Networking establishes the foundational infrastructure for device communication and data exchange across systems, enabling connectivity and resource sharing. Zero Trust redefines security principles by enforcing strict identity verification, continuous monitoring, and least-privilege access regardless of network location. Integrating Zero Trust with traditional networking enhances protection against modern cyber threats by minimizing attack surfaces and validating every access request within the network environment.
Table of Comparison
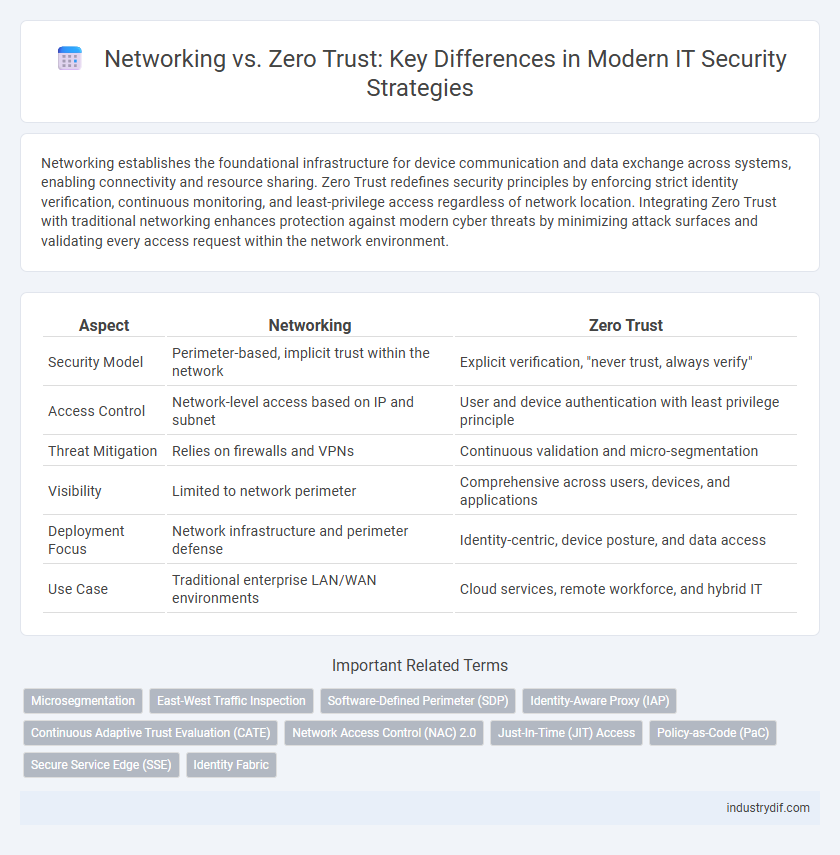
| Aspect | Networking | Zero Trust |
|---|---|---|
| Security Model | Perimeter-based, implicit trust within the network | Explicit verification, "never trust, always verify" |
| Access Control | Network-level access based on IP and subnet | User and device authentication with least privilege principle |
| Threat Mitigation | Relies on firewalls and VPNs | Continuous validation and micro-segmentation |
| Visibility | Limited to network perimeter | Comprehensive across users, devices, and applications |
| Deployment Focus | Network infrastructure and perimeter defense | Identity-centric, device posture, and data access |
| Use Case | Traditional enterprise LAN/WAN environments | Cloud services, remote workforce, and hybrid IT |
Understanding Traditional Networking Models
Traditional networking models rely on perimeter-based security, assuming that internal networks are inherently trustworthy and external networks are hostile. These models typically enforce access control through firewalls and VPNs, which create a defined boundary between trusted and untrusted zones. However, this approach struggles with modern challenges like remote work, cloud adoption, and insider threats, highlighting limitations in securing diverse and dynamic environments.
Key Principles of Zero Trust Architecture
Zero Trust Architecture eliminates implicit trust by enforcing strict identity verification for every device and user attempting to access network resources. It hinges on the principles of least privilege access, continuous monitoring, and micro-segmentation to minimize attack surfaces and contain breaches. This approach contrasts with traditional networking models that rely heavily on perimeter-based security and implicit trust within the network boundary.
Security Challenges in Legacy Network Environments
Legacy network environments face significant security challenges due to outdated perimeter-based defenses that struggle to address modern threats such as insider attacks and lateral movement. Traditional networking models lack granular access control and continuous verification, making them vulnerable to breached credentials and advanced persistent threats (APTs). Zero Trust architecture mitigates these risks by enforcing strict identity verification, micro-segmentation, and least-privilege access, fundamentally transforming security posture in complex network ecosystems.
Core Components of Zero Trust Security
Core components of Zero Trust security include continuous authentication, strict access controls, and micro-segmentation, which ensure that trust is never assumed regardless of network location. Unlike traditional networking models that rely on perimeter defenses, Zero Trust enforces verification of every user and device before granting access to resources. This approach minimizes attack surfaces and prevents lateral movement by isolating sensitive data and enforcing least privilege principles throughout the environment.
Authentication and Access Control: Networking vs Zero Trust
Traditional networking relies on perimeter-based authentication and access control, granting users broad access once inside the network boundary. Zero Trust enforces strict identity verification for every access request, regardless of location, using continuous authentication and granular access policies. This shift reduces lateral movement risks and improves security by limiting access to only what is explicitly authorized.
Segmentation Strategies: VLANs vs Micro-Segmentation
VLANs provide network segmentation by isolating traffic at the Layer 2 level, offering basic separation of network segments based on physical or logical groupings. Micro-segmentation, a core principle of Zero Trust architecture, enforces granular security policies at the workload level, enabling dynamic, context-aware control over east-west traffic within data centers and cloud environments. While VLANs reduce broadcast domains and improve traffic management, micro-segmentation enhances security posture by minimizing attack surfaces through precise, application-aware isolation.
