Information security involves protecting data from unauthorized access, breaches, and threats through policies, technologies, and controls. Zero Trust is a security framework that assumes no user or system is trustworthy by default, enforcing strict verification and continuous monitoring for every access request. Emphasizing Zero Trust enhances information security by minimizing risks associated with insider threats and compromised credentials.
Table of Comparison
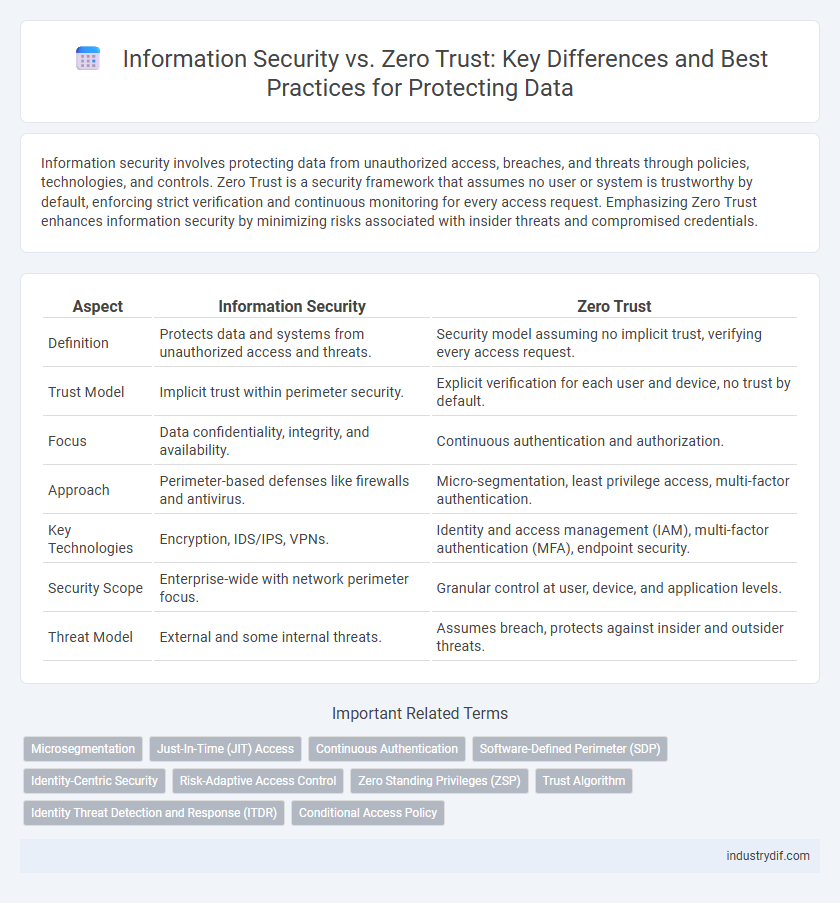
| Aspect | Information Security | Zero Trust |
|---|---|---|
| Definition | Protects data and systems from unauthorized access and threats. | Security model assuming no implicit trust, verifying every access request. |
| Trust Model | Implicit trust within perimeter security. | Explicit verification for each user and device, no trust by default. |
| Focus | Data confidentiality, integrity, and availability. | Continuous authentication and authorization. |
| Approach | Perimeter-based defenses like firewalls and antivirus. | Micro-segmentation, least privilege access, multi-factor authentication. |
| Key Technologies | Encryption, IDS/IPS, VPNs. | Identity and access management (IAM), multi-factor authentication (MFA), endpoint security. |
| Security Scope | Enterprise-wide with network perimeter focus. | Granular control at user, device, and application levels. |
| Threat Model | External and some internal threats. | Assumes breach, protects against insider and outsider threats. |
Introduction to Information Security and Zero Trust
Information Security involves protecting data integrity, confidentiality, and availability through measures like access controls, encryption, and threat detection. Zero Trust is a cybersecurity model that assumes no implicit trust inside or outside the network, enforcing strict identity verification and continuous monitoring to minimize risk. Implementing Zero Trust strengthens Information Security by reducing attack surfaces and ensuring that every access request is thoroughly validated.
Defining Information Security: Core Concepts
Information security encompasses the protection of data confidentiality, integrity, and availability across digital and physical assets. It involves implementing policies, controls, and technologies designed to prevent unauthorized access, data breaches, and cyber threats. Zero Trust, as a security paradigm, builds on these core concepts by enforcing strict verification for every access request, regardless of the user's location within or outside the network.
Understanding Zero Trust: Principles and Framework
Zero Trust is a cybersecurity framework that operates on the principle of never trusting any entity inside or outside the network perimeter by default, enforcing continuous verification of all users, devices, and applications. Its core principles include least privilege access, micro-segmentation, and strong authentication methods, which collectively minimize attack surfaces and limit lateral movement within networks. Implementing Zero Trust requires integrating advanced technologies such as multi-factor authentication (MFA), identity and access management (IAM), and real-time monitoring to ensure strict access controls and enhanced security postures.
Key Differences Between Information Security and Zero Trust
Information Security encompasses a broad range of practices, policies, and technologies aimed at protecting data confidentiality, integrity, and availability from unauthorized access or cyber threats. Zero Trust is a specific security model within Information Security that operates on the principle of "never trust, always verify," requiring strict identity verification and micro-segmentation regardless of network location. Key differences include Information Security's wide scope covering various defenses, while Zero Trust focuses on continuous authentication and least-privilege access controls to limit lateral movement within networks.
Advantages of Traditional Information Security Models
Traditional information security models offer streamlined perimeter defense by focusing on safeguarding network boundaries, enabling clear access control policies and centralized monitoring. These models often provide simpler implementation and lower initial costs compared to Zero Trust frameworks, making them suitable for organizations with limited resources or established infrastructure. Established tools such as firewalls, antivirus software, and intrusion detection systems effectively mitigate common threats within conventional security architectures.
