On-premises infrastructure provides organizations with full control over their hardware and data, but often lacks the dynamic security model required to address modern threats effectively. Zero Trust Architecture enforces strict identity verification and continuous monitoring regardless of network location, minimizing the risk of breaches within internal environments. Integrating Zero Trust principles into on-premises setups enhances security by reducing reliance on perimeter defense and assuming no implicit trust in any user or device.
Table of Comparison
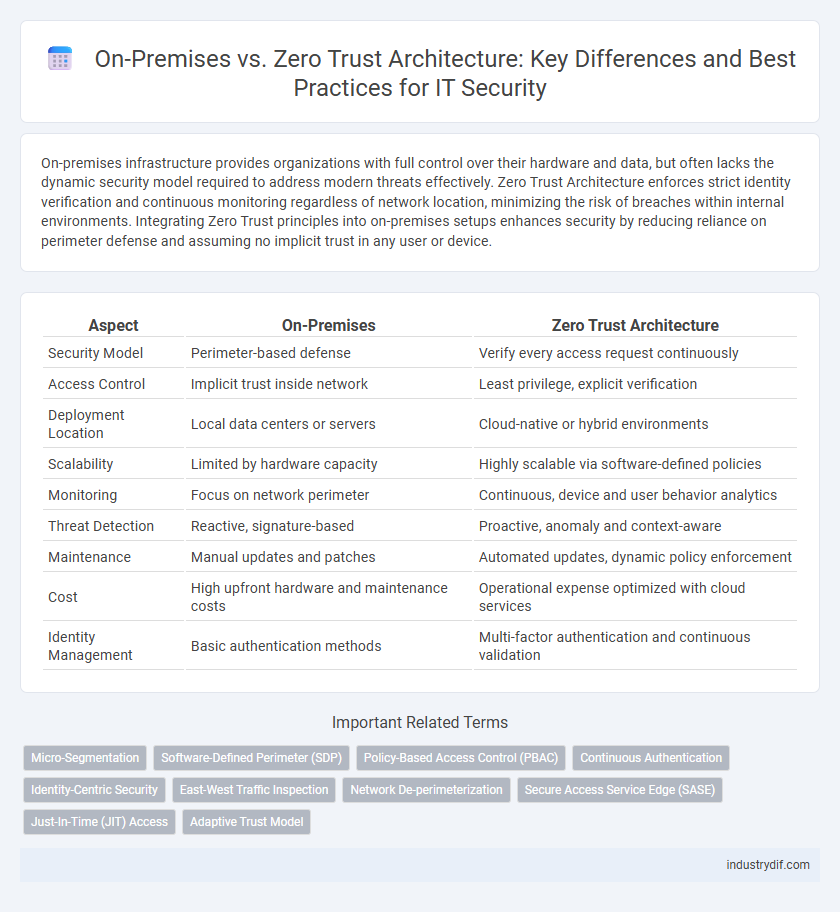
| Aspect | On-Premises | Zero Trust Architecture |
|---|---|---|
| Security Model | Perimeter-based defense | Verify every access request continuously |
| Access Control | Implicit trust inside network | Least privilege, explicit verification |
| Deployment Location | Local data centers or servers | Cloud-native or hybrid environments |
| Scalability | Limited by hardware capacity | Highly scalable via software-defined policies |
| Monitoring | Focus on network perimeter | Continuous, device and user behavior analytics |
| Threat Detection | Reactive, signature-based | Proactive, anomaly and context-aware |
| Maintenance | Manual updates and patches | Automated updates, dynamic policy enforcement |
| Cost | High upfront hardware and maintenance costs | Operational expense optimized with cloud services |
| Identity Management | Basic authentication methods | Multi-factor authentication and continuous validation |
Introduction to On-Premises and Zero Trust Architecture
On-Premises infrastructure refers to the deployment of IT resources within the physical confines of an organization, providing direct control over hardware and data security. Zero Trust Architecture emphasizes a strict identity verification process, assuming no trusted network perimeter, and continuously validating every user and device attempting to access resources. This security model shifts from traditional perimeter defenses to granular access controls based on dynamic policies and real-time context evaluation.
