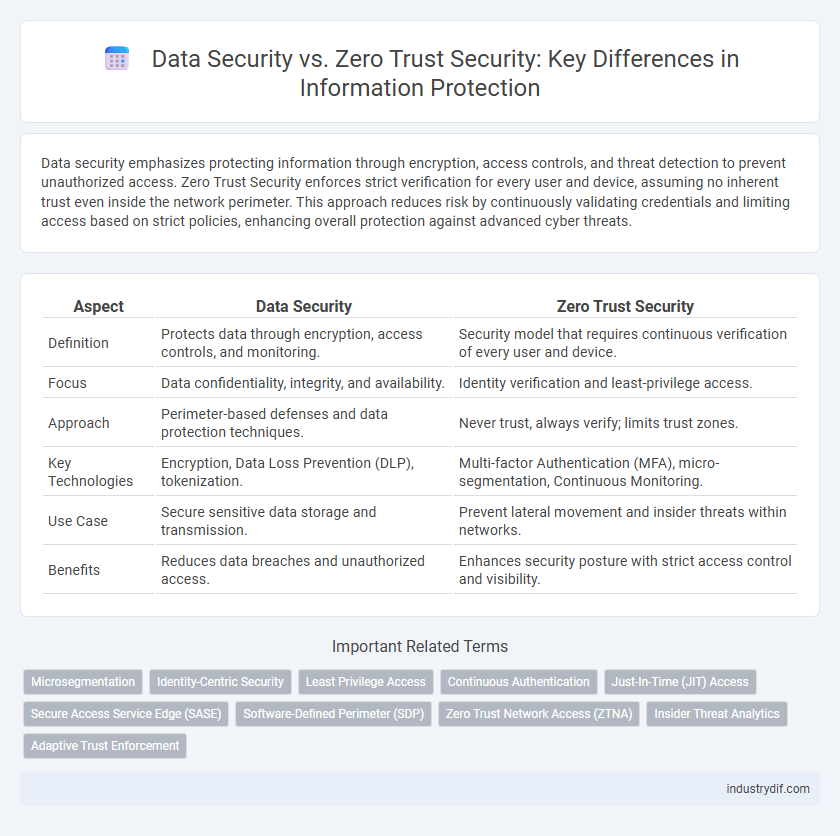
Data security emphasizes protecting information through encryption, access controls, and threat detection to prevent unauthorized access. Zero Trust Security enforces strict verification for every user and device, assuming no inherent trust even inside the network perimeter. This approach reduces risk by continuously validating credentials and limiting access based on strict policies, enhancing overall protection against advanced cyber threats.
Table of Comparison
| Aspect | Data Security | Zero Trust Security |
|---|---|---|
| Definition | Protects data through encryption, access controls, and monitoring. | Security model that requires continuous verification of every user and device. |
| Focus | Data confidentiality, integrity, and availability. | Identity verification and least-privilege access. |
| Approach | Perimeter-based defenses and data protection techniques. | Never trust, always verify; limits trust zones. |
| Key Technologies | Encryption, Data Loss Prevention (DLP), tokenization. | Multi-factor Authentication (MFA), micro-segmentation, Continuous Monitoring. |
| Use Case | Secure sensitive data storage and transmission. | Prevent lateral movement and insider threats within networks. |
| Benefits | Reduces data breaches and unauthorized access. | Enhances security posture with strict access control and visibility. |
Understanding Data Security: Core Principles
Data security centers on protecting sensitive information through encryption, access control, and regular audits to prevent unauthorized access and data breaches. Core principles include confidentiality, integrity, and availability, ensuring data remains accurate and accessible only to authorized users. Unlike zero trust security, which assumes no user or device is inherently trustworthy, traditional data security focuses on securing trusted networks and users within defined perimeters.
What Is Zero Trust Security?
Zero Trust Security is a cybersecurity model that operates on the principle of "never trust, always verify," requiring strict identity verification for every person and device attempting to access resources within a network. Unlike traditional data security approaches that rely on perimeter defenses, Zero Trust enforces continuous authentication and micro-segmentation to minimize the attack surface. This framework reduces risks from insider threats and lateral movement by assuming no device or user is inherently trusted, thereby enhancing overall data protection.
Key Differences Between Data Security and Zero Trust
Data security focuses on protecting data through encryption, access controls, and monitoring to prevent unauthorized access. Zero Trust security, however, operates on the principle of "never trust, always verify," requiring continuous authentication and strict access policies regardless of network location. While data security safeguards the data itself, Zero Trust emphasizes securing the entire IT environment by verifying every user and device before granting access.
Core Technologies in Data Security
Core technologies in data security include encryption, access control, and data masking to protect sensitive information from unauthorized access. Zero Trust Security extends these principles by continuously verifying user identities and device integrity through multi-factor authentication and micro-segmentation. Both models prioritize safeguarding data, but Zero Trust emphasizes continuous validation and minimizing trust zones within networks.
Zero Trust Architecture Explained
Zero Trust Architecture enforces strict identity verification for every user and device seeking access to resources, regardless of network location. Unlike traditional data security models that rely on perimeter defenses, Zero Trust continuously monitors and validates all activities within the network to minimize risks of breaches. Implementing Zero Trust reduces attack surfaces through micro-segmentation, least privilege access, and continuous authentication, ensuring robust protection against modern cyber threats.
