Firewalls serve as traditional network security barriers that monitor and control incoming and outgoing traffic based on predetermined rules, primarily protecting the perimeter of a network. Zero Trust Network Architecture eliminates implicit trust by continuously verifying every user and device attempting to access resources, enforcing strict access controls regardless of location. This approach reduces security risks by assuming that threats can exist both inside and outside the network perimeter, making it more robust for modern, dynamic environments.
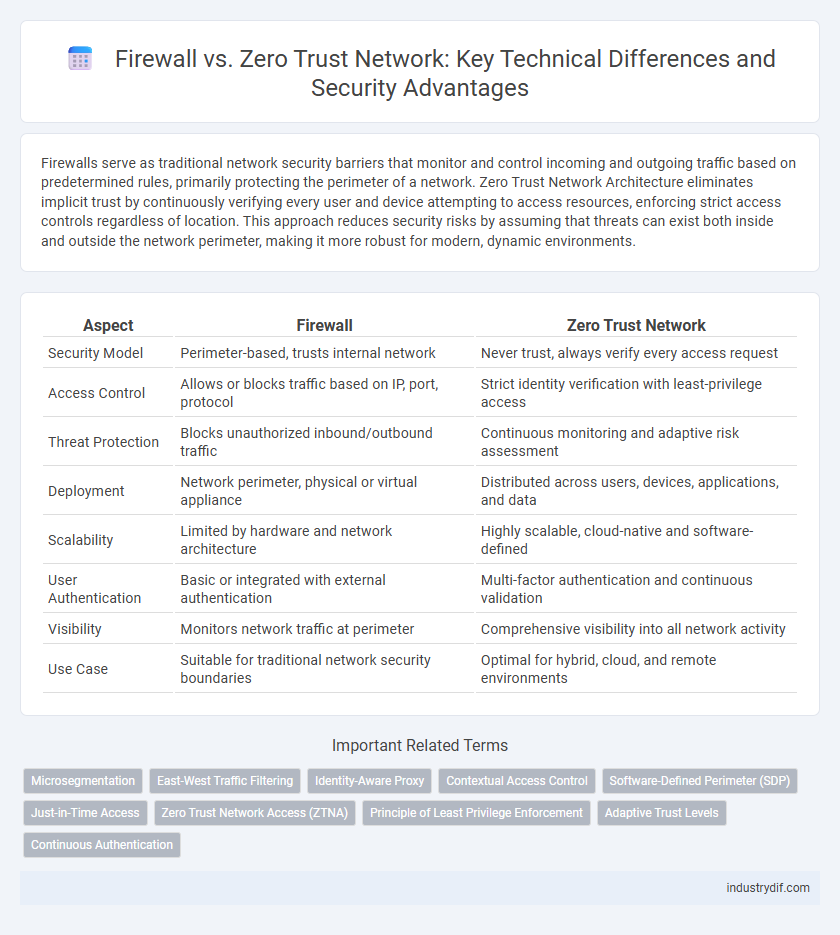
Table of Comparison
| Aspect | Firewall | Zero Trust Network |
|---|---|---|
| Security Model | Perimeter-based, trusts internal network | Never trust, always verify every access request |
| Access Control | Allows or blocks traffic based on IP, port, protocol | Strict identity verification with least-privilege access |
| Threat Protection | Blocks unauthorized inbound/outbound traffic | Continuous monitoring and adaptive risk assessment |
| Deployment | Network perimeter, physical or virtual appliance | Distributed across users, devices, applications, and data |
| Scalability | Limited by hardware and network architecture | Highly scalable, cloud-native and software-defined |
| User Authentication | Basic or integrated with external authentication | Multi-factor authentication and continuous validation |
| Visibility | Monitors network traffic at perimeter | Comprehensive visibility into all network activity |
| Use Case | Suitable for traditional network security boundaries | Optimal for hybrid, cloud, and remote environments |
Understanding Traditional Firewalls
Traditional firewalls serve as perimeter defense systems that control incoming and outgoing network traffic based on predetermined security rules, primarily filtering traffic by IP addresses, ports, and protocols. They are designed to establish a protective barrier between trusted internal networks and untrusted external environments but lack granular authentication and continuous verification of user identity. This inherent limitation makes traditional firewalls insufficient for modern security demands, such as protecting distributed workforces and cloud environments, where Zero Trust Network Architecture (ZTNA) offers continuous validation and role-based access controls.
