On-Premises network architectures provide localized control over data and security but often face challenges with scalability and remote access management. Zero Trust Network models eliminate implicit trust by continuously verifying users and devices, enhancing security across distributed environments and hybrid infrastructures. Combining zero trust principles with on-premises systems delivers robust protection while maintaining organizational control over critical resources.
Table of Comparison
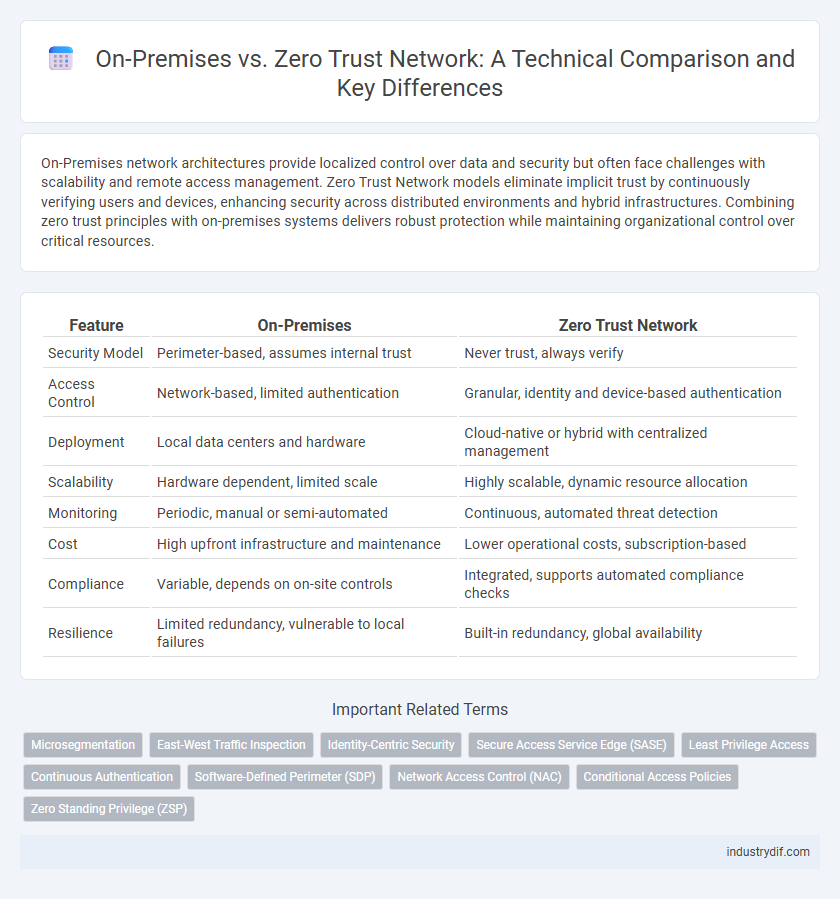
| Feature | On-Premises | Zero Trust Network |
|---|---|---|
| Security Model | Perimeter-based, assumes internal trust | Never trust, always verify |
| Access Control | Network-based, limited authentication | Granular, identity and device-based authentication |
| Deployment | Local data centers and hardware | Cloud-native or hybrid with centralized management |
| Scalability | Hardware dependent, limited scale | Highly scalable, dynamic resource allocation |
| Monitoring | Periodic, manual or semi-automated | Continuous, automated threat detection |
| Cost | High upfront infrastructure and maintenance | Lower operational costs, subscription-based |
| Compliance | Variable, depends on on-site controls | Integrated, supports automated compliance checks |
| Resilience | Limited redundancy, vulnerable to local failures | Built-in redundancy, global availability |
Introduction to On-Premises and Zero Trust Network
On-Premises infrastructure refers to IT systems and hardware physically located within an organization's facility, providing direct control over data and resources. Zero Trust Network architecture eliminates implicit trust by continuously verifying user identities and device compliance regardless of location or network perimeter. Combining On-Premises environments with Zero Trust principles enhances security through strict access controls and comprehensive threat detection.