Risks Addressed by Data Security Solutions
Data security solutions primarily address risks related to unauthorized data access, data breaches, and loss of sensitive information through encryption, access controls, and monitoring. These solutions mitigate threats such as insider attacks, malware, and accidental data leaks by ensuring data confidentiality, integrity, and availability. Zero Trust Security complements this by enforcing continuous authentication and strict access policies, focusing on minimizing trust zones and reducing attack surfaces.
How Zero Trust Mitigates Modern Threats
Zero Trust Security mitigates modern threats by continuously verifying every user and device attempting to access resources, minimizing the risk of insider threats and lateral movement in networks. Unlike traditional data security models that rely on perimeter defenses, Zero Trust enforces strict access controls and micro-segmentation, reducing the attack surface exploited by cybercriminals. It also implements real-time monitoring and adaptive authentication, enabling rapid detection and response to emerging threats such as phishing, ransomware, and advanced persistent threats (APTs).
Data Security Compliance and Regulations
Data security compliance involves adhering to regulations such as GDPR, HIPAA, and CCPA, which mandate strict controls over data access, encryption, and breach notification protocols. Zero Trust Security frameworks enhance compliance efforts by enforcing continuous verification of user identity and device trustworthiness, minimizing insider threats and unauthorized data access. Implementing Zero Trust principles helps organizations maintain regulatory requirements through granular access controls and real-time monitoring, reducing the risk of data breaches and ensuring robust data protection.
Implementing Zero Trust: Best Practices
Implementing Zero Trust security involves continuously validating user identities and device integrity before granting access to resources, minimizing the risk of unauthorized data breaches. Best practices include micro-segmentation of network resources, strict access controls based on the principle of least privilege, and continuous monitoring using behavioral analytics. Integrating multifactor authentication (MFA) and endpoint detection and response (EDR) tools further enhances protection by ensuring only verified users and devices interact with sensitive information.
Which Security Model Fits Your Organization?
Data security focuses on protecting sensitive information through encryption, access control, and threat prevention, while zero trust security emphasizes continuous verification of users and devices regardless of location. Organizations with complex, hybrid environments benefit from zero trust's granular access policies and real-time monitoring, whereas traditional data security suits simpler, perimeter-based setups. Evaluating your organization's risk posture, infrastructure complexity, and compliance requirements determines which security model aligns best with your security objectives.
Related Important Terms
Microsegmentation
Data security focuses on protecting sensitive information through encryption, access controls, and regular audits, while Zero Trust Security employs a strict identity verification process to assume no user or device is inherently trustworthy. Microsegmentation enhances Zero Trust by dividing networks into isolated segments, limiting lateral movement of threats and minimizing the attack surface within an organization's infrastructure.
Identity-Centric Security
Data security traditionally protects information through perimeter-based controls, while zero trust security emphasizes an identity-centric approach, continuously verifying user identities and device trustworthiness regardless of location. Identity-centric security in zero trust enforces strict access policies based on user roles, multi-factor authentication, and behavioral analytics to minimize insider threats and data breaches.
Least Privilege Access
Least Privilege Access enforces strict user permissions by limiting access rights to only what is essential for job functions, thereby reducing the attack surface in Data Security frameworks. Zero Trust Security amplifies this principle by continuously verifying user identities and access requests, ensuring that no entity is inherently trusted regardless of network location.
Continuous Authentication
Continuous authentication enhances data security by persistently verifying user identities through behavioral biometrics, device recognition, and contextual analysis, reducing the risk of unauthorized access. Zero Trust Security integrates continuous authentication to enforce strict access controls, minimizing internal and external threats by assuming no implicit trust within the network.
Just-In-Time (JIT) Access
Data Security frameworks protect information by implementing access controls and encryption, while Zero Trust Security assumes no implicit trust and enforces strict identity verification for all users and devices. Just-In-Time (JIT) Access in Zero Trust minimizes attack surfaces by granting temporary, time-bound permissions only when necessary, significantly reducing the risk of unauthorized access.
Secure Access Service Edge (SASE)
Secure Access Service Edge (SASE) integrates data security and Zero Trust Security by providing a cloud-native architecture that enforces strict access controls and continuous authentication, reducing risks from internal and external threats. By combining network security functions like SWG, CASB, and ZTNA into a unified platform, SASE ensures secure data access regardless of user location, optimizing overall security posture.
Software-Defined Perimeter (SDP)
Data Security emphasizes protecting data through encryption and access controls, whereas Zero Trust Security centers on continuous verification of every user and device, regardless of location. Software-Defined Perimeter (SDP) implements Zero Trust by dynamically creating secure, encrypted perimeters around critical resources, reducing attack surfaces and preventing unauthorized access.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) improves data security by enforcing strict identity verification and limiting user access to specific resources based on continuous risk assessment. Unlike traditional data security models that rely on perimeter defenses, ZTNA reduces attack surfaces and mitigates insider threats by granting least-privilege access regardless of location.
Insider Threat Analytics
Data Security focuses on protecting sensitive information through encryption and access controls, while Zero Trust Security extends these measures by continuously verifying all users and devices regardless of location. Insider Threat Analytics plays a crucial role in Zero Trust by monitoring user behavior and detecting anomalies to prevent data breaches from internal actors.
Adaptive Trust Enforcement
Adaptive trust enforcement dynamically adjusts security measures based on real-time risk assessments and contextual data, enhancing traditional data security by minimizing implicit trust within network environments. Zero Trust Security frameworks leverage this adaptive approach to continuously verify user identities and device integrity, thereby reducing vulnerability surfaces and preventing unauthorized access more effectively.
Data Security vs Zero Trust Security Infographic
 industrydif.com
industrydif.com