Information sovereignty refers to the control and governance over data as it is processed, stored, and utilized, emphasizing legal and ethical management. Data sovereignty specifically addresses the physical location of data storage and the jurisdictional laws that apply to it, ensuring data remains within designated national boundaries. Distinguishing between the two is crucial for organizations seeking compliance with privacy regulations and safeguarding sensitive information.
Table of Comparison
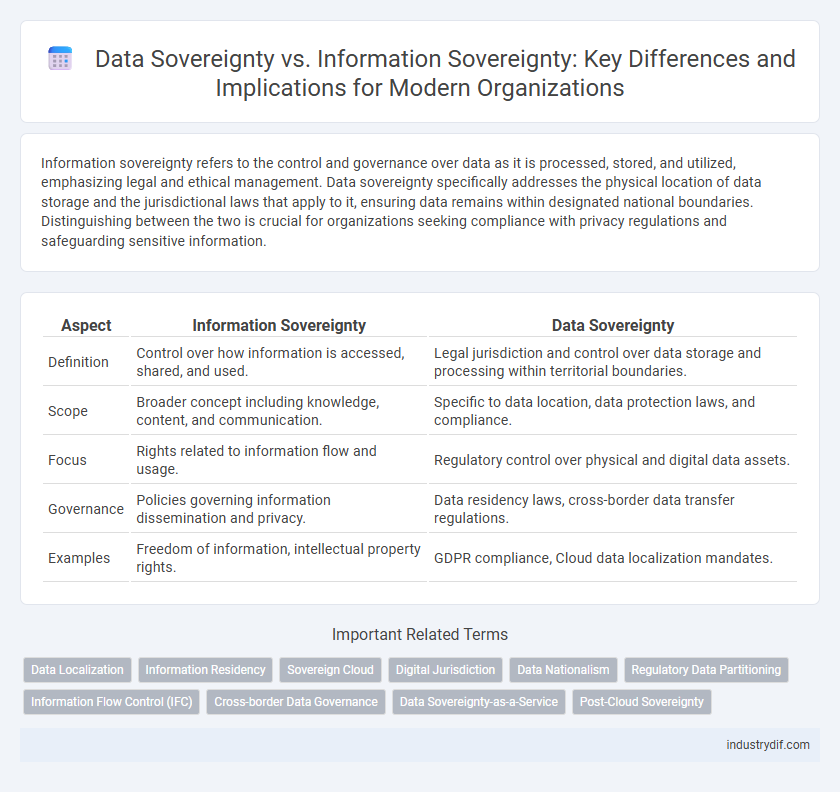
| Aspect | Information Sovereignty | Data Sovereignty |
|---|---|---|
| Definition | Control over how information is accessed, shared, and used. | Legal jurisdiction and control over data storage and processing within territorial boundaries. |
| Scope | Broader concept including knowledge, content, and communication. | Specific to data location, data protection laws, and compliance. |
| Focus | Rights related to information flow and usage. | Regulatory control over physical and digital data assets. |
| Governance | Policies governing information dissemination and privacy. | Data residency laws, cross-border data transfer regulations. |
| Examples | Freedom of information, intellectual property rights. | GDPR compliance, Cloud data localization mandates. |
Defining Information and Data Sovereignty
Information sovereignty refers to the control and governance over the creation, storage, and dissemination of information within a specific jurisdiction, ensuring data privacy, security, and compliance with local regulations. Data sovereignty specifically emphasizes the legal jurisdiction governing data, mandating that data is subject to the laws and policies of the country where it is collected or stored. Both concepts are critical in managing risk and protecting sensitive information in an increasingly digital and globalized environment.
Key Differences Between Information and Data Sovereignty
Information sovereignty emphasizes control over the creation, processing, and dissemination of meaningful content, ensuring privacy, security, and compliance with local regulations. Data sovereignty focuses specifically on the physical location and jurisdiction governing the storage and handling of raw data sets, highlighting legal accountability and protection measures. Key differences include that information sovereignty deals with contextual use and interpretation, while data sovereignty centers on legal ownership and geographical constraints of data.
Importance of Information Sovereignty in Modern Enterprises
Information sovereignty ensures that enterprises maintain control over their data, complying with legal and regulatory frameworks unique to each jurisdiction. Protecting data privacy and maintaining trust with customers are critical competitive advantages driven by robust information sovereignty policies. Enterprises leveraging information sovereignty optimize data governance, reducing risks associated with cross-border data transfers and cyber threats.
Legal Frameworks Impacting Data and Information Sovereignty
Legal frameworks such as the European Union's General Data Protection Regulation (GDPR) significantly shape data sovereignty by imposing strict requirements on data privacy, storage, and cross-border transfer. Information sovereignty extends beyond data sovereignty, encompassing the control over information processing, sharing, and governance within jurisdictional boundaries. National laws and international agreements influence both, mandating compliance to protect citizens' digital rights and ensure transparent data management practices.
Cross-Border Data Flow: Challenges and Risks
Cross-border data flow presents significant challenges and risks in the context of information and data sovereignty, as national regulations often impose strict controls on where and how data can be stored and transferred. Organizations must navigate complex legal frameworks, such as the EU's GDPR and similar laws in other jurisdictions, which prioritize protecting personal information while enabling data-driven innovation. Failure to comply with these regulations can lead to substantial penalties, data breaches, and loss of trust, emphasizing the critical need for robust data governance and sovereignty strategies.
