Traditional encryption secures data by transforming it into an unreadable format that requires decryption before any processing, limiting its use in cloud computing and data analysis. Homomorphic encryption allows computation directly on encrypted data, enabling privacy-preserving operations without exposing sensitive information. This breakthrough technology enhances security in environments where data confidentiality and functional processing must coexist.
Table of Comparison
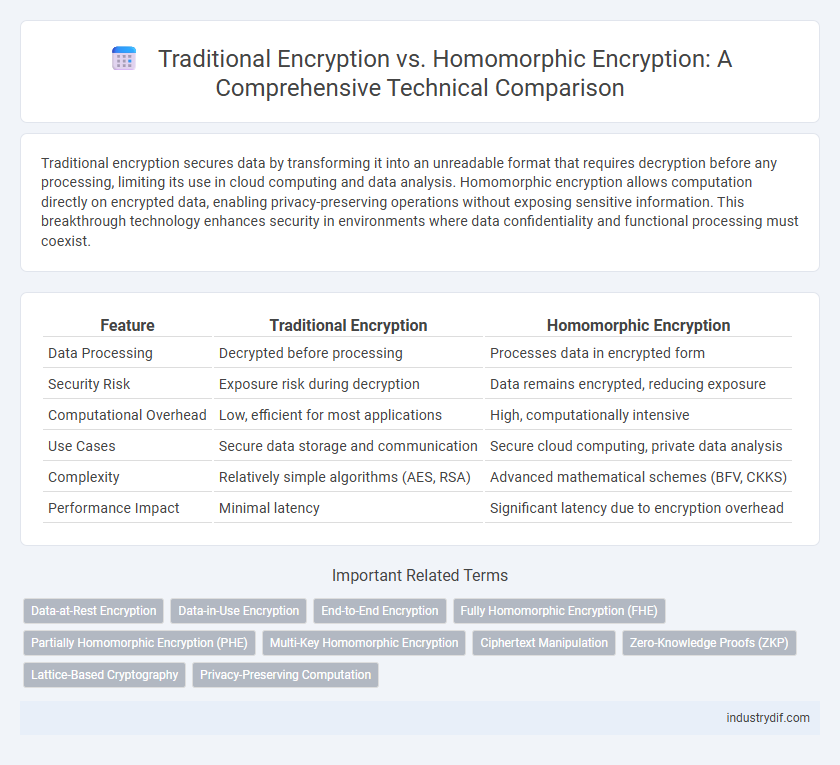
| Feature | Traditional Encryption | Homomorphic Encryption |
|---|---|---|
| Data Processing | Decrypted before processing | Processes data in encrypted form |
| Security Risk | Exposure risk during decryption | Data remains encrypted, reducing exposure |
| Computational Overhead | Low, efficient for most applications | High, computationally intensive |
| Use Cases | Secure data storage and communication | Secure cloud computing, private data analysis |
| Complexity | Relatively simple algorithms (AES, RSA) | Advanced mathematical schemes (BFV, CKKS) |
| Performance Impact | Minimal latency | Significant latency due to encryption overhead |
Introduction to Encryption Technologies
Traditional encryption secures data by transforming plaintext into ciphertext using symmetric or asymmetric keys, requiring decryption for data processing. Homomorphic encryption allows computations directly on encrypted data without decryption, preserving confidentiality throughout processing. This advancement enables secure cloud computing and data analysis while maintaining privacy and compliance with data protection regulations.
Fundamentals of Traditional Encryption
Traditional encryption relies on transforming plaintext into ciphertext using symmetric or asymmetric algorithms such as AES or RSA, ensuring data confidentiality and integrity during storage or transmission. It typically requires decryption with a secret key to access the original data, exposing information during processing. These techniques prioritize security but limit data usability since operations on encrypted data must first be decrypted, increasing vulnerability risks.
Core Principles of Homomorphic Encryption
Homomorphic encryption enables computations on encrypted data without decryption, preserving data privacy throughout processing. Its core principles involve mathematical structures that support addition and multiplication operations directly on ciphertexts, allowing result transformation back into meaningful plaintext. This approach contrasts with traditional encryption, where data must be decrypted before computation, exposing it to potential vulnerabilities.
Data Security: Traditional vs. Homomorphic Methods
Traditional encryption secures data by transforming it into unreadable ciphertext, requiring decryption prior to processing, which exposes data to potential attacks during this phase. Homomorphic encryption enables computation directly on encrypted data without decryption, preserving confidentiality throughout data processing and significantly reducing exposure risks. This advanced cryptographic method enhances data security in cloud computing, financial analysis, and healthcare applications by maintaining end-to-end encryption during operations.
Performance and Computational Efficiency
Traditional encryption methods offer high performance with low computational overhead, making them suitable for real-time applications but require decryption before data processing. Homomorphic encryption enables computation on encrypted data without decryption, enhancing security but significantly increases computational complexity and latency. The trade-off between these encryption schemes revolves around balancing data privacy with system performance and resource utilization.
Real-World Use Cases and Applications
Traditional encryption secures data at rest and in transit, making it ideal for applications like secure file storage, email protection, and VPN communications where data must be decrypted before processing. Homomorphic encryption enables computation on encrypted data without decryption, enhancing privacy in sensitive fields such as healthcare analytics, financial services, and cloud computing by allowing encrypted data to be processed securely. Enterprises leveraging secure multi-party computation and privacy-preserving machine learning increasingly adopt homomorphic encryption to comply with stringent data privacy regulations like GDPR and HIPAA.
