VPNs provide remote users with encrypted access to a private network, but they often expose the entire network once connected, increasing security risks. Software Defined Perimeters (SDPs) create dynamic, per-request access controls that minimize attack surfaces by granting access only to authorized users and specific resources. This approach enhances security through granular segmentation and reduces vulnerabilities commonly associated with traditional VPNs.
Table of Comparison
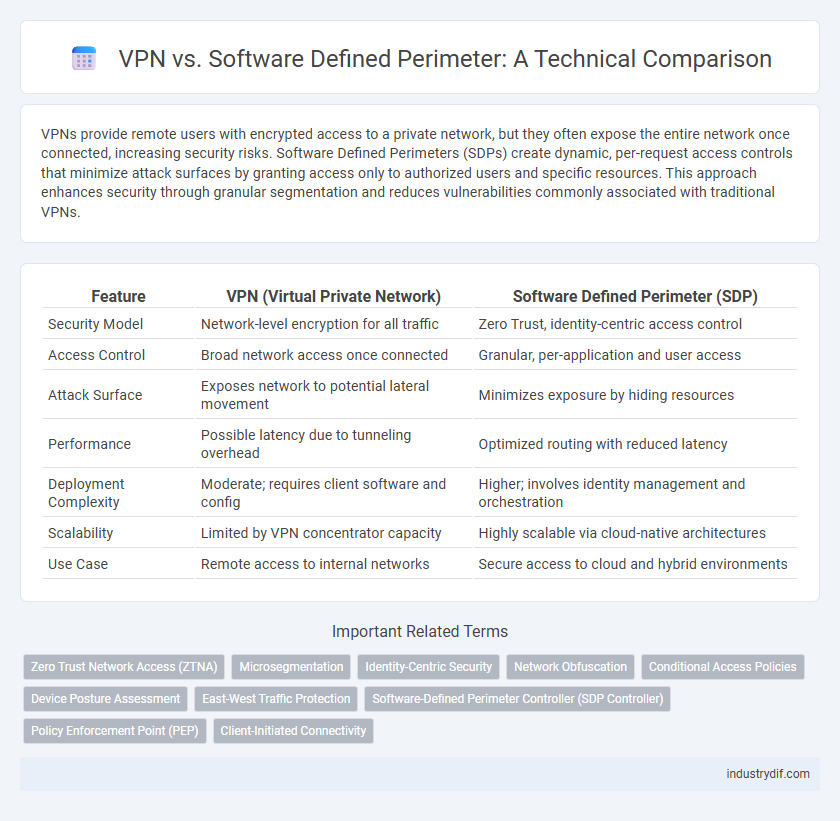
| Feature | VPN (Virtual Private Network) | Software Defined Perimeter (SDP) |
|---|---|---|
| Security Model | Network-level encryption for all traffic | Zero Trust, identity-centric access control |
| Access Control | Broad network access once connected | Granular, per-application and user access |
| Attack Surface | Exposes network to potential lateral movement | Minimizes exposure by hiding resources |
| Performance | Possible latency due to tunneling overhead | Optimized routing with reduced latency |
| Deployment Complexity | Moderate; requires client software and config | Higher; involves identity management and orchestration |
| Scalability | Limited by VPN concentrator capacity | Highly scalable via cloud-native architectures |
| Use Case | Remote access to internal networks | Secure access to cloud and hybrid environments |
Understanding VPN: Core Concepts and Functionality
VPNs establish encrypted tunnels between user devices and remote networks, ensuring secure data transmission across public internet channels. They utilize protocols such as IPsec or OpenVPN to authenticate users and maintain confidentiality, integrity, and availability of information. VPNs primarily focus on network-level access control, enabling users to connect to corporate resources as if they were physically on-site.
