Encryption secures data by converting it into a coded format, preventing unauthorized access while requiring decryption for processing. Homomorphic encryption enables computations on encrypted data without needing to decrypt it, preserving privacy throughout processing. This advanced method enhances security in cloud computing and sensitive data analysis by maintaining confidentiality during data operations.
Table of Comparison
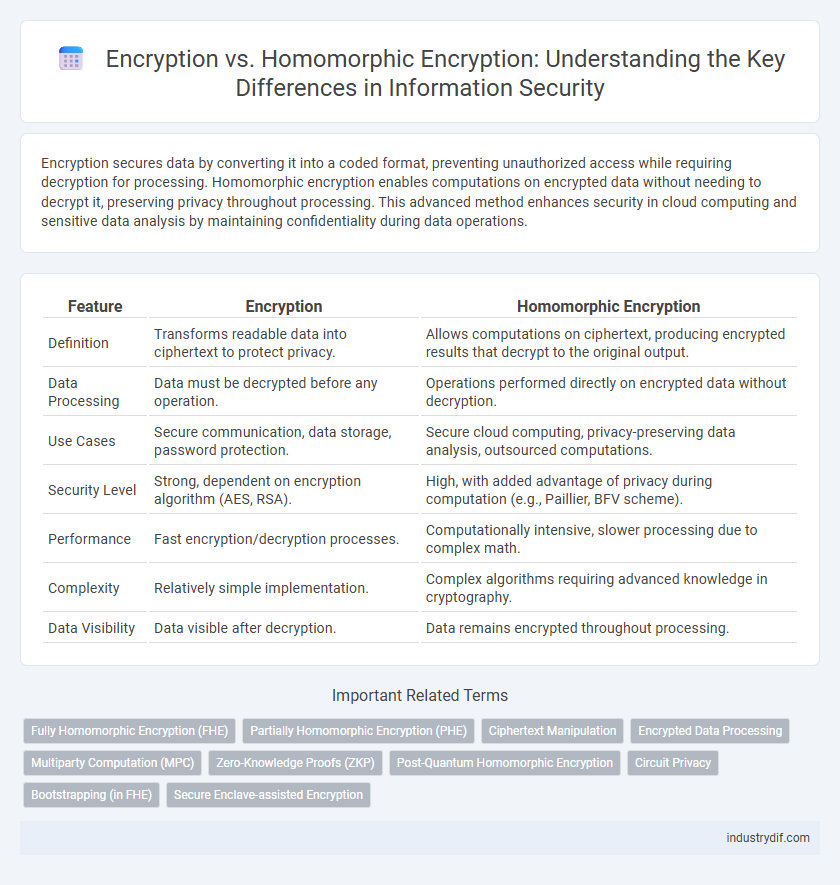
| Feature | Encryption | Homomorphic Encryption |
|---|---|---|
| Definition | Transforms readable data into ciphertext to protect privacy. | Allows computations on ciphertext, producing encrypted results that decrypt to the original output. |
| Data Processing | Data must be decrypted before any operation. | Operations performed directly on encrypted data without decryption. |
| Use Cases | Secure communication, data storage, password protection. | Secure cloud computing, privacy-preserving data analysis, outsourced computations. |
| Security Level | Strong, dependent on encryption algorithm (AES, RSA). | High, with added advantage of privacy during computation (e.g., Paillier, BFV scheme). |
| Performance | Fast encryption/decryption processes. | Computationally intensive, slower processing due to complex math. |
| Complexity | Relatively simple implementation. | Complex algorithms requiring advanced knowledge in cryptography. |
| Data Visibility | Data visible after decryption. | Data remains encrypted throughout processing. |
Introduction to Encryption and Homomorphic Encryption
Encryption secures data by converting it into unreadable ciphertext using algorithms like AES or RSA, ensuring confidentiality during storage and transmission. Homomorphic encryption extends this concept by enabling computations directly on encrypted data without decryption, preserving privacy while allowing data processing. This innovative approach supports secure cloud computing and data analysis in sensitive environments such as healthcare and finance.