Impact on User Experience and Productivity
Networking architectures often prioritize connectivity and bandwidth, which can lead to faster access but may expose users to security risks, negatively impacting user trust and productivity in case of breaches. Zero Trust models enforce strict identity verification and continuous monitoring, reducing unauthorized access while potentially introducing latency or complexity that can affect seamless user experience. Balancing real-time authentication with optimized network performance is crucial for maintaining productivity without compromising security in enterprise environments.
Implementation Considerations and Best Practices
Implementing networking solutions alongside Zero Trust frameworks requires meticulous segmentation and continuous verification of all users and devices to minimize attack surfaces. Best practices include enforcing least privilege access, deploying multi-factor authentication, and integrating real-time monitoring to detect and respond to anomalies swiftly. Ensuring compatibility between existing network infrastructure and Zero Trust policies is critical for seamless operation and enhanced security posture.
Comparing Regulatory Compliance: Networking and Zero Trust
Networking architectures often face challenges meeting evolving regulatory compliance standards due to traditional perimeter-based security models that can be bypassed by sophisticated threats. Zero Trust frameworks enforce strict identity verification and least-privilege access controls, aligning more effectively with regulations such as GDPR, HIPAA, and PCI-DSS by minimizing attack surfaces and ensuring continuous authentication. Organizations adopting Zero Trust can achieve higher compliance levels through granular policy enforcement, real-time monitoring, and comprehensive audit trails.
Future Trends in Network Security Evolution
Future trends in network security emphasize a shift from traditional perimeter-based networking to Zero Trust architectures, which enforce strict identity verification regardless of location. Zero Trust models leverage continuous monitoring, micro-segmentation, and adaptive access controls to mitigate emerging threats in increasingly complex hybrid cloud environments. Advances in AI-driven threat detection and automated response are accelerating this evolution, enhancing resilience against sophisticated cyberattacks.
Related Important Terms
Microsegmentation
Microsegmentation enhances network security by dividing the network into granular segments, limiting lateral movement and reducing attack surfaces compared to traditional flat networking architectures. Zero Trust architecture integrates microsegmentation to enforce strict identity verification and access controls at each segment, ensuring continuous validation and minimizing threats.
East-West Traffic Inspection
East-West traffic inspection in networking emphasizes internal data flow analysis, contrasting with Zero Trust architecture that enforces strict identity verification and micro-segmentation to prevent lateral movement of threats. Implementing Zero Trust for East-West traffic enhances visibility and security by continuously validating every access request within the network, reducing the risk of internal breaches.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) enhances network security by creating dynamic, context-aware access controls that isolate resources and verify users before granting connectivity, effectively minimizing attack surfaces compared to traditional network security models. Unlike conventional networking, SDP enforces Zero Trust principles by continuously authenticating and authorizing every connection attempt based on identity, device posture, and real-time risk assessment.
Identity-Aware Proxy (IAP)
Identity-Aware Proxy (IAP) revolutionizes network security by enforcing granular access controls based on user identity and context, eliminating traditional perimeter-based vulnerabilities. Unlike conventional networking models that rely on static IP-based access, IAP dynamically verifies identity and device trustworthiness to enable secure, scalable zero trust architectures.
Continuous Adaptive Trust Evaluation (CATE)
Continuous Adaptive Trust Evaluation (CATE) revolutionizes networking security by dynamically assessing user and device trustworthiness in real-time, unlike traditional static network perimeter defenses. This ongoing, context-aware verification model enhances Zero Trust frameworks by minimizing risks through perpetual validation of identities, behaviors, and compliance within network environments.
Network Access Control (NAC) 2.0
Network Access Control (NAC) 2.0 integrates advanced identity verification, device posture assessment, and real-time analytics to enforce granular security policies, surpassing traditional networking models by enabling dynamic, context-aware access control. Zero Trust architecture complements NAC 2.0 by eliminating implicit trust within network perimeters, ensuring that every access request undergoes continuous authentication and authorization regardless of location.
Just-In-Time (JIT) Access
Just-In-Time (JIT) Access in Zero Trust architecture minimizes network exposure by granting temporary, time-bound permissions based on real-time validation, contrasting with traditional persistent network access models. This approach enhances security posture by reducing the attack surface and limiting lateral movement within the infrastructure.
Policy-as-Code (PaC)
Policy-as-Code (PaC) enhances Zero Trust security by enabling automated, programmable policies that enforce granular access controls across dynamic network environments, reducing manual errors and accelerating compliance. Unlike traditional networking security models reliant on static perimeter defenses, PaC in Zero Trust facilitates continuous validation and real-time policy updates, ensuring adaptive protection tailored to evolving threat landscapes.
Secure Service Edge (SSE)
Secure Service Edge (SSE) integrates Zero Trust principles with cloud-delivered networking to provide continuous, identity-driven security across all user access points, eliminating reliance on traditional perimeter-based security models. Unlike conventional networking, SSE enforces granular access controls, real-time threat protection, and data loss prevention by dynamically verifying trust for each service request regardless of user location or device.
Identity Fabric
Networking frameworks traditionally emphasize perimeter security, whereas Zero Trust architecture centers on continuous identity verification through an advanced Identity Fabric that integrates user, device, and application contexts for granular access control. Leveraging Identity Fabric enables dynamic policy enforcement and real-time risk assessment, ensuring secure resource access regardless of network location or device trust level.
Networking vs Zero Trust Infographic
 industrydif.com
industrydif.com