Penetration testing involves authorized, methodical attempts to exploit security vulnerabilities within a system, typically conducted by professional ethical hackers under a predefined scope. Bug bounty programs invite a broad community of independent researchers to identify and report security flaws in exchange for rewards, leveraging diverse perspectives to uncover hidden weaknesses. Both approaches complement each other by combining controlled, in-depth analysis with crowd-sourced vulnerability discovery to strengthen overall cybersecurity defenses.
Table of Comparison
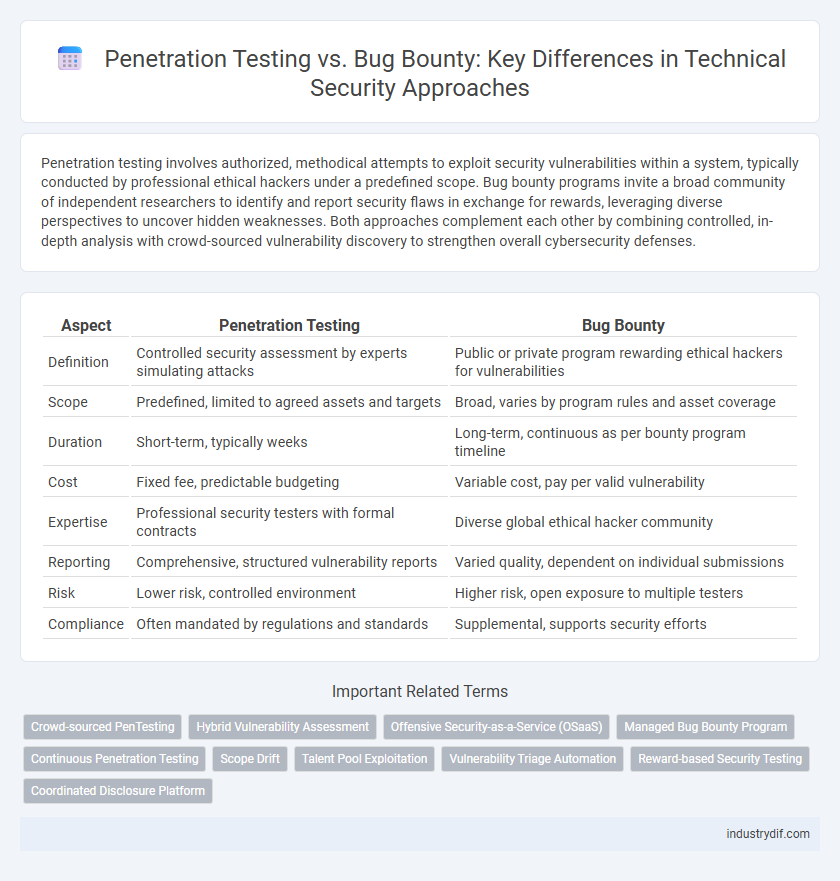
| Aspect | Penetration Testing | Bug Bounty |
|---|---|---|
| Definition | Controlled security assessment by experts simulating attacks | Public or private program rewarding ethical hackers for vulnerabilities |
| Scope | Predefined, limited to agreed assets and targets | Broad, varies by program rules and asset coverage |
| Duration | Short-term, typically weeks | Long-term, continuous as per bounty program timeline |
| Cost | Fixed fee, predictable budgeting | Variable cost, pay per valid vulnerability |
| Expertise | Professional security testers with formal contracts | Diverse global ethical hacker community |
| Reporting | Comprehensive, structured vulnerability reports | Varied quality, dependent on individual submissions |
| Risk | Lower risk, controlled environment | Higher risk, open exposure to multiple testers |
| Compliance | Often mandated by regulations and standards | Supplemental, supports security efforts |
Definition of Penetration Testing
Penetration testing is a systematic, authorized simulation of cyberattacks performed to identify and exploit vulnerabilities within an organization's IT infrastructure, aiming to assess security weaknesses before malicious actors can. This method utilizes structured techniques such as network scanning, vulnerability assessment, and exploitation attempts conducted by certified ethical hackers under predefined scopes and rules. Results from penetration tests provide actionable insights for enhancing defensive measures, ensuring compliance with industry security standards, and mitigating risk exposure effectively.