Core Principles of Zero Trust Network
Zero Trust Network architecture is built on the core principle of "never trust, always verify," requiring continuous authentication and authorization for all users and devices, regardless of their location within or outside the network perimeter. Unlike traditional firewalls that primarily filter traffic based on IP addresses and ports, Zero Trust enforces strict identity verification, micro-segmentation, and least privilege access to minimize attack surfaces. This proactive approach enhances security posture by assuming breach and limiting lateral movement within the network.
Key Differences: Firewall vs Zero Trust
Firewalls serve as perimeter defense mechanisms that monitor and control incoming and outgoing network traffic based on predetermined security rules, primarily focusing on filtering access at the network edge. Zero Trust Network Architecture (ZTNA) enforces strict identity verification for every user and device, regardless of location, implementing granular access controls and continuous monitoring within the network. Unlike traditional firewalls that rely on implicit trust within the internal network, Zero Trust eliminates implicit trust by segmenting networks and validating every access request dynamically.
Access Control Mechanisms Compared
Firewalls primarily rely on perimeter-based access control, filtering traffic based on IP addresses, ports, and protocols to create a boundary between trusted and untrusted networks. Zero Trust Network Access (ZTNA) employs continuous verification and context-aware policies, granting access based on user identity, device posture, and real-time risk assessments rather than network location. Unlike traditional firewall models, Zero Trust minimizes implicit trust by enforcing least-privilege access through micro-segmentation and adaptive authentication methods.
Security Policy Enforcement in Both Models
Firewall security policy enforcement relies on predefined perimeter rules controlling inbound and outbound traffic based on IP addresses, ports, and protocols, effectively blocking unauthorized access at network boundaries. Zero Trust Network uses continuous verification, enforcing security policies at the identity, device, and application levels, regardless of network location, minimizing trust assumptions. This granular, adaptive policy enforcement in Zero Trust offers enhanced protection against lateral movement and insider threats compared to traditional firewall models.
Scalability: Legacy Firewalls vs Zero Trust
Legacy firewalls often struggle with scalability due to their perimeter-based security model, which becomes increasingly complex and less effective as networks expand and incorporate cloud services. Zero Trust Network Architecture (ZTNA) offers superior scalability by enforcing granular, identity-based access controls that adapt dynamically to distributed and hybrid environments. This approach minimizes attack surfaces and enhances security posture without the bottlenecks associated with scaling traditional firewalls.
Threat Detection and Response Capabilities
Firewall technology primarily relies on predefined rules and perimeter-based defenses, limiting its ability to detect sophisticated threats that bypass traditional boundaries. Zero Trust Network architectures employ continuous verification and granular access controls, enabling real-time threat detection and swift response to suspicious activities within the network. Enhanced behavioral analytics and micro-segmentation in Zero Trust frameworks significantly improve threat containment and reduce response times compared to conventional firewall systems.
Deployment Challenges and Considerations
Firewall deployment often faces challenges such as complex rule management, scalability limitations, and difficulty in handling encrypted traffic, whereas Zero Trust Network implementations require extensive identity verification, continuous monitoring, and seamless integration with multifactor authentication systems. Zero Trust demands substantial changes in network architecture and employee training, increasing initial deployment complexity but offering enhanced security granularity. Both approaches necessitate careful consideration of existing infrastructure compatibility, resource allocation, and the organization's risk tolerance to ensure effective protection.
Industry Use Cases: When to Choose Which
Firewalls remain essential for traditional network perimeter defense, particularly in industries with well-defined physical boundaries like manufacturing and finance. Zero Trust Network models excel in dynamic environments such as healthcare and technology, where continuous verification and strict access controls protect sensitive data across distributed architectures. Enterprises with hybrid cloud deployments benefit from integrating Zero Trust principles to complement firewall protections for enhanced security posture and granular access management.