Core Principles of On-Premises Security
On-premises security relies heavily on physical control, where all hardware and data remain within the organization's infrastructure, ensuring direct oversight and protection against external threats. Core principles include network segmentation, strict perimeter defenses such as firewalls, and controlled internal access using role-based authentication to prevent unauthorized entry. This traditional approach depends on the assumption that threats primarily exist outside the network, making internal users inherently trusted.
Foundational Concepts of Zero Trust Network
Zero Trust Network (ZTN) architecture eliminates implicit trust by continuously verifying each user, device, and connection before granting access, unlike traditional on-premises models that rely heavily on perimeter security. Core principles include least privilege access, micro-segmentation, and strong authentication methods such as multi-factor authentication (MFA) to reduce attack surfaces. This foundational shift ensures that internal and external network traffic receives equal scrutiny, enhancing security posture in complex, modern IT environments.
Key Differences Between On-Premises and Zero Trust
On-Premises networks rely on perimeter-based security, granting access primarily within a defined physical network, while Zero Trust Networks enforce strict verification of every user and device regardless of location. Zero Trust architecture emphasizes continuous authentication, micro-segmentation, and minimal access privileges, contrasting with the broader trust zones in traditional on-premises setups. This shift enhances protection against insider threats and lateral movement by attackers within the network.
Authentication Mechanisms: Legacy vs Modern Approaches
On-premises authentication mechanisms primarily rely on legacy protocols such as LDAP and Kerberos, which often present vulnerabilities due to static credentials and limited multi-factor support. Zero Trust Network models emphasize modern approaches like continuous authentication, adaptive risk-based verification, and integration with identity providers supporting OAuth and SAML protocols. These advanced methods significantly enhance security by minimizing trust assumptions and enforcing granular access controls based on real-time context.
Access Control Strategies in On-Premises vs Zero Trust
On-premises access control relies on perimeter-based security models, granting users network access based on physical location or IP ranges. Zero Trust Network architecture enforces strict identity verification for every access request, minimizing implicit trust and applying least-privilege principles. This shift from network-centric to identity-centric access control enhances security against insider threats and lateral movement.
Scalability and Flexibility: Comparative Analysis
On-premises network architectures often face limitations in scalability due to physical infrastructure constraints and capital expenditure requirements, restricting rapid adaptation to evolving business needs. Zero Trust Network models offer enhanced flexibility by leveraging cloud-native technologies and micro-segmentation, enabling seamless scaling across distributed environments without compromising security. This approach supports dynamic access policies and real-time monitoring, accommodating fluctuating workloads and diverse device ecosystems more effectively than traditional on-premises setups.
Impact on Compliance and Regulatory Requirements
On-premises network architectures often require extensive manual controls and audits to meet compliance standards such as HIPAA, GDPR, or SOX, potentially increasing the risk of human error and gaps in regulatory adherence. Zero Trust Network models inherently enforce strict access controls and continuous verification, aligning more naturally with regulatory requirements for data protection and minimizing the attack surface. Adopting Zero Trust can streamline compliance management by automating policy enforcement and providing detailed logging for audit trails.
Challenges and Risks in Migrating to Zero Trust
Migrating from traditional on-premises infrastructure to a Zero Trust Network introduces challenges such as complexity in integrating legacy systems and ensuring continuous authentication across diverse endpoints. Risks include potential misconfigurations that can lead to security gaps, increased latency from stringent access controls, and user resistance due to changes in access protocols. Effective migration requires comprehensive planning, robust identity governance, and thorough testing to mitigate these operational and security risks.
