Cybersecurity encompasses a broad range of practices designed to protect networks, devices, and data from unauthorized access and attacks. Zero Trust Architecture specifically implements the principle of "never trust, always verify," enforcing strict identity verification for every user and device attempting to access resources, regardless of their location. This approach enhances traditional cybersecurity by minimizing trust assumptions and reducing the risk of internal and external threats.
Table of Comparison
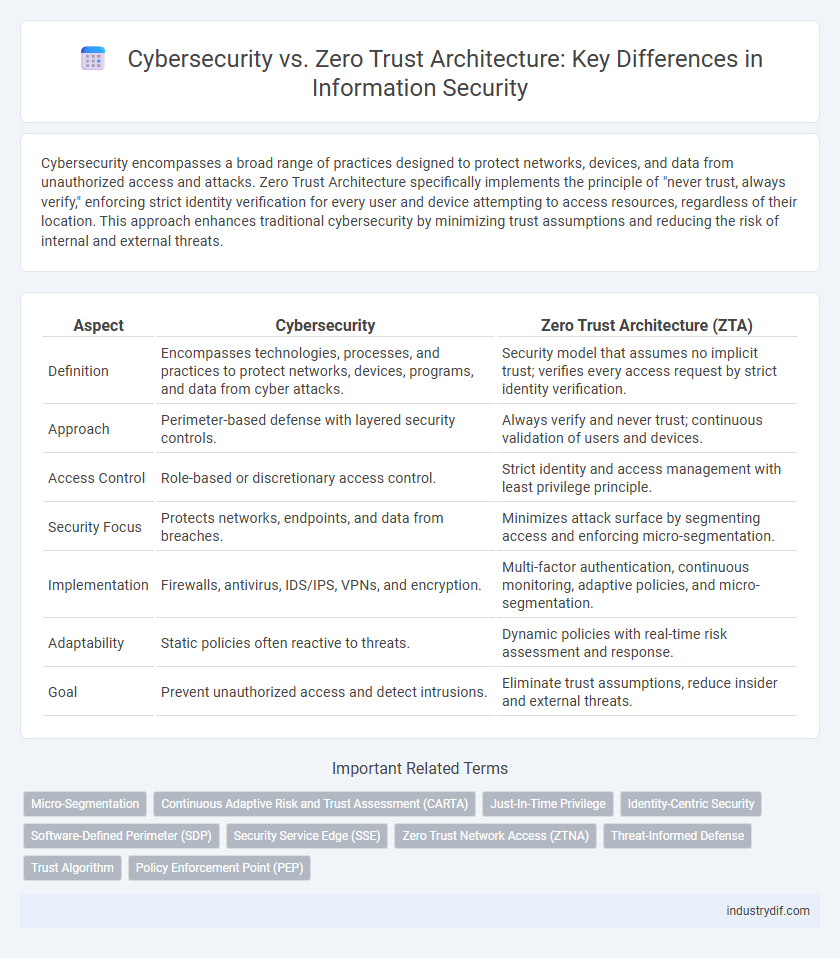
| Aspect | Cybersecurity | Zero Trust Architecture (ZTA) |
|---|---|---|
| Definition | Encompasses technologies, processes, and practices to protect networks, devices, programs, and data from cyber attacks. | Security model that assumes no implicit trust; verifies every access request by strict identity verification. |
| Approach | Perimeter-based defense with layered security controls. | Always verify and never trust; continuous validation of users and devices. |
| Access Control | Role-based or discretionary access control. | Strict identity and access management with least privilege principle. |
| Security Focus | Protects networks, endpoints, and data from breaches. | Minimizes attack surface by segmenting access and enforcing micro-segmentation. |
| Implementation | Firewalls, antivirus, IDS/IPS, VPNs, and encryption. | Multi-factor authentication, continuous monitoring, adaptive policies, and micro-segmentation. |
| Adaptability | Static policies often reactive to threats. | Dynamic policies with real-time risk assessment and response. |
| Goal | Prevent unauthorized access and detect intrusions. | Eliminate trust assumptions, reduce insider and external threats. |
Understanding Cybersecurity Fundamentals
Cybersecurity fundamentals encompass protecting systems, networks, and data from unauthorized access, attacks, and damage through practices like risk management, threat detection, and incident response. Zero Trust Architecture (ZTA) is a cybersecurity model that enforces strict identity verification for every person and device attempting to access resources, regardless of their location within or outside the network perimeter. Understanding cybersecurity basics aids in implementing Zero Trust principles effectively, ensuring comprehensive protection against evolving cyber threats.