Future of Network Security: Evolving Beyond Firewalls
The future of network security is shifting from traditional firewalls to Zero Trust Network architectures that verify every access request regardless of location. Zero Trust models minimize insider threats by enforcing strict identity verification and micro-segmentation, reducing attack surfaces significantly. This evolution supports dynamic cloud environments and mobile workforces with adaptive security policies that outpace static firewall rules.
Related Important Terms
Microsegmentation
Microsegmentation, a core principle of Zero Trust Network Architecture, divides a network into isolated segments to enhance security by limiting lateral movement of threats, unlike traditional firewalls which primarily control traffic based on perimeter defenses. This granular control allows Zero Trust models to enforce strict access policies at the workload level, significantly reducing the attack surface compared to conventional firewall approaches.
East-West Traffic Filtering
Firewalls primarily focus on controlling North-South traffic by filtering data entering and exiting a network perimeter, while Zero Trust Network architecture enforces stringent East-West traffic filtering through micro-segmentation and continuous verification of internal communication. This granular inspection reduces lateral movement risks by validating user identities and device health across all network segments, enhancing overall security posture against insider threats and lateral attacks.
Identity-Aware Proxy
Identity-Aware Proxy (IAP) enhances Zero Trust Network architecture by enforcing granular access controls based on user identity and context rather than relying solely on perimeter defenses like traditional firewalls. This approach reduces attack surfaces by validating user credentials and device posture continuously, enabling secure access to applications without exposing the network to unauthorized traffic.
Contextual Access Control
Firewall technology primarily relies on perimeter-based security to regulate incoming and outgoing network traffic based on predetermined rules, whereas Zero Trust Network Access (ZTNA) enforces Contextual Access Control by continuously verifying user identity, device posture, and real-time risk factors before granting access to resources. This dynamic context-aware approach in ZTNA minimizes attack surfaces and enhances security posture compared to traditional firewalls that often permit broad access once inside the network perimeter.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) enhances Zero Trust Network Architecture by dynamically creating secure, individualized network perimeters based on user identity and device posture, contrasting traditional firewall models that rely on static, perimeter-based defenses. SDP minimizes attack surfaces through real-time authentication and encrypted access, enabling granular control and seamless scalability beyond the limitations of conventional firewall technologies.
Just-in-Time Access
Just-in-Time Access within Zero Trust Network Architecture dynamically provisions user permissions only for the duration needed, minimizing persistent access risks that traditional firewalls cannot control effectively. Firewalls rely on static perimeter defenses, whereas Just-in-Time Access enforces least privilege by continuously validating user context and access requirements in real-time.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) eliminates implicit trust by continuously verifying user identity and device posture before granting access to applications, significantly reducing the attack surface compared to traditional firewalls that rely on perimeter defense. ZTNA enforces granular, context-aware policies, providing secure, remote access based on least privilege principles rather than broad network-level permissions typical of firewalls.
Principle of Least Privilege Enforcement
Firewalls primarily control network traffic based on predefined rules but often lack granular access controls, whereas Zero Trust Networks strictly enforce the Principle of Least Privilege by continuously verifying user identities and device compliance before granting minimal, role-based access. This dynamic, context-aware enforcement significantly reduces the attack surface compared to traditional firewall models.
Adaptive Trust Levels
Adaptive trust levels in Zero Trust Network Architecture dynamically evaluate user behavior, device security posture, and contextual factors to continuously adjust access permissions, reducing risk beyond traditional firewall static rules. Firewalls primarily rely on predetermined access control lists, lacking the granular, real-time trust assessments vital for modern threat landscapes.
Continuous Authentication
Zero Trust Network emphasizes continuous authentication by constantly verifying user identities and device health throughout every session, unlike traditional firewalls that enforce static perimeter-based security controls. Continuous authentication in Zero Trust minimizes breach risks by dynamically assessing context and access permissions in real-time, ensuring secure and adaptive network defense.
Firewall vs Zero Trust Network Infographic
 industrydif.com
industrydif.com