Core Principles of On-Premises Security
On-premises security relies heavily on physical control over hardware and network infrastructure, ensuring that servers, storage, and devices remain within organizational boundaries. It emphasizes perimeter defense through firewalls, intrusion detection systems, and secure access controls based on trusted internal networks. Core principles include maintaining strict asset management, user authentication via directory services like Active Directory, and continuous monitoring to detect anomalies within a controlled environment.
Fundamentals of Zero Trust Architecture
Zero Trust Architecture centers on continuous verification of user identities, devices, and access permissions, contrasting sharply with traditional on-premises security that relies on perimeter defenses. It implements micro-segmentation, multi-factor authentication (MFA), and least-privilege access to minimize risk and prevent lateral movement within networks. Zero Trust's fundamental principle assumes no implicit trust inside or outside the network, enhancing security posture beyond the static boundaries of on-premises environments.
Identity and Access Management Differences
On-Premises Identity and Access Management (IAM) relies heavily on centralized directory services and perimeter-based security controls, often limiting access to internal network environments. Zero Trust Architecture (ZTA) employs continuous verification of user identities and device health regardless of network location, enforcing least-privilege access through dynamic policy evaluation. This fundamental shift enhances security by minimizing attack surfaces and reducing reliance on static trust boundaries inherent in traditional on-premises systems.
Network Segmentation and Micro-Segmentation
Network segmentation in on-premises environments divides the network into isolated zones to contain breaches and improve security monitoring, relying on physical or virtual barriers such as VLANs and firewalls. Zero Trust Architecture enhances this approach by implementing micro-segmentation, which applies granular, identity-based access controls to individual workloads and devices, minimizing lateral movement within the network. Micro-segmentation leverages software-defined perimeters and continuous verification, significantly reducing attack surfaces compared to traditional segmented networks.
Threat Detection and Incident Response
On-premises security systems rely heavily on perimeter defenses, which can delay threat detection and prolong incident response times due to limited visibility beyond network boundaries. Zero Trust Architecture (ZTA) enhances threat detection by continuously authenticating and authorizing users and devices across all resources, enabling rapid identification of anomalies and reducing dwell time of threats. Incident response in ZTA frameworks is streamlined through automated policy enforcement and real-time monitoring, minimizing manual intervention and improving overall security posture.
Data Protection and Compliance Considerations
On-premises environments offer direct control over data storage and security protocols, enabling easier adherence to strict regulatory requirements such as GDPR, HIPAA, and PCI-DSS through localized data governance. Zero Trust Architecture enhances data protection by enforcing continuous authentication, micro-segmentation, and least-privilege access, reducing the risk of insider threats and lateral movement in cloud or hybrid environments. Compliance considerations in Zero Trust involve implementing comprehensive logging, real-time monitoring, and automated policy enforcement to ensure auditability and alignment with industry standards.
Scalability and Flexibility in Security Models
On-premises security models often face scalability challenges due to hardware limitations and fixed infrastructure, making rapid adaptation to evolving threats difficult. Zero Trust Architecture enhances scalability by leveraging cloud-native technologies, enabling dynamic policy enforcement across distributed environments without reliance on traditional network boundaries. The flexibility in Zero Trust allows seamless integration with diverse platforms and continuous verification of user and device identity, optimizing protection against complex cybersecurity threats.
Cost Implications and Resource Allocation
On-premises infrastructure demands significant upfront capital expenditure for hardware acquisition, maintenance, and dedicated IT personnel, leading to increased operational costs over time. Zero Trust Architecture, leveraging cloud-native solutions and automation, reduces physical resource dependencies and optimizes personnel allocation by minimizing manual security management. Organizations benefit from scalable cost models and more efficient resource distribution, aligning expenditures closely with actual usage and security needs.