What is Zero Trust Architecture?
Zero Trust Architecture is a cybersecurity framework that operates on the principle of "never trust, always verify," requiring strict identity verification for every user and device attempting to access resources, regardless of their location within or outside the network perimeter. It minimizes security risks by segmenting networks, enforcing least privilege access, and continuously monitoring and validating user activities. This approach effectively mitigates cyber threats like insider attacks, data breaches, and lateral movement within the network.
Key Differences Between Traditional Cybersecurity and Zero Trust
Traditional cybersecurity relies on perimeter-based defenses and assumes trust within the network, whereas Zero Trust Architecture enforces strict verification for every access request regardless of location. Zero Trust operates on the principle of "never trust, always verify," using continuous authentication, micro-segmentation, and least-privilege access controls to minimize attack surfaces. This proactive approach contrasts with reactive traditional models, enhancing security against modern threats such as insider attacks and advanced persistent threats (APTs).
Benefits of Adopting Zero Trust Principles
Zero Trust Architecture enhances cybersecurity by strictly verifying every user and device before granting access, reducing the risk of unauthorized breaches. It minimizes attack surfaces through continuous monitoring and adaptive access controls, ensuring sensitive data remains protected. Organizations adopting Zero Trust principles experience improved threat detection, compliance, and reduced impact from insider threats.
Core Components of Zero Trust Architecture
Zero Trust Architecture centers on core components such as continuous verification, micro-segmentation, least privilege access, and multifactor authentication to enhance cybersecurity posture. It eliminates implicit trust by enforcing strict identity verification for every user and device attempting to access resources. Implementing these components reduces the risk of insider threats, lateral movement, and data breaches within enterprise networks.
Cybersecurity Challenges in Modern IT Environments
Cybersecurity challenges in modern IT environments stem from increasingly sophisticated cyber threats, complex network architectures, and the rapid adoption of cloud services. Traditional security models struggle to effectively protect against insider threats, lateral movement, and advanced persistent threats (APTs) due to their perimeter-focused design. Zero Trust Architecture addresses these challenges by enforcing continuous verification, least privilege access, and micro-segmentation, reducing the attack surface and improving threat detection and response.
Implementing Zero Trust: Best Practices
Implementing Zero Trust Architecture requires continuous monitoring of user activities and strict verification of access permissions to minimize security risks. Key best practices include segmenting networks, enforcing multi-factor authentication, and adopting least privilege access controls to prevent unauthorized access. Integration of automated threat detection tools enhances real-time response capabilities within the Zero Trust framework.
Zero Trust vs Perimeter-Based Security Models
Zero Trust Architecture eliminates implicit trust by continuously verifying every user and device attempting to access network resources, contrasting sharply with traditional perimeter-based security models that rely on a strong outer defense to keep threats out. Perimeter-based security assumes that entities inside the network are trustworthy, creating vulnerabilities once an attacker bypasses the outer defenses. By enforcing least-privilege access and micro-segmentation, Zero Trust significantly reduces the attack surface and limits lateral movement within the network.
Common Misconceptions About Zero Trust
Zero Trust Architecture is often misunderstood as solely a technology solution rather than a comprehensive security strategy that requires cultural shifts and continuous verification of user identities and devices. Many assume that implementing Zero Trust means eliminating all perimeter security, while in reality, it enhances existing defenses through micro-segmentation and strict access controls. Misconceptions also include the belief that Zero Trust is a one-time project, ignoring the ongoing monitoring and policy adjustments essential for effective protection against evolving cyber threats.