Understanding Bug Bounty Programs
Bug bounty programs harness a global network of ethical hackers who identify vulnerabilities in software and systems, providing real-time feedback for continuous security improvement. These programs complement traditional penetration testing by offering diverse perspectives and various attack methodologies beyond scheduled assessments. Organizations benefit from scalable, cost-effective security testing that uncovers issues before malicious actors exploit them.
Key Differences Between Pen Testing and Bug Bounties
Penetration testing involves a controlled, time-bound assessment conducted by security professionals using predefined scopes and methodologies to identify vulnerabilities. Bug bounty programs leverage a diverse, global community of ethical hackers who continuously search for security flaws in exchange for rewards, offering broader coverage and real-world attack perspectives. While pen testing provides depth with comprehensive analysis and formal reporting, bug bounties offer scalability and ongoing discovery of emerging threats.
Methodologies in Penetration Testing
Penetration testing employs a structured methodology involving reconnaissance, vulnerability scanning, exploitation, and post-exploitation analysis to systematically identify security weaknesses in a controlled environment. Tools such as Nmap, Metasploit, and Burp Suite are utilized to simulate real-world attack scenarios in alignment with industry standards like OWASP and PTES. This approach contrasts with bug bounty programs, which leverage crowd-sourced testing by diverse security researchers to uncover vulnerabilities in various applications over time.
Scope and Approach in Bug Bounty Programs
Bug bounty programs feature an open scope that invites diverse security researchers to identify vulnerabilities across multiple products or services, fostering continuous and real-world testing scenarios. This crowdsourced approach contrasts with the predefined, often limited scope of traditional penetration testing, enabling broader coverage and dynamic threat detection. Rewards are performance-based, incentivizing detailed, innovative exploit discovery and encouraging ongoing engagement beyond fixed testing periods.
Risks and Security Considerations
Penetration testing involves controlled, authorized simulations of cyberattacks designed to identify security vulnerabilities within a defined scope, minimizing unexpected risks by following strict protocols. Bug bounty programs leverage a diverse pool of external security researchers, increasing the chances of discovering unknown threats but introducing challenges such as variable testing quality and potential exposure to uncoordinated disclosures. Organizations must carefully balance the predictable, methodical approach of penetration testing against the wide-reaching, incentive-driven nature of bug bounties while implementing robust guidelines and legal frameworks to mitigate risks and protect sensitive data.
Cost Comparison: Pen Testing vs Bug Bounty
Penetration testing typically involves a fixed cost for a predefined scope and duration, which can range from $4,000 to $30,000 depending on the complexity and size of the target system. Bug bounty programs operate on a pay-for-results model, where organizations pay rewards based on the severity of vulnerabilities found, often leading to variable expenses that can scale with the program's popularity and coverage. Cost efficiency depends on the organization's risk tolerance and testing frequency, as penetration testing provides predictable budgeting while bug bounty programs potentially offer broader vulnerability discovery at fluctuating costs.
Skills and Expertise Required
Penetration testing demands advanced knowledge of network protocols, system vulnerabilities, and exploit development, requiring specialized certifications like OSCP or CEH. Bug bounty programs favor diverse skill sets, encouraging expertise in web application security, mobile platforms, and creative vulnerability discovery methods. Both approaches necessitate strong problem-solving abilities, but penetration testers often work within structured methodologies, while bug bounty hunters rely on independent research and adaptability.
Reporting and Remediation Processes
Penetration testing typically involves a structured reporting process with detailed vulnerability documentation, risk assessments, and prioritized remediation recommendations issued by certified professionals within a fixed engagement period. Bug bounty programs rely on continuous, crowd-sourced reporting through a platform where ethical hackers submit findings that are validated before being communicated to the development team for patching. Both approaches emphasize clear remediation workflows, but penetration testing often provides a more comprehensive, deadline-driven assessment, whereas bug bounty offers ongoing coverage and diverse vulnerability discovery.
