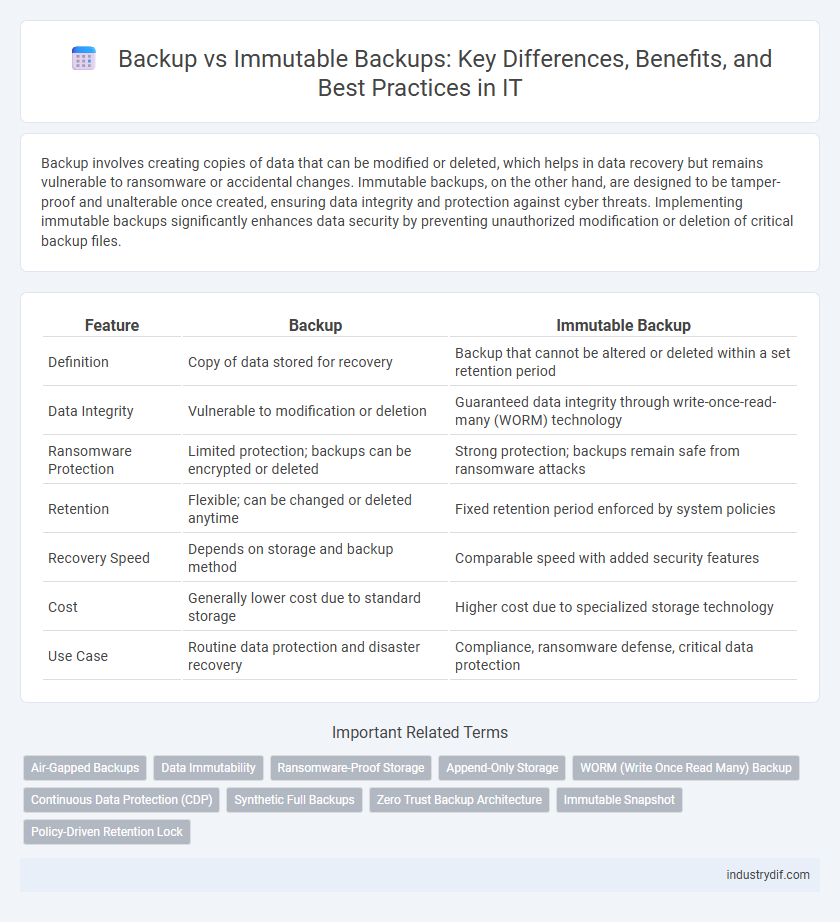
| Feature | Backup | Immutable Backup |
|---|---|---|
| Definition | Copy of data stored for recovery | Backup that cannot be altered or deleted within a set retention period |
| Data Integrity | Vulnerable to modification or deletion | Guaranteed data integrity through write-once-read-many (WORM) technology |
| Ransomware Protection | Limited protection; backups can be encrypted or deleted | Strong protection; backups remain safe from ransomware attacks |
| Retention | Flexible; can be changed or deleted anytime | Fixed retention period enforced by system policies |
| Recovery Speed | Depends on storage and backup method | Comparable speed with added security features |
| Cost | Generally lower cost due to standard storage | Higher cost due to specialized storage technology |
| Use Case | Routine data protection and disaster recovery | Compliance, ransomware defense, critical data protection |
Understanding Backup: Definition and Importance
Backup involves creating copies of data to restore information after data loss, corruption, or disaster, ensuring business continuity and data integrity. Traditional backups are vulnerable to ransomware and accidental deletions, making regular backup schedules and secure storage critical components of data protection strategies. Understanding the limitations of conventional backups helps organizations implement stronger solutions like immutable backups for enhanced security and compliance.
What Are Immutable Backups?
Immutable backups are data copies that cannot be altered, deleted, or tampered with once written, ensuring data integrity and protection against ransomware attacks. These backups use write-once-read-many (WORM) technology or cryptographic hashing to guarantee that stored data remains unchanged over time. Implementing immutable backups enhances cybersecurity frameworks by providing reliable recovery points critical for disaster recovery and compliance with data protection regulations.
Key Differences: Backup vs Immutable Backups
Backup solutions enable data restoration by creating recoverable copies that can be modified or deleted, whereas immutable backups secure data by preventing any alterations or deletions for a defined retention period. Immutable backups leverage technologies like WORM (Write Once, Read Many) storage, ensuring data integrity and protection against ransomware attacks. The key difference lies in data modifiability: standard backups allow changes post-creation, while immutable backups enforce tamper-proof storage to guarantee data permanence.
Data Protection: Risks and Vulnerabilities
Backup systems provide essential data protection but remain vulnerable to ransomware attacks, human error, and hardware failures that can compromise data integrity. Immutable backups enhance security by creating tamper-proof copies that cannot be altered or deleted within a specified retention period, effectively mitigating risks like data corruption and unauthorized modifications. Implementing immutable storage technologies such as Write-Once-Read-Many (WORM) and leveraging blockchain-based backup solutions further strengthen defenses against evolving cyber threats.
Compliance and Regulatory Requirements
Immutable backups provide enhanced compliance by ensuring that stored data cannot be altered or deleted, meeting strict regulatory requirements such as GDPR, HIPAA, and SOX. Traditional backups may be vulnerable to unauthorized changes or ransomware attacks, risking data integrity and regulatory violations. Implementing immutable backup solutions helps organizations achieve audit readiness and maintain data retention policies mandated by industry standards.