Future Trends in Cybersecurity and Zero Trust Adoption
Future trends in cybersecurity emphasize the widespread adoption of Zero Trust Architecture (ZTA), driven by the increasing complexity of cyber threats and the shift to cloud-native environments. Organizations are investing in continuous authentication, micro-segmentation, and AI-powered threat detection to enhance Zero Trust implementation. Advancements in automation and improved identity and access management (IAM) systems are critical for scaling Zero Trust frameworks to protect data across hybrid and multi-cloud infrastructures.
Related Important Terms
Micro-Segmentation
Micro-segmentation in Zero Trust Architecture enhances cybersecurity by dividing networks into isolated segments, limiting lateral movement of threats and enforcing granular access controls. This approach drastically reduces the attack surface compared to traditional perimeter-based security models, strengthening defense mechanisms against sophisticated cyberattacks.
Continuous Adaptive Risk and Trust Assessment (CARTA)
Continuous Adaptive Risk and Trust Assessment (CARTA) enhances cybersecurity by enabling dynamic, real-time evaluation of risk and trust levels within Zero Trust Architecture frameworks. This approach continuously monitors user behavior, device health, and network conditions to enforce precise, adaptive access controls that minimize security breaches.
Just-In-Time Privilege
Just-In-Time Privilege within Zero Trust Architecture minimizes attack surfaces by granting users temporary access only when necessary, enhancing overall cybersecurity resilience. This dynamic access control significantly reduces the risk associated with persistent privileges common in traditional cybersecurity models.
Identity-Centric Security
Zero Trust Architecture prioritizes identity-centric security by continuously verifying user identities and managing access permissions based on strict authentication and least-privilege principles. Unlike traditional cybersecurity models that assume trust within a network perimeter, Zero Trust enforces granular access controls across all users and devices, minimizing the risk of insider threats and lateral movement.
Software-Defined Perimeter (SDP)
Cybersecurity frameworks increasingly adopt Software-Defined Perimeter (SDP) technology within Zero Trust Architecture to enhance network security by dynamically controlling access based on identity verification and device posture. SDP reduces attack surfaces and prevents unauthorized access by creating encrypted, per-connection micro-perimeters that enforce strict authentication beyond traditional network boundaries.
Security Service Edge (SSE)
Security Service Edge (SSE) integrates cybersecurity functions such as secure web gateways, cloud access security brokers, and zero trust network access into a unified cloud-native service, enhancing the enforcement of Zero Trust Architecture principles by continuously verifying user identity and device posture. This approach mitigates risks associated with traditional perimeter-based security models by providing dynamic, context-aware access controls and real-time threat protection across all network edges.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) enhances cybersecurity by strictly verifying every user and device before granting access, eliminating implicit trust within the network. ZTNA integrates continuous authentication, micro-segmentation, and least-privilege principles to reduce attack surfaces and prevent lateral movement in modern enterprise environments.
Threat-Informed Defense
Cybersecurity strategies increasingly prioritize Threat-Informed Defense, integrating real-time threat intelligence to proactively identify and neutralize risks within Zero Trust Architecture frameworks. This approach enables continuous verification and granular access controls, minimizing attack surfaces by assuming no implicit trust and adapting defenses based on evolving threat landscapes.
Trust Algorithm
Cybersecurity relies on perimeter-based defenses, whereas Zero Trust Architecture employs a trust algorithm that continuously verifies every user and device before granting access. This algorithm uses contextual data such as user behavior, device health, and network status to dynamically enforce strict access controls, minimizing security risks.
Policy Enforcement Point (PEP)
The Policy Enforcement Point (PEP) in cybersecurity acts as a critical control mechanism that enforces access policies by validating user credentials and permissions before granting resource access. In Zero Trust Architecture, the PEP continuously monitors and verifies every access attempt, ensuring strict compliance with least-privilege principles and dynamic risk assessments to mitigate insider threats and unauthorized access.
Cybersecurity vs Zero Trust Architecture Infographic
 industrydif.com
industrydif.com