Traditional backup systems store data copies that can be altered or deleted, making them vulnerable to ransomware attacks and accidental corruption. Immutable backup solutions create unchangeable, tamper-proof copies of data that ensure integrity and protect against data loss. This immutability feature is crucial for maintaining reliable recovery points in disaster recovery and cybersecurity strategies.
Table of Comparison
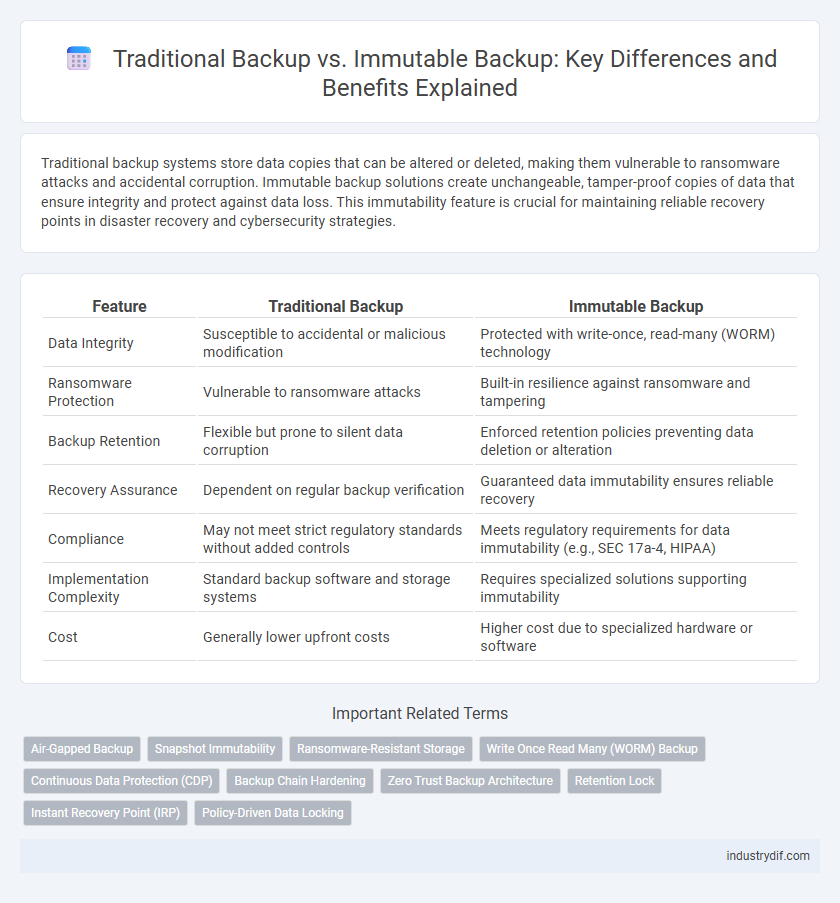
| Feature | Traditional Backup | Immutable Backup |
|---|---|---|
| Data Integrity | Susceptible to accidental or malicious modification | Protected with write-once, read-many (WORM) technology |
| Ransomware Protection | Vulnerable to ransomware attacks | Built-in resilience against ransomware and tampering |
| Backup Retention | Flexible but prone to silent data corruption | Enforced retention policies preventing data deletion or alteration |
| Recovery Assurance | Dependent on regular backup verification | Guaranteed data immutability ensures reliable recovery |
| Compliance | May not meet strict regulatory standards without added controls | Meets regulatory requirements for data immutability (e.g., SEC 17a-4, HIPAA) |
| Implementation Complexity | Standard backup software and storage systems | Requires specialized solutions supporting immutability |
| Cost | Generally lower upfront costs | Higher cost due to specialized hardware or software |
Definition of Traditional Backup
Traditional backup refers to the process of creating copies of data that can be restored in case of data loss, corruption, or disaster. These backups are typically stored on external drives, tape libraries, or cloud storage, offering recoverability through periodic snapshots or full data duplication. While effective for recovering deleted or corrupted files, traditional backups are vulnerable to ransomware attacks and accidental deletion since the backup data can be altered or erased.
