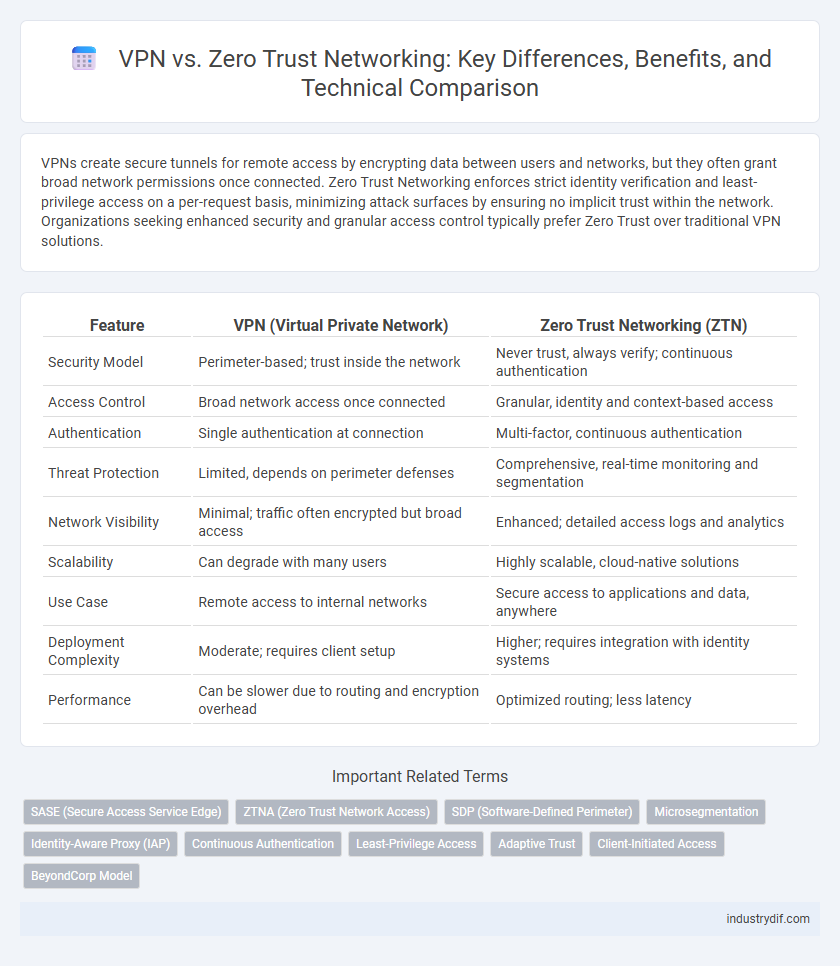
VPNs create secure tunnels for remote access by encrypting data between users and networks, but they often grant broad network permissions once connected. Zero Trust Networking enforces strict identity verification and least-privilege access on a per-request basis, minimizing attack surfaces by ensuring no implicit trust within the network. Organizations seeking enhanced security and granular access control typically prefer Zero Trust over traditional VPN solutions.
Table of Comparison
| Feature | VPN (Virtual Private Network) | Zero Trust Networking (ZTN) |
|---|---|---|
| Security Model | Perimeter-based; trust inside the network | Never trust, always verify; continuous authentication |
| Access Control | Broad network access once connected | Granular, identity and context-based access |
| Authentication | Single authentication at connection | Multi-factor, continuous authentication |
| Threat Protection | Limited, depends on perimeter defenses | Comprehensive, real-time monitoring and segmentation |
| Network Visibility | Minimal; traffic often encrypted but broad access | Enhanced; detailed access logs and analytics |
| Scalability | Can degrade with many users | Highly scalable, cloud-native solutions |
| Use Case | Remote access to internal networks | Secure access to applications and data, anywhere |
| Deployment Complexity | Moderate; requires client setup | Higher; requires integration with identity systems |
| Performance | Can be slower due to routing and encryption overhead | Optimized routing; less latency |
Understanding VPN: Core Concepts and Usage
Virtual Private Network (VPN) technology establishes secure, encrypted tunnels between remote users and corporate networks, ensuring confidentiality and data integrity during transmission. VPNs rely on perimeter-based security models, granting access based on network location rather than continuous verification of user or device trustworthiness. Commonly used for remote access, VPNs can introduce risks such as broad network access and insufficient granular control compared to Zero Trust Networking models.