Zero Trust Architecture: Benefits and Challenges
Zero Trust Architecture enhances information security by enforcing strict identity verification and micro-segmentation, minimizing the risk of unauthorized access within complex networks. Its benefits include improved threat detection, reduced attack surfaces, and adaptive access control, which collectively strengthen data protection strategies. Challenges involve implementation complexity, operational costs, and the need for continuous monitoring and policy updates to maintain effective security postures.
Implementation Strategies: Information Security vs Zero Trust
Implementing Information Security involves establishing layered defenses, including firewalls, encryption, and access controls, to protect data integrity and confidentiality across the network. Zero Trust architecture requires continuous verification of user identities and device health, enforcing strict access permissions regardless of network location to minimize potential breaches. Combining traditional Information Security measures with Zero Trust principles creates a robust framework that proactively mitigates risks by limiting trust zones and isolating sensitive assets.
Industry Standards and Compliance Considerations
Industry standards such as NIST SP 800-53 and ISO/IEC 27001 emphasize rigorous risk assessments and layered security controls integral to Information Security frameworks. Zero Trust architecture, aligned with these standards, mandates strict identity verification and micro-segmentation to prevent unauthorized access within networks. Compliance considerations include adhering to regulations like GDPR, HIPAA, and PCI-DSS, which increasingly incorporate Zero Trust principles to enhance data protection and reduce breach risks.
Case Studies: Migration from Information Security to Zero Trust
Case studies of migration from traditional Information Security to Zero Trust reveal significant improvements in threat detection and access control by implementing identity-centric policies and micro-segmentation. Organizations like Google and Microsoft demonstrate reduced lateral movement within networks and minimized insider threats through continuous verification and least-privilege access models. These real-world examples highlight how Zero Trust frameworks enhance security postures beyond perimeter-based defenses by assuming breach and enforcing strict access validation.
Future Trends in Information Security and Zero Trust
Emerging trends in information security emphasize the growing adoption of Zero Trust architectures, which enforce strict identity verification and micro-segmentation to mitigate cyber risks. Artificial intelligence and machine learning enhance threat detection and response capabilities, enabling proactive defense against sophisticated attacks in Zero Trust environments. Cloud-native security solutions and continuous monitoring are expected to dominate future strategies, ensuring adaptive protection across complex hybrid infrastructures.
Related Important Terms
Microsegmentation
Microsegmentation enhances zero trust architecture by isolating workloads and enforcing granular access controls within a network, reducing attack surfaces and limiting lateral movement of threats. Information security strategies leveraging microsegmentation ensure continuous verification of user and device trustworthiness, aligning with zero trust principles to protect sensitive data and critical assets.
Just-In-Time (JIT) Access
Just-In-Time (JIT) Access in information security minimizes risk by granting users temporary, time-bound permissions, reducing exposure to sensitive data and preventing persistent access vulnerabilities. Zero Trust architectures integrate JIT Access as a core principle, enforcing strict verification and dynamic access controls to ensure users only gain necessary resources precisely when needed.
Continuous Authentication
Continuous authentication strengthens information security by verifying user identity in real-time based on behavioral biometrics and contextual data, reducing reliance on one-time login credentials. This ongoing verification process aligns with Zero Trust principles by ensuring that access permissions are constantly re-evaluated to prevent unauthorized breaches.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) enhances Information Security by creating dynamic, context-aware perimeters that restrict access based on user identity and device posture, aligning closely with Zero Trust principles. By segmenting networks and enforcing strict authentication before connection, SDP minimizes attack surfaces and mitigates risks inherent in traditional perimeter-based defenses.
Identity-Centric Security
Information security emphasizes protecting data through perimeter defenses, while Zero Trust adopts an identity-centric approach, continuously verifying user identities and access privileges regardless of network location, reducing insider threats and unauthorized access risks. This identity-focused model enforces strict authentication and authorization policies, ensuring that trust is never implicit but always dynamically evaluated based on user credentials and behavior.
Risk-Adaptive Access Control
Risk-Adaptive Access Control enhances Information Security by dynamically adjusting user permissions based on real-time threat intelligence and contextual factors, reducing exposure to potential breaches. Zero Trust frameworks implement this approach by continuously verifying all access requests, minimizing the risk of unauthorized data access within complex IT environments.
Zero Standing Privileges (ZSP)
Zero Standing Privileges (ZSP) in information security enforces minimal access rights, eliminating permanent privileges to reduce the risk of insider threats and lateral movement within a network. Unlike traditional zero trust models that continuously verify user and device identities, ZSP ensures no user retains persistent access, mandating real-time permissions only when necessary.
Trust Algorithm
Zero Trust employs a trust algorithm that continuously verifies all users and devices before granting access, eliminating implicit trust within the network. Information Security frameworks leverage this dynamic trust evaluation to minimize risks and prevent unauthorized access by enforcing strict identity verification and access controls.
Identity Threat Detection and Response (ITDR)
Identity Threat Detection and Response (ITDR) is a critical component in both Information Security and Zero Trust frameworks, focusing on continuously monitoring, detecting, and mitigating identity-based threats to prevent unauthorized access. ITDR enhances Zero Trust by verifying every identity request through real-time analytics, behavioral analysis, and automated response mechanisms to safeguard sensitive data and systems.
Conditional Access Policy
Information security frameworks emphasize protecting data through layered defenses, while Zero Trust architecture requires strict verification for every access request. Conditional Access Policy in Zero Trust enforces adaptive security measures based on user identity, device compliance, location, and real-time risk analysis to minimize unauthorized data exposure.
Information Security vs Zero Trust Infographic
 industrydif.com
industrydif.com