Core Principles of Conventional Encryption
Conventional encryption primarily relies on symmetric or asymmetric key algorithms to transform plaintext into ciphertext, securing data through secrecy and controlled access. Its core principle involves key management, ensuring that only authorized parties can decrypt the information by using appropriate private or public keys. This method emphasizes data confidentiality but requires data to be decrypted before processing, exposing it to potential risks during computation.
Understanding Homomorphic Encryption
Homomorphic encryption enables computations directly on encrypted data without needing to decrypt it first, preserving privacy and security. Unlike traditional encryption, which requires data to be decrypted before processing, homomorphic encryption supports operations such as addition and multiplication on ciphertexts, producing encrypted results that, when decrypted, match the outcome of operations performed on the plaintext. This property is crucial for secure data analysis in cloud computing, confidential data sharing, and privacy-preserving machine learning.
Key Differences: Encryption vs Homomorphic Encryption
Encryption secures data by transforming plaintext into ciphertext, requiring decryption for analysis, while homomorphic encryption allows computations directly on encrypted data without needing decryption. Traditional encryption prioritizes data confidentiality but limits processing capabilities, whereas homomorphic encryption enables privacy-preserving data operations in cloud computing and secure multi-party computations. Key differences include the ability of homomorphic encryption to perform arithmetic operations on ciphertext, maintaining functionality alongside security.
Industry Applications of Standard Encryption
Standard encryption is widely used in industries such as finance, healthcare, and e-commerce to protect sensitive data like credit card transactions, patient records, and customer information during storage and transmission. It enables secure communication channels through protocols such as TLS/SSL, ensuring data confidentiality and integrity in online banking and retail platforms. Enterprises rely on symmetric and asymmetric encryption algorithms, including AES and RSA, to comply with regulatory standards like GDPR and HIPAA while safeguarding intellectual property and consumer privacy.
Use Cases for Homomorphic Encryption
Homomorphic encryption enables computations on encrypted data without decryption, making it ideal for privacy-preserving cloud computing, secure data analysis, and confidential machine learning. It supports secure multiparty computations in healthcare for sensitive patient data sharing and financial services for fraud detection while maintaining data confidentiality. Its use cases extend to protecting personal information in IoT devices and enabling collaborative research between organizations without exposing raw data.
Security Implications in Both Encryption Types
Encryption protects data by converting it into unreadable formats, ensuring confidentiality against unauthorized access. Homomorphic encryption extends this by enabling computations on encrypted data without decryption, preserving privacy during processing but often with increased computational overhead. Security implications include traditional encryption's vulnerability when decrypting data for processing, while homomorphic encryption reduces this risk by maintaining encryption throughout computation, albeit with potential performance trade-offs.
Performance and Scalability Considerations
Encryption typically offers faster processing speeds and lower computational overhead compared to homomorphic encryption, which demands significant resources due to complex mathematical operations. Homomorphic encryption enables computations on encrypted data without decryption, enhancing privacy but often resulting in slower performance and limited scalability. Balancing security requirements with performance, homomorphic encryption remains challenging to deploy at scale in real-time or large-data environments.
Regulatory Compliance and Privacy Concerns
Encryption secures data by converting it into ciphertext, ensuring regulatory compliance such as GDPR and HIPAA by protecting sensitive information from unauthorized access. Homomorphic encryption advances privacy concerns by enabling computations on encrypted data without decryption, maintaining data confidentiality throughout processing while meeting strict regulatory standards. This cryptographic method supports secure data analytics and cloud computing environments where privacy preservation and compliance are critical.
Future Trends in Data Encryption Technologies
Future trends in data encryption technologies emphasize the growing adoption of homomorphic encryption, which allows computation on encrypted data without decryption, enhancing privacy and security in cloud computing and data sharing. Traditional encryption methods remain essential but are increasingly supplemented by advanced techniques like lattice-based cryptography to resist quantum attacks. The integration of homomorphic encryption with artificial intelligence and blockchain promises breakthroughs in secure data analytics and decentralized applications.