Zero Trust Networking: Principles and Framework
Zero Trust Networking operates on the principle of "never trust, always verify," requiring continuous authentication and strict access controls regardless of user location. Its framework segments networks into microperimeters, enforcing granular policies based on user identity, device posture, and real-time risk assessment. This model significantly reduces attack surfaces compared to traditional VPN solutions by limiting lateral movement and enforcing least-privilege access throughout the network.
Key Technical Differences Between VPN and Zero Trust
VPNs create encrypted tunnels granting network-wide access based on a single point of authentication, often leading to implicit trust within the network perimeter. Zero Trust Networking enforces granular, least-privilege access controls using continuous verification of user identity, device posture, and contextual data for every access request. Unlike VPNs, Zero Trust eliminates implicit trust by segmenting resources and leveraging adaptive security policies to reduce attack surfaces and lateral movement risks.
Authentication Methods: VPN vs. Zero Trust
VPNs primarily rely on single-factor authentication such as passwords or pre-shared keys, which can expose networks to risks if credentials are compromised. Zero Trust Networking employs multi-factor authentication (MFA) and continuous verification, ensuring that user identity and device posture are validated dynamically before granting access. This granular approach significantly enhances security by minimizing the attack surface compared to traditional VPN authentication methods.
Network Access Control Mechanisms
VPNs rely on perimeter-based access control, granting broad network access after user authentication, which can expose internal resources to lateral threats. Zero Trust Networking employs granular network access control mechanisms, continuously verifying user identity and device posture before permitting access to specific applications or data. This shift enhances security by minimizing attack surfaces and enforcing least-privilege principles within dynamic, context-aware environments.
Scalability and Flexibility in Modern Environments
VPNs often struggle with scalability due to limited capacity and complex management as user numbers increase, whereas Zero Trust Networking (ZTN) offers enhanced scalability by leveraging cloud-native architectures and granular access controls. ZTN enables flexible policy enforcement tailored to dynamic, distributed workforces, improving security posture without compromising performance. The adaptive nature of Zero Trust frameworks aligns better with modern, hybrid cloud environments, facilitating seamless integration and real-time threat response.
Security Posture: Threat Mitigation Comparison
Zero Trust Networking enforces strict identity verification and micro-segmentation, significantly reducing attack surfaces compared to traditional VPNs that grant broad network access once connected. VPNs often expose internal resources to lateral movement risks if credentials are compromised, while Zero Trust continuously verifies user and device trustworthiness at each access request. Implementing Zero Trust enhances security posture by minimizing threats such as unauthorized access, insider threats, and advanced persistent threats through dynamic policy enforcement and real-time risk assessment.
Performance and Latency Implications
VPNs often introduce higher latency due to the overhead of tunneling and encrypting all network traffic, impacting real-time applications and overall performance. Zero Trust Networking minimizes performance degradation by applying granular, identity-based access controls that reduce unnecessary data routing through central gateways. This approach enables faster packet forwarding and lower latency, improving user experience and operational efficiency in distributed environments.
Implementation Challenges and Best Practices
Implementing VPNs often faces challenges like managing broad network access and securing endpoints, whereas Zero Trust Networking requires granular identity verification and continuous monitoring across all access points. Best practices for VPNs include enforcing strong authentication and endpoint security, while Zero Trust demands micro-segmentation, adaptive access controls, and real-time analytics for threat detection. Both approaches benefit from integrating multi-factor authentication (MFA) and comprehensive monitoring to enhance overall security posture.