Definition of Immutable Backup
Immutable backup refers to a data storage method where backup files are written once and cannot be altered or deleted by any user or software, ensuring complete data integrity. Unlike traditional backups, which can be modified or accidentally overwritten, immutable backups provide a secure and tamper-proof solution against ransomware and human error. This technology typically leverages Write Once Read Many (WORM) storage or blockchain frameworks to guarantee data immutability.
Key Differences Between Traditional and Immutable Backup
Traditional backup relies on periodic copies stored on rewritable media, which can be vulnerable to accidental deletion, corruption, or ransomware attacks. Immutable backup stores data in a way that prevents alteration or deletion within a specified retention period, ensuring data integrity and security. Key differences include immutability enforcement, protection against ransomware, and compliance with regulatory data retention requirements.
Data Integrity and Tamper Resistance
Traditional backup methods often struggle with vulnerabilities that allow unauthorized modifications, compromising data integrity and increasing the risk of tampering during storage or transmission. Immutable backup solutions ensure data remains unaltered through write-once, read-many (WORM) technologies and cryptographic hashing, providing robust tamper resistance and preserving authenticity. These immutable systems enhance compliance with data protection regulations by maintaining verifiable, unchangeable copies, critical for disaster recovery and forensic analysis.
Ransomware Protection Capabilities
Traditional backup systems often store data in a manner vulnerable to ransomware attacks, as backup files can be altered or deleted by malicious actors. Immutable backup technology ensures that once data is written, it cannot be modified or erased within a specified retention period, providing a robust defense against ransomware encryption or deletion attempts. This immutability feature significantly enhances data recovery reliability and reduces downtime during ransomware incidents.
Compliance and Regulatory Considerations
Traditional backups often face challenges in meeting stringent compliance and regulatory requirements due to their susceptibility to data alteration or deletion. Immutable backups provide a secure, tamper-proof solution by ensuring data cannot be modified or erased within a defined retention period, aligning with regulations such as GDPR, HIPAA, and SOX. Organizations leveraging immutable backup technology enhance audit readiness and reduce legal risks associated with data integrity breaches.
Storage Architecture Comparison
Traditional backup storage architecture relies on overwritable media such as magnetic tapes or hard drives, which are susceptible to accidental deletion and ransomware attacks. Immutable backup storage, often implemented using Write Once Read Many (WORM) technology or blockchain-based ledgers, ensures data cannot be altered or deleted once written, providing enhanced data integrity and security. Storage systems for immutable backups typically utilize object storage with built-in versioning and cryptographic sealing to maintain tamper-proof records.
Recovery Speed and Reliability
Immutable backups significantly enhance recovery speed and reliability by preventing data alteration or deletion, ensuring data integrity during restoration processes. Traditional backups, while flexible, often suffer from slower recovery times and increased risk of data corruption or ransomware attacks compromising backup sets. Utilizing immutable backup solutions reduces downtime and bolsters data protection, critical for maintaining business continuity in disaster recovery scenarios.
Cost Implications and Resource Requirements
Traditional backup solutions often incur higher costs due to ongoing storage expenses, increased maintenance, and resource-intensive management that require frequent updates and vulnerability patches. Immutable backup systems reduce long-term expenses by ensuring data integrity with write-once, read-many (WORM) technology, minimizing risks of ransomware attacks and costly data recovery efforts. Resource requirements for immutable backups are streamlined by automated protection mechanisms, lowering the demand for manual oversight and operational overhead associated with traditional backup environments.