Data Localization vs. Information Governance
Data sovereignty emphasizes the legal control and jurisdiction over data held within a country, requiring data localization to store and process data domestically. Information governance, however, focuses on the policies, standards, and procedures managing information lifecycle, ensuring compliance, security, and data quality regardless of physical data location. Balancing data localization with robust information governance frameworks enables organizations to meet regulatory requirements while optimizing data use across borders.
Industry-Specific Regulations and Compliance
Industry-specific regulations such as HIPAA for healthcare, GDPR for European data subjects, and FINRA for financial services enforce strict requirements on data sovereignty, mandating that information be stored and processed within defined jurisdictions to protect sensitive data. Compliance with these frameworks ensures that organizations adhere to legal standards on data residency, access controls, and audit trails to maintain data integrity and privacy. Enterprises must implement tailored governance policies aligning with regulatory directives to mitigate risks associated with cross-border data transfers and unauthorized information access.
Security Implications of Sovereignty Models
Data sovereignty refers to the legal control over data within a specific jurisdiction, whereas information sovereignty emphasizes the protection and management of information regardless of its location. Security implications of sovereignty models include challenges in compliance with diverse regulatory frameworks, increased risk of data breaches due to jurisdictional complexities, and the necessity for robust encryption and access controls to maintain data integrity. Organizations must implement tailored security strategies that address cross-border data flows and ensure adherence to local laws while protecting sensitive information.
Technology Solutions for Sovereignty Enforcement
Technology solutions for sovereignty enforcement emphasize robust data encryption, decentralized storage architectures, and blockchain-based access controls to ensure data sovereignty. Implementing edge computing and localized data centers reduces reliance on foreign infrastructure, enhancing information autonomy. Advanced identity management systems and AI-driven audit trails further reinforce compliance with regional data protection regulations.
Future Trends in Information and Data Sovereignty
Future trends in information and data sovereignty emphasize increasing regulatory measures to protect user privacy and data localization mandates driven by geopolitical tensions. Advances in blockchain and decentralized technologies are reshaping how data ownership and control are managed, promoting transparent and secure data governance models. Cross-border data flow policies will increasingly balance national security concerns with the demand for global digital innovation and interoperability.
Related Important Terms
Data Localization
Data localization refers to the legal requirement that digital information about a country's citizens or residents must be stored, processed, and accessed within the nation's borders, enhancing data sovereignty by maintaining control over data flows and protecting privacy. Ensuring data localization helps governments enforce regulations, prevent unauthorized cross-border data transfers, and mitigate risks associated with foreign surveillance or cyber threats.
Information Residency
Information residency refers to the physical or geographical location where data is stored and processed, impacting compliance with local data protection laws and regulatory requirements. Unlike data sovereignty that emphasizes legal ownership and control, information residency specifically addresses the jurisdictional aspects influencing data security, privacy, and access management.
Sovereign Cloud
Sovereign cloud ensures data sovereignty by storing and processing information within specific national or jurisdictional boundaries, enabling compliance with local data protection laws and regulatory requirements. This approach enhances control over data residency, security, and privacy, critical for organizations managing sensitive information under strict sovereignty mandates.
Digital Jurisdiction
Digital jurisdiction defines the authority a nation holds over data generated within its borders, emphasizing the control of digital information flow and storage. Information sovereignty extends beyond data sovereignty by encompassing the rights to access, manage, and protect information in digital spaces under specific legal frameworks.
Data Nationalism
Data nationalism prioritizes the control and ownership of data within a nation's borders, emphasizing strict regulations that restrict cross-border data flows to protect national security and economic interests. In contrast, data sovereignty refers to the legal framework asserting that data is subject to the laws and governance of the country where it is collected, highlighting compliance and jurisdictional authority rather than protectionism.
Regulatory Data Partitioning
Regulatory data partitioning enforces strict jurisdictional boundaries that separate data storage and processing according to local laws, ensuring compliance with sovereignty requirements. This method differentiates information sovereignty by emphasizing controlled data handling environments, whereas data sovereignty broadly refers to legal ownership and access rights over data within a specific territory.
Information Flow Control (IFC)
Information Flow Control (IFC) enforces strict policies to manage data movement and access within information systems, ensuring compliance with sovereignty laws by preventing unauthorized data transfer across borders. By integrating IFC mechanisms, organizations can maintain granular control over sensitive information, aligning data handling practices with regional sovereignty requirements and minimizing cross-jurisdictional data leakage risks.
Cross-border Data Governance
Cross-border data governance requires clear frameworks distinguishing information sovereignty, which protects data in use and processing, from data sovereignty, emphasizing jurisdiction over data storage and transfer. Effective policies must address legal compliance, privacy regulations, and international data flow to ensure security and control in global information exchanges.
Data Sovereignty-as-a-Service
Data Sovereignty-as-a-Service ensures that data is stored, processed, and managed in compliance with local regulations, providing organizations with control over data jurisdiction without the complexity of maintaining physical infrastructure. This service model enhances security, reduces legal risks, and supports global compliance by leveraging cloud platforms tailored to specific regional data sovereignty requirements.
Post-Cloud Sovereignty
Post-cloud sovereignty emphasizes controlling information flow and ensuring data sovereignty extends beyond traditional cloud infrastructures, addressing the challenges of decentralized data storage and processing. Information sovereignty entails comprehensive governance frameworks that safeguard data privacy, security, and compliance across distributed networks, promoting user autonomy and national jurisdiction enforcement in a post-cloud era.
Information vs Data Sovereignty Infographic
 industrydif.com
industrydif.com