Choosing the Right Approach for Your Organization
Penetration testing offers a structured, time-bound assessment by cybersecurity experts simulating attacker behavior, ideal for organizations needing comprehensive vulnerability analysis within a defined scope. Bug bounty programs leverage a diverse global community of ethical hackers who continuously search for vulnerabilities, providing dynamic and ongoing threat detection beneficial for companies aiming to enhance security posture over time. Selecting the right approach depends on factors such as budget, risk tolerance, compliance requirements, and the desired frequency of security evaluations.
Related Important Terms
Crowd-sourced PenTesting
Crowd-sourced penetration testing leverages a diverse pool of ethical hackers to identify vulnerabilities, providing broader coverage and real-world attack perspectives compared to traditional pen testing engagements. This approach enhances security by continuously uncovering critical bugs through diverse skill sets, making bug bounty programs an effective complement to structured penetration testing methodologies.
Hybrid Vulnerability Assessment
Hybrid Vulnerability Assessment integrates the structured approach of penetration testing with the diverse, real-world insights from bug bounty programs, enhancing the identification and remediation of security flaws. This combination maximizes coverage by leveraging both controlled internal expertise and external crowd-sourced talent, improving overall system resilience against cyber threats.
Offensive Security-as-a-Service (OSaaS)
Penetration Testing provides structured, periodic assessments by certified professionals identifying critical vulnerabilities, while Bug Bounty leverages a global community of ethical hackers offering continuous real-time threat detection. Offensive Security-as-a-Service (OSaaS) integrates automated tools and expert insights to deliver scalable, proactive security measures combining the benefits of both methodologies.
Managed Bug Bounty Program
Managed Bug Bounty Programs offer continuous vulnerability discovery through a curated pool of ethical hackers, providing scalable and diverse security assessments compared to traditional penetration testing's fixed-scope, time-bound evaluations. These programs integrate real-time threat intelligence and reward-driven motivation, enhancing identification of critical zero-day exploits and improving overall application security posture.
Continuous Penetration Testing
Continuous penetration testing offers a proactive approach by regularly simulating cyberattacks to identify vulnerabilities before they can be exploited. Unlike traditional bug bounty programs that rely on external contributors reporting findings sporadically, continuous testing integrates automated tools and scheduled assessments into the security lifecycle, enhancing overall risk management and compliance.
Scope Drift
Penetration testing offers a predefined, controlled scope which minimizes scope drift by clearly establishing boundaries before engagement, while bug bounty programs inherently risk scope creep due to their open-ended nature and continuous submission of vulnerabilities from a diverse researcher base. Effective management of scope drift in bug bounty initiatives requires rigorous scope definition, real-time monitoring, and dynamic adjustment of program parameters to maintain focus on critical assets.
Talent Pool Exploitation
Penetration testing engages a specialized, often limited pool of certified security professionals, providing focused but constrained expertise for vulnerability assessment. Bug bounty programs harness a vast, diverse global talent pool of ethical hackers, enabling broader exploitation of skills and perspectives to uncover a wider range of security flaws.
Vulnerability Triage Automation
Penetration testing offers structured, scheduled assessments with controlled scope, while bug bounty programs harness diverse external expertise for continuous vulnerability discovery; integrating automated vulnerability triage accelerates prioritization and remediation by systematically categorizing findings based on severity, exploitability, and context. Leveraging machine learning algorithms and AI-driven platforms in triage automation reduces false positives and enhances the efficiency of both penetration testing and bug bounty workflows.
Reward-based Security Testing
Reward-based security testing distinguishes penetration testing and bug bounty programs by compensation structure and scope; penetration testing typically involves fixed-price assignments with predefined targets, whereas bug bounty programs offer variable rewards based on vulnerability severity and impact discovered in live environments. This performance-based incentive model in bug bounties encourages continuous, real-world exploitation attempts, leveraging a diverse pool of ethical hackers to enhance an organization's security posture dynamically.
Coordinated Disclosure Platform
A Coordinated Disclosure Platform streamlines vulnerability reporting by enabling security researchers and organizations to collaborate securely, ensuring timely remediation of discovered flaws. Penetration testing provides structured, controlled assessments, while bug bounty programs leverage diverse external expertise through continuous, incentive-driven vulnerability discovery on such platforms.
Penetration Testing vs Bug Bounty Infographic
 industrydif.com
industrydif.com