Future Trends in Backup Technologies
Traditional backup methods rely on periodic snapshots vulnerable to ransomware attacks, whereas immutable backup solutions ensure data integrity by preventing modification or deletion once stored. Advances in blockchain-based storage and AI-driven anomaly detection are driving future trends, enhancing backup security and automation. Cloud-native immutable backups with decentralized verification mechanisms are gaining traction for robust disaster recovery strategies.
Related Important Terms
Air-Gapped Backup
Traditional backups often store data in environments susceptible to cyber threats, whereas immutable backups ensure data integrity by preventing any modifications or deletions once written. Air-gapped backup solutions further enhance security by physically isolating the backup from network access, making them resilient against ransomware attacks and unauthorized tampering.
Snapshot Immutability
Snapshot immutability in traditional backup systems often allows data to be altered or deleted after creation, increasing vulnerability to ransomware and accidental modifications. Immutable backups enforce write-once, read-many (WORM) policies at the snapshot level, ensuring data integrity and tamper resistance by preventing any changes or deletions until a predefined retention period expires.
Ransomware-Resistant Storage
Immutable backup storage offers a significant advantage over traditional backup by preventing ransomware from modifying or deleting backup data, ensuring data integrity even during cyberattacks. Traditional backups are vulnerable to ransomware encryption and deletion, whereas immutable backups use write-once-read-many (WORM) technology to create ransomware-resistant storage that preserves critical data for recovery.
Write Once Read Many (WORM) Backup
Traditional backup systems often allow data modification or deletion post-backup, posing risks to data integrity and compliance, while immutable backup solutions leverage Write Once Read Many (WORM) technology to ensure data remains unaltered and tamper-proof. WORM backup enforces a strict, non-rewriteable storage layer that secures critical information against ransomware attacks and accidental deletion, enhancing long-term data retention and regulatory adherence.
Continuous Data Protection (CDP)
Traditional backup systems perform periodic data snapshots prone to data loss between intervals, while immutable backup solutions leverage Continuous Data Protection (CDP) to capture every data change in real-time, ensuring complete recoverability and tamper-proof record integrity. CDP's real-time data replication and write-once, read-many (WORM) storage architecture enhance ransomware resilience and reduce recovery point objectives (RPOs) compared to conventional backup methodologies.
Backup Chain Hardening
Immutable backup enhances backup chain hardening by preventing unauthorized alterations or deletions within the backup sequence, ensuring data integrity and security. Traditional backup methods lack this tamper-resistant feature, making the backup chain vulnerable to ransomware attacks and accidental data corruption.
Zero Trust Backup Architecture
Immutable backup solutions enhance zero trust backup architecture by ensuring data integrity through write-once, read-many (WORM) storage that prevents unauthorized alterations or deletions. Unlike traditional backup methods vulnerable to ransomware and insider threats, immutable backups leverage cryptographic hashes and strict access controls to maintain tamper-proof recovery points.
Retention Lock
Retention Lock in immutable backups ensures data cannot be altered or deleted within a predefined retention period, enhancing security and regulatory compliance compared to traditional backups where data can be modified or erased. This immutable feature protects against ransomware attacks and accidental data loss by enforcing strict retention policies at the storage layer.
Instant Recovery Point (IRP)
Traditional backup systems rely on periodic snapshots that can lead to significant recovery time objectives (RTOs), whereas immutable backup solutions enable Instant Recovery Points (IRPs) by ensuring data cannot be altered or deleted, drastically reducing RTOs. Immutable backups maintain data integrity through cryptographic hashes and write-once-read-many (WORM) technology, providing faster, tamper-proof recovery in critical failure scenarios.
Policy-Driven Data Locking
Policy-driven data locking in immutable backup ensures that data cannot be altered or deleted within a predefined retention period, providing enhanced protection against ransomware and accidental deletion compared to traditional backups. This approach enforces strict compliance and audit trails by automating immutable storage policies at the software or hardware level, significantly improving data integrity and security frameworks.
Traditional Backup vs Immutable Backup Infographic
 industrydif.com
industrydif.com