Ransomware Resilience: Traditional vs Immutable
Traditional backups store data in a mutable format susceptible to unauthorized alteration or deletion during ransomware attacks, compromising recovery efforts. Immutable backups utilize write-once-read-many (WORM) technology that prevents any modification or deletion within a predefined retention period, ensuring data integrity even under ransomware threats. This immutable architecture significantly enhances ransomware resilience by providing a reliable, tamper-proof recovery source unavailable in conventional backup solutions.
Storage Architecture: How Backups Are Stored
Backup storage typically involves writable media that allows modification or overwriting of data, enabling versioning and incremental backup methods. Immutable backups leverage storage architectures designed to prevent any alteration or deletion within a defined retention period, often using Write Once Read Many (WORM) technology or object storage with immutability policies. This structural difference enhances data integrity and protection against ransomware by ensuring backups remain tamper-proof and recoverable even in compromised environments.
Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO)
Traditional backups typically offer flexible Recovery Point Objectives (RPO) but can result in longer Recovery Time Objectives (RTO) due to data restoration processes. Immutable backups enhance data integrity by preventing alteration or deletion, enabling lower RPOs and significantly faster RTOs in ransomware or data corruption scenarios. Enterprises prioritizing minimal downtime and data loss leverage immutable backup solutions to meet stringent recovery requirements.
Implementation Challenges and Best Practices
Implementing immutable backups involves challenges such as ensuring write-once, read-many (WORM) storage compliance and integrating with existing backup workflows without disrupting recovery time objectives. Best practices include leveraging hardware-based immutable storage, employing cryptographic hashes for data integrity verification, and automating backup verification processes to detect corruption early. Addressing these challenges guarantees reliable data protection and enhances ransomware resilience in enterprise environments.
Future Trends in Backup Technologies
Future trends in backup technologies emphasize the integration of immutable backups to enhance data security and integrity against ransomware attacks. Advanced solutions increasingly combine AI-driven anomaly detection with immutable storage to prevent unauthorized data alterations while ensuring rapid recovery. Cloud-native backup architectures are evolving to support immutable snapshots, enabling scalable, tamper-proof data protection aligned with regulatory compliance requirements.
Related Important Terms
Air-Gapped Backups
Air-gapped backups provide an additional layer of security by isolating backup data from network access, preventing cyber threats such as ransomware from compromising stored information. Unlike immutable backups, which prohibit alteration or deletion within the storage system, air-gapped solutions physically disconnect backup media, ensuring data integrity through complete offline separation.
Data Immutability
Immutable backups ensure data immutability by preventing any alterations or deletions once the backup is created, providing a tamper-proof recovery point critical for ransomware defense. Traditional backups lack inherent immutability, making them vulnerable to accidental or malicious changes that can compromise data integrity.
Ransomware-Proof Storage
Immutable backups utilize write-once, read-many (WORM) technology that ensures data cannot be altered or deleted, providing ransomware-proof storage by preventing unauthorized encryption or modification. Unlike traditional backups, which can be vulnerable to ransomware attacks due to overwriting or deletion, immutable backups maintain a secure, tamper-proof version history critical for reliable disaster recovery.
Append-Only Storage
Backup systems using append-only storage ensure data integrity by preventing overwrites and deletions, which minimizes risks of tampering and ransomware attacks. Immutable backups, leveraging append-only mechanisms, create indelible records that guarantee recovery points remain intact, enhancing disaster recovery and compliance adherence.
WORM (Write Once Read Many) Backup
WORM (Write Once Read Many) backup technology ensures data immutability by preventing any modifications or deletions once the backup is written, providing a critical defense against ransomware and accidental data loss. Unlike traditional backups, immutable backups using WORM guarantee compliance with regulatory standards and enable long-term data retention without risking corruption or tampering.
Continuous Data Protection (CDP)
Continuous Data Protection (CDP) offers real-time backup by capturing every data change, enabling point-in-time recovery without data loss, whereas Immutable Backups ensure data integrity by preventing alteration or deletion of stored backups. CDP enhances recovery objectives by providing granular restore options, while immutability guarantees tamper-proof archives crucial for compliance and ransomware protection.
Synthetic Full Backups
Synthetic full backups enhance data protection by consolidating incremental and differential backups into a single, complete backup without transferring all data again, reducing backup windows and storage needs. When combined with immutable backups, synthetic full backups ensure tamper-proof recovery points, safeguarding against ransomware and accidental deletion.
Zero Trust Backup Architecture
Zero Trust Backup Architecture enforces strict verification and encryption protocols to ensure data integrity, making immutable backups resistant to ransomware and unauthorized modifications. Unlike traditional backups, immutable backups provide tamper-proof recovery points critical for secure disaster recovery in Zero Trust environments.
Immutable Snapshot
Immutable snapshots provide a robust data protection method by preventing any alterations or deletions once the backup is created, ensuring data integrity and resilience against ransomware attacks. Unlike traditional backups, immutable snapshots leverage storage-level immutability features to preserve exact, unchangeable copies of data for specified retention periods.
Policy-Driven Retention Lock
Policy-driven retention lock in immutable backups enforces strict, non-modifiable data retention periods to prevent deletion or alteration, ensuring compliance with regulatory requirements. Unlike traditional backups, this method uses automated policies to secure data integrity, reducing the risk of ransomware and accidental data loss.
Backup vs Immutable Backups Infographic
 industrydif.com
industrydif.com