Introduction to Software Defined Perimeter (SDP)
Software Defined Perimeter (SDP) is a security framework that dynamically creates secure, encrypted connections between users and resources based on identity and context, minimizing exposure to cyber threats. Unlike traditional VPNs, SDP operates on a zero-trust model, ensuring that access is granted strictly on a need-to-know basis without exposing the entire network. SDP enhances security by leveraging software-based controls that isolate applications and infrastructure, reducing the attack surface and improving overall network resiliency.
Architecture Comparison: VPN vs SDP
VPN architecture relies on a traditional client-server model where remote users connect through a secure tunnel to access the entire network, exposing a broad attack surface. Software Defined Perimeter (SDP) uses a zero-trust model, dynamically creating one-to-one connections between users and authorized resources, minimizing exposure and reducing lateral movement risks. SDP architecture decouples access control from the network, providing granular, context-aware access that scales better in hybrid and cloud environments compared to VPN.
Security Mechanisms: VPN vs SDP
VPN security mechanisms rely on encrypted tunnels using IPsec or SSL/TLS protocols to protect data in transit but often expose the network perimeter to potential lateral movement once access is granted. Software Defined Perimeter (SDP) employs a zero-trust model with dynamic, identity-based micro-segmentation and perimeter cloaking, drastically reducing attack surfaces and preventing unauthorized access by making resources invisible to malicious actors. Unlike VPNs, SDP continuously verifies user and device credentials before granting access, enhancing protection against insider threats and lateral attacks.
Access Control Methods in VPN and SDP
VPNs rely on network-layer access control, granting users broad network access after authentication, which can expose resources beyond the intended scope. Software Defined Perimeters (SDP) implement granular, application-layer access control by verifying user identity, device posture, and context before allowing access, minimizing attack surfaces. SDP enforces a zero-trust model with dynamic, least-privilege access, whereas VPNs often operate on implicit trust once the connection is established.
Scalability and Performance Considerations
VPN solutions often face scalability challenges due to increased latency and bandwidth constraints as user connections grow, impacting overall network performance. Software Defined Perimeters (SDP) utilize dynamic, identity-based access controls and on-demand provisioning, enabling more efficient resource allocation and improved scalability in large distributed environments. SDP architectures typically enhance performance by minimizing attack surfaces and reducing the need for constant tunnel maintenance, resulting in optimized network throughput and lower latency compared to traditional VPNs.
Deployment Models: Cloud, On-Premises, and Hybrid
VPNs traditionally rely on on-premises deployment, requiring physical infrastructure and manual configuration, while Software Defined Perimeter (SDP) solutions excel in cloud-native and hybrid environments by dynamically provisioning secure access based on identity and context. SDP's architecture supports seamless integration with cloud platforms like AWS, Azure, and Google Cloud, enabling zero-trust security models without exposing the network perimeter. Hybrid deployment of SDP enhances scalability and flexibility by combining on-premises security controls with cloud-based policy enforcement, outperforming classic VPNs in agility and reduced attack surfaces.
Compliance and Regulatory Impact
VPNs often face challenges meeting stringent compliance requirements due to their broad network access and limited visibility, increasing risks in regulated environments such as HIPAA and GDPR. Software Defined Perimeters (SDPs) offer granular access controls and continuous authentication, aligning more effectively with regulatory frameworks by minimizing attack surfaces and ensuring strict user verification. Implementing SDPs enhances compliance posture through dynamic policy enforcement and comprehensive audit trails essential for regulatory audits.
Use Cases: When to Choose VPN or SDP
VPNs are ideal for remote workers requiring secure access to an entire corporate network with consistent performance across various internet connections. Software Defined Perimeters (SDP) are better suited for organizations needing granular, context-aware access control, minimizing attack surfaces by allowing user access only to specific applications based on identity and device compliance. Enterprises prioritizing zero-trust security architectures and dynamic access management benefit from SDP, while those with simpler, broad access needs often rely on traditional VPNs.