Future Trends in Network Security Architectures
Future trends in network security architectures emphasize a shift from traditional on-premises models to Zero Trust frameworks, driven by increasing cloud adoption and sophisticated cyber threats. Zero Trust Network architectures prioritize continuous verification, least privilege access, and micro-segmentation to mitigate risks more effectively than perimeter-based defenses. Emerging technologies such as AI-powered threat detection and adaptive access controls enhance the scalability and resilience of Zero Trust implementations in dynamic IT environments.
Related Important Terms
Microsegmentation
Microsegmentation enhances security in both On-Premises and Zero Trust Network architectures by isolating workloads and controlling east-west traffic within data centers. Zero Trust Network leverages microsegmentation to enforce strict, identity-based access policies, reducing lateral movement risks compared to traditional On-Premises models.
East-West Traffic Inspection
East-West traffic inspection within an on-premises network typically relies on internal firewalls and segmentation to monitor lateral movement, whereas Zero Trust Network architectures enforce strict identity verification and micro-segmentation for continuous validation of every internal request. This approach reduces the attack surface by treating all internal traffic as untrusted, enhancing detection and mitigation of insider threats and lateral breaches.
Identity-Centric Security
On-premises security relies heavily on perimeter defenses with identity management often siloed within internal networks, whereas Zero Trust Network Architecture (ZTNA) enforces strict identity-centric security by continuously verifying user credentials and device trust regardless of location. This approach minimizes insider threats and lateral movement by implementing least-privilege access policies based on dynamic, context-aware identity attributes.
Secure Access Service Edge (SASE)
Secure Access Service Edge (SASE) integrates comprehensive security functions with wide-area networking to provide secure, scalable access, overcoming traditional on-premises limitations. Unlike zero trust networks confined to internal resources, SASE delivers consistent, context-aware protection across cloud, edge, and remote environments, optimizing performance and security.
Least Privilege Access
On-premises architectures often rely on perimeter-based security, limiting Least Privilege Access enforcement compared to Zero Trust Network models that continuously verify and restrict user permissions based on real-time risk assessments. Zero Trust frameworks implement granular access controls, ensuring users and devices operate strictly within the bounds of their assigned privileges to minimize potential attack surfaces.
Continuous Authentication
Continuous authentication within Zero Trust Network architecture leverages real-time monitoring of user behavior and device posture to dynamically verify identity, minimizing risks associated with static credentials in traditional on-premises environments. This proactive security approach ensures persistent validation without relying solely on perimeter defenses, enhancing protection against unauthorized access in complex IT infrastructures.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) enhances traditional on-premises networks by creating dynamic, context-aware access controls that reduce attack surfaces through user and device identity verification before granting network entry. Unlike rigid on-premises infrastructures, SDP implements zero trust principles by enforcing continuous authentication and micro-segmentation, ensuring secure, least-privilege access to applications regardless of the user's location.
Network Access Control (NAC)
On-premises Network Access Control (NAC) solutions provide direct management of device authentication and policy enforcement within a local infrastructure, ensuring strict perimeter security and granular control. Zero Trust Network Access (ZTNA) eliminates implicit trust by continuously verifying user and device identities across hybrid environments, enhancing NAC effectiveness through dynamic, context-aware access policies.
Conditional Access Policies
Conditional Access Policies in On-Premises environments rely heavily on network perimeter controls and static IP whitelisting, limiting flexibility and increasing administrative overhead. In contrast, Zero Trust Network architectures implement dynamic, context-aware Conditional Access Policies based on user identity, device health, and continuous risk assessment to enhance security and reduce unauthorized access.
Zero Standing Privilege (ZSP)
Zero Standing Privilege (ZSP) within Zero Trust Network architecture eliminates persistent access rights by granting permissions dynamically based on real-time verification, significantly reducing the attack surface compared to traditional on-premises systems with static privilege assignments. ZSP enforces least-privilege access policies through continuous authentication and authorization, enhancing security posture by minimizing insider threats and lateral movement risks inherent in conventional network models.
On-Premises vs Zero Trust Network Infographic
 industrydif.com
industrydif.com