Future Trends in Secure Network Architecture
Future trends in secure network architecture emphasize the shift from traditional VPNs to Zero Trust Networking, leveraging continuous verification and micro-segmentation for enhanced security. Zero Trust models reduce attack surfaces by strictly enforcing access controls based on user identity, device posture, and real-time risk assessments. Integration of AI-driven threat detection and cloud-native security frameworks positions Zero Trust as the dominant paradigm for scalable, adaptive cybersecurity in evolving enterprise environments.
Related Important Terms
SASE (Secure Access Service Edge)
SASE (Secure Access Service Edge) integrates VPN capabilities with Zero Trust Networking principles to deliver secure, cloud-native access by enforcing identity-driven policies and continuous verification for every user and device. Unlike traditional VPNs that grant broad network access, SASE's Zero Trust model minimizes attack surfaces by providing least-privilege access and real-time threat protection across distributed cloud environments.
ZTNA (Zero Trust Network Access)
Zero Trust Network Access (ZTNA) offers enhanced security by verifying every user and device continuously before granting access, unlike traditional VPNs that provide broad network access once connected. ZTNA reduces risk by enforcing least privilege access policies and minimizing attack surfaces in modern, cloud-centric IT environments.
SDP (Software-Defined Perimeter)
Software-Defined Perimeter (SDP) enhances Zero Trust Networking by dynamically creating secure, encrypted connections that limit access to authorized users and devices, reducing attack surfaces compared to traditional VPNs. SDP integrates identity verification and continuous trust assessment, ensuring granular access control and minimizing exposure in hybrid and cloud environments.
Microsegmentation
Microsegmentation within Zero Trust Networking enables granular security controls by dividing networks into isolated segments, reducing attack surfaces significantly compared to traditional VPNs that provide broad, perimeter-based access. This approach enforces strict access policies at the workload level, ensuring that users and devices can only communicate with authorized resources, enhancing threat containment and minimizing lateral movement risks.
Identity-Aware Proxy (IAP)
Identity-Aware Proxy (IAP) enhances security by enforcing granular user identity verification and access policies, contrasting with traditional VPNs that grant broad network access after initial authentication. IAP minimizes attack surfaces by dynamically controlling application-level access based on user credentials and device posture, aligning with Zero Trust Networking principles for continuous trust assessment.
Continuous Authentication
Zero Trust Networking leverages continuous authentication by constantly verifying user identity and device integrity throughout the session, unlike traditional VPNs that rely on a one-time access verification. This persistent validation reduces the risk of unauthorized access and lateral movement within the network, enhancing overall security posture.
Least-Privilege Access
Zero Trust Networking enforces least-privilege access by continuously validating user identities and device health before granting minimal necessary permissions, reducing attack surfaces compared to traditional VPNs that often provide broad network access once connected. Unlike VPNs, which rely on perimeter-based security, Zero Trust applies granular access controls at every request, ensuring that users only access resources essential to their roles.
Adaptive Trust
Adaptive Trust in Zero Trust Networking continuously evaluates user identity and device posture to grant precise, least-privilege access based on real-time risk assessment, unlike traditional VPNs that often provide broad, static access once connected. This dynamic approach reduces attack surfaces by enforcing granular access controls and minimizing implicit trust inherent in VPN connections.
Client-Initiated Access
VPN relies on client-initiated access by establishing a secure tunnel between the user device and the corporate network, typically granting broad internal access once connected. Zero Trust Networking enforces strict identity verification and least-privilege access for every request, ensuring client-initiated connections only access specific resources based on continuous authentication and context-aware policies.
BeyondCorp Model
BeyondCorp Model shifts security from traditional VPN-based perimeter defenses to a zero trust networking approach by verifying user identity and device health before granting access to corporate resources. This model eliminates implicit trust within the network, enforcing granular access controls regardless of user location, thereby enhancing security postures against lateral threats.
VPN vs Zero Trust Networking Infographic
 industrydif.com
industrydif.com