Related Important Terms
Fully Homomorphic Encryption (FHE)
Fully Homomorphic Encryption (FHE) enables computations on encrypted data without requiring decryption, preserving privacy while allowing complex data processing. This advanced form of encryption surpasses traditional methods by supporting arithmetic operations directly on ciphertext, making it crucial for secure cloud computing and privacy-preserving applications.
Partially Homomorphic Encryption (PHE)
Partially Homomorphic Encryption (PHE) allows specific mathematical operations, such as addition or multiplication, to be performed directly on encrypted data without revealing the plaintext, enhancing data security in computations. Unlike fully homomorphic encryption, PHE supports limited types of operations, making it more efficient for practical applications like secure voting or private data analysis.
Ciphertext Manipulation
Encryption transforms plaintext into ciphertext to secure data, but traditional methods require decryption for manipulation, exposing data risks. Homomorphic encryption allows ciphertext manipulation directly, enabling computations on encrypted data without revealing the original information, enhancing privacy and security in data processing.
Encrypted Data Processing
Encrypted data processing enables secure computation on ciphertexts without revealing underlying plaintext, preserving data privacy during analysis. Homomorphic encryption extends this capability by allowing complex operations directly on encrypted data, supporting advanced secure data processing workflows in cloud computing and confidential data analytics.
Multiparty Computation (MPC)
Encryption secures data by transforming it into unreadable ciphertext, while homomorphic encryption enables computations directly on encrypted data without decryption. In Multiparty Computation (MPC), homomorphic encryption facilitates collaborative data processing among parties, preserving privacy by ensuring no individual can access the raw inputs during joint computations.
Zero-Knowledge Proofs (ZKP)
Encryption secures data by converting it into a ciphertext using a key, preventing unauthorized access, while homomorphic encryption allows computations on encrypted data without decryption, preserving privacy in processing. Zero-Knowledge Proofs (ZKP) enhance these methods by enabling one party to prove knowledge of a secret or claim without revealing the secret itself, crucial for verifying encrypted data's integrity and computations in privacy-preserving protocols.
Post-Quantum Homomorphic Encryption
Post-quantum homomorphic encryption enables computations on encrypted data without decryption, protecting sensitive information against quantum computer attacks. This advanced cryptographic method combines the data privacy of homomorphic encryption with quantum-resistant algorithms, ensuring secure data processing in the era of quantum computing.
Circuit Privacy
Encryption secures data by converting it into ciphertext, but traditional methods often expose computational patterns during processing, unlike homomorphic encryption which enables computations on encrypted data without decryption, preserving circuit privacy by preventing leakage of underlying algorithmic structures. Circuit privacy is critical in homomorphic encryption to ensure that neither the input data nor the specific functions applied are revealed through ciphertext, protecting intellectual property and sensitive operations during secure computations.
Bootstrapping (in FHE)
Bootstrapping in Fully Homomorphic Encryption (FHE) is a crucial process that refreshes ciphertexts to reduce noise accumulation, enabling unlimited-depth computation on encrypted data without decryption. Unlike traditional encryption methods, which do not support complex operations on ciphertext, bootstrapping ensures practical usability of FHE by maintaining ciphertext integrity during extended computations.
Secure Enclave-assisted Encryption
Secure Enclave-assisted encryption leverages hardware-based security to protect sensitive data during processing, ensuring that encryption keys remain isolated from the main operating system and potential vulnerabilities. Unlike traditional encryption that requires data decryption for computation, homomorphic encryption allows processing of encrypted data without exposing plaintext, but Secure Enclave-assisted methods offer enhanced performance and lower computational overhead for secure data handling.
Encryption vs Homomorphic Encryption Infographic
 industrydif.com
industrydif.com