Migration Strategies: From On-Premises to Zero Trust
Migrating from on-premises infrastructure to a Zero Trust Architecture involves comprehensive network segmentation and enforcing strict access controls at every layer. Organizations should implement identity-centric security models, including multi-factor authentication (MFA) and continuous validation, to replace traditional perimeter-based defenses. Adopting cloud-native tools and integrating endpoint detection and response (EDR) solutions enable a seamless transition while maintaining security posture throughout the migration process.
Related Important Terms
Micro-Segmentation
Micro-segmentation in Zero Trust Architecture enforces granular security policies within on-premises environments by isolating workloads and limiting lateral movement, significantly reducing the attack surface. Unlike traditional perimeter-based models, micro-segmentation provides dynamic, context-aware controls that elevate protection for sensitive data and critical applications in hybrid infrastructure setups.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) provides a dynamic, identity-centric approach to network security, contrasting with traditional on-premises architectures by cloaking critical assets and granting access strictly based on verified user and device credentials. SDP minimizes attack surfaces and enhances security posture through real-time authentication and authorization, aligning with Zero Trust principles that eliminate implicit trust within network boundaries.
Policy-Based Access Control (PBAC)
Policy-Based Access Control (PBAC) in On-Premises environments relies on static rules tied to physical network boundaries, limiting dynamic response to evolving threats. Zero Trust Architecture leverages PBAC with continuous evaluation of policies based on user identity, device state, and context, enabling granular, adaptive access control beyond traditional perimeter defenses.
Continuous Authentication
On-premises environments typically rely on static perimeter-based security models, which can limit the effectiveness of continuous authentication by trusting users once they are inside the network. Zero Trust Architecture enforces continuous authentication by constantly verifying user identities and device health through real-time analytics and adaptive access policies, reducing the risk of lateral movement and insider threats.
Identity-Centric Security
On-premises security relies heavily on network perimeter defenses, whereas Zero Trust Architecture emphasizes continuous identity verification and least-privilege access across all devices and users. Identity-centric security in Zero Trust reduces attack surfaces by enforcing strict authentication protocols and real-time context-aware access control regardless of the network location.
East-West Traffic Inspection
East-West traffic inspection in on-premises environments relies heavily on internal firewalls and network segmentation, often creating security gaps due to lateral movement threats within the data center. Zero Trust Architecture enhances East-West traffic inspection by enforcing strict identity verification, micro-segmentation, and continuous monitoring, reducing attack surfaces and preventing unauthorized access between workloads.
Network De-perimeterization
On-premises networks rely on traditional perimeter-based security models, creating distinct boundaries that separate trusted internal environments from untrusted external ones; zero trust architecture eliminates this perimeter, enforcing continuous verification and least-privilege access regardless of location. Network de-perimeterization enables granular micro-segmentation, adaptive authentication, and real-time threat detection to reduce lateral movement and elevate overall cybersecurity resilience.
Secure Access Service Edge (SASE)
Secure Access Service Edge (SASE) integrates networking and security functions into a unified cloud-native service, surpassing traditional on-premises architectures by delivering scalable, identity-driven secure access regardless of user location. Zero Trust Architecture within SASE enforces strict verification for every access attempt, minimizing attack surfaces and enhancing protection against lateral threats compared to conventional perimeter-based security models.
Just-In-Time (JIT) Access
Just-In-Time (JIT) Access in Zero Trust Architecture minimizes exposure by granting users temporary, precise permissions only when needed, contrasting with traditional On-Premises models that often rely on persistent access rights. This dynamic access control reduces attack surfaces and enhances security posture by enforcing least-privilege principles at granular levels.
Adaptive Trust Model
The Adaptive Trust Model in Zero Trust Architecture dynamically evaluates user behavior, device health, and contextual risk factors in real-time, contrasting with traditional On-Premises security that relies on static perimeter defenses. This approach enables granular access control and continuous verification, significantly reducing vulnerabilities associated with fixed trust boundaries.
On-Premises vs Zero Trust Architecture Infographic
 industrydif.com
industrydif.com