Scalability and Integration Challenges
Traditional encryption methods face scalability limitations due to the need for decryption before processing data, which introduces latency and inefficiency in large-scale systems. Homomorphic encryption enables computation on encrypted data without decryption, enhancing data privacy but imposes significant computational overhead and complexity in integration with existing infrastructures. Overcoming these challenges requires advancements in algorithm optimization and seamless compatibility with current software frameworks to achieve practical scalability.
Regulatory Compliance and Privacy Considerations
Traditional encryption secures data at rest and in transit, meeting many regulatory standards like GDPR and HIPAA by restricting unauthorized access but requires decryption for processing, exposing data to potential risks. Homomorphic encryption allows computation on encrypted data without decryption, enhancing privacy preservation and reducing compliance risks by ensuring sensitive information remains protected throughout processing. Regulatory frameworks increasingly recognize homomorphic encryption's potential to maintain data confidentiality while enabling secure analytics and machine learning on encrypted datasets.
Future Trends in Encryption Technologies
Traditional encryption relies on data being decrypted before processing, posing security risks in cloud computing and data analytics environments. Homomorphic encryption enables computation on encrypted data without decryption, offering enhanced privacy and security critical for future applications in secure multi-party computations and privacy-preserving machine learning. Advances in quantum-resistant algorithms and hardware acceleration are driving the adoption of homomorphic encryption in enterprise and government sectors, signaling a paradigm shift in encryption technologies.
Choosing the Right Encryption Solution
Traditional encryption techniques prioritize data security during storage and transmission by converting plaintext into ciphertext, but require decryption before processing, which exposes data to potential vulnerabilities. Homomorphic encryption allows computation on encrypted data without decryption, enabling secure data analysis and processing in cloud environments while preserving privacy. Selecting the right encryption solution depends on balancing performance, security requirements, and operational complexity, with homomorphic encryption suited for sensitive, compliant workloads needing computation on encrypted data and traditional encryption optimal for efficient, high-speed data protection.
Related Important Terms
Data-at-Rest Encryption
Traditional encryption secures data-at-rest by converting plaintext into ciphertext using symmetric or asymmetric keys, requiring decryption before processing, which exposes information risk during computation. Homomorphic encryption enables direct computation on encrypted data without decryption, maintaining data confidentiality throughout processing and significantly enhancing security for sensitive data-at-rest scenarios.
Data-in-Use Encryption
Traditional encryption secures data primarily at rest and in transit, leaving data vulnerable when actively processed, whereas homomorphic encryption enables computations directly on encrypted data without decryption, ensuring continuous protection during data-in-use. This capability is critical for sensitive applications in cloud computing and privacy-preserving analytics, where maintaining confidentiality throughout processing is paramount.
End-to-End Encryption
End-to-end encryption (E2EE) ensures data remains encrypted during transmission and storage, but traditional encryption requires data to be decrypted for processing, exposing vulnerabilities. Homomorphic encryption enables computations on encrypted data without decryption, maintaining confidentiality throughout processing and enhancing security in end-to-end encrypted systems.
Fully Homomorphic Encryption (FHE)
Fully Homomorphic Encryption (FHE) enables computations on encrypted data without decryption, preserving confidentiality throughout processing, unlike traditional encryption which requires data to be decrypted before computation. This advancement in cryptography supports secure cloud computing and privacy-preserving data analysis, overcoming limitations of classical methods by maintaining data protection in active use.
Partially Homomorphic Encryption (PHE)
Partially Homomorphic Encryption (PHE) enables specific algebraic operations on ciphertexts, such as addition or multiplication, without decrypting the data, enhancing secure data processing in cloud computing environments. Unlike traditional encryption, which requires decryption before computation, PHE allows selective operations on encrypted data, improving efficiency and privacy in applications like secure voting and private query processing.
Multi-Key Homomorphic Encryption
Traditional encryption secures data by requiring decryption for computation, exposing sensitive information during processing, whereas multi-key homomorphic encryption enables multiple users to perform joint computations on encrypted data without revealing individual plaintexts. This advanced cryptographic technique facilitates collaborative data analysis while preserving privacy across distributed systems, enhancing security in cloud computing and multi-party scenarios.
Ciphertext Manipulation
Traditional encryption requires decryption before performing any operations on data, exposing plaintext vulnerabilities, whereas homomorphic encryption allows direct computations on ciphertext without decryption, preserving data privacy throughout processing. This capability enables secure data manipulation in cloud computing and outsourced environments, significantly reducing risks associated with data breaches during analysis.
Zero-Knowledge Proofs (ZKP)
Traditional encryption secures data by transforming plaintext into ciphertext requiring decryption keys for access, while homomorphic encryption enables computations directly on encrypted data without exposing the underlying information; Zero-Knowledge Proofs (ZKP) enhance both methods by allowing one party to prove knowledge of a secret without revealing the secret itself. Integrating ZKP with homomorphic encryption strengthens privacy-preserving protocols in sensitive applications like secure voting, confidential cloud computing, and blockchain verification by ensuring data integrity and authenticity without compromising confidentiality.
Lattice-Based Cryptography
Traditional encryption methods rely on well-established algorithms like RSA and AES, which encrypt data by transforming it into unreadable formats but require decryption for processing, posing risks in data privacy. Lattice-based cryptography, a cornerstone of homomorphic encryption, enables computations directly on encrypted data without decryption, enhancing security and supporting post-quantum resilience by leveraging hard mathematical problems in lattice structures.
Privacy-Preserving Computation
Traditional encryption secures data by transforming it into an unreadable format, but requires decryption for computation, exposing plaintext to potential breaches. Homomorphic encryption enables direct computation on encrypted data, preserving privacy by eliminating the need to decrypt, making it ideal for secure cloud computing and sensitive data processing.
Traditional Encryption vs Homomorphic Encryption Infographic
 industrydif.com
industrydif.com