Future Trends in Secure Remote Access Solutions
Software Defined Perimeter (SDP) is rapidly surpassing traditional VPNs by offering enhanced security through dynamic, identity-centric access controls and micro-segmentation. Future trends emphasize zero trust architecture integration, AI-driven threat detection, and seamless scalability to accommodate hybrid workforces and cloud environments. Innovations in SDP aim to minimize attack surfaces and optimize user experience, positioning it as the preferred solution for next-generation secure remote access.
Related Important Terms
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) enhances security by granting access based on user identity and device posture rather than broad network access, contrasting traditional VPNs that create extensive network access once authenticated. Software Defined Perimeter (SDP) technologies utilize ZTNA principles to create dynamic, context-aware, and least-privilege access environments, minimizing attack surfaces compared to the static access model of VPNs.
Microsegmentation
Software Defined Perimeter (SDP) enhances security through microsegmentation by isolating network segments and enforcing granular access controls, reducing the attack surface more effectively than traditional VPNs, which provide broader network access. Microsegmentation in SDP dynamically adapts to user identity, device posture, and application context, enabling precise policy enforcement that traditional VPNs lack.
Identity-Centric Security
Software Defined Perimeter (SDP) offers superior identity-centric security compared to traditional VPNs by dynamically granting access based on verified user identity and device posture rather than broad network-level access. This granular control reduces attack surfaces and prevents unauthorized lateral movement within networks, enhancing protection for sensitive data and critical applications.
Network Obfuscation
Software Defined Perimeter (SDP) enhances network obfuscation by dynamically creating one-to-one network connections, effectively hiding internal infrastructure from unauthorized users, unlike traditional VPNs which often expose entire network segments once connected. VPNs rely on broad access tunnels that can be detected and targeted, whereas SDPs use identity-based access and encrypted micro-tunnels to minimize attack surfaces and prevent network reconnaissance.
Conditional Access Policies
VPNs primarily use static network access controls, while Software Defined Perimeters (SDPs) enforce dynamic Conditional Access Policies based on real-time user identity, device posture, and context. SDP's granular access management significantly reduces attack surfaces by granting least-privilege access only when specific conditions are met.
Device Posture Assessment
VPNs primarily provide encrypted network access but lack integrated device posture assessment, leaving endpoint security verification to separate tools. Software Defined Perimeters (SDPs) incorporate real-time device posture assessment, dynamically enforcing access controls based on the security status of endpoints before granting network entry.
East-West Traffic Protection
Software Defined Perimeter (SDP) offers superior East-West traffic protection by dynamically enforcing identity-based access controls within data centers, reducing lateral movement risks compared to traditional VPNs that predominantly secure North-South traffic. Unlike VPNs, SDP segments internal network access, ensures encrypted micro-segmentation, and mitigates insider threats by restricting resource visibility based on user authentication and device posture.
Software-Defined Perimeter Controller (SDP Controller)
The Software-Defined Perimeter Controller (SDP Controller) serves as the central authentication and authorization hub in SDP architecture, dynamically granting access based on user identity and device posture rather than network location. Unlike traditional VPNs that provide broad network access, the SDP Controller ensures granular, context-aware security policies, reducing attack surfaces and preventing unauthorized lateral movement within the network.
Policy Enforcement Point (PEP)
The Policy Enforcement Point (PEP) in a Software Defined Perimeter (SDP) dynamically enforces granular access controls based on identity, device posture, and real-time risk assessment, contrasting with traditional VPNs that rely on static access rules and broad network-level trust. SDP's PEP minimizes attack surfaces by ensuring zero-trust principles, only granting access to specific resources after continuous verification.
Client-Initiated Connectivity
VPNs establish client-initiated connectivity by creating encrypted tunnels directly between the user device and the corporate network, often exposing the network perimeter to broader access risks. In contrast, Software Defined Perimeters use identity-based, client-initiated connections that dynamically create secure, micro-segmented access paths, minimizing attack surfaces and enhancing security posture by ensuring users connect only to authorized services.
VPN vs Software Defined Perimeter Infographic
 industrydif.com
industrydif.com