VPNs create secure tunnels for remote access by encrypting data between users and networks, primarily protecting point-to-point connections. SASE integrates network security functions such as secure web gateways, firewall as a service, and zero-trust network access into a cloud-delivered service, offering comprehensive security with improved scalability and reduced latency. Unlike VPNs, SASE provides dynamic access control and continuous risk assessment, making it more suited for modern, distributed work environments.
Table of Comparison
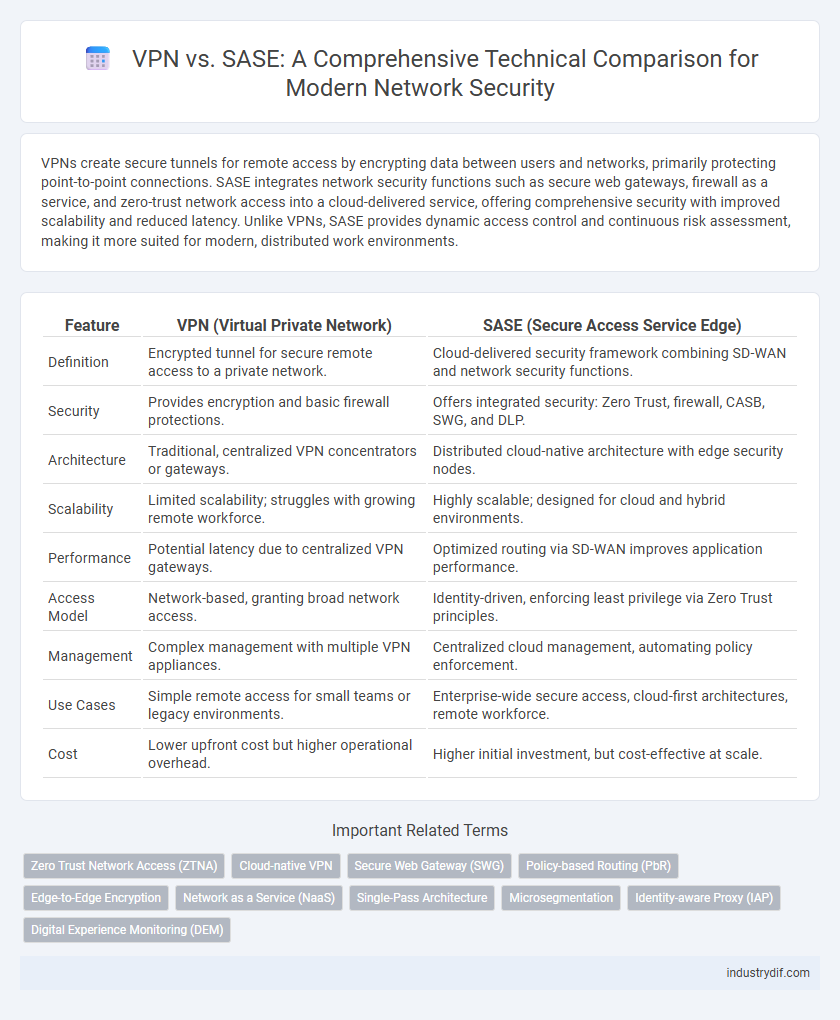
| Feature | VPN (Virtual Private Network) | SASE (Secure Access Service Edge) |
|---|---|---|
| Definition | Encrypted tunnel for secure remote access to a private network. | Cloud-delivered security framework combining SD-WAN and network security functions. |
| Security | Provides encryption and basic firewall protections. | Offers integrated security: Zero Trust, firewall, CASB, SWG, and DLP. |
| Architecture | Traditional, centralized VPN concentrators or gateways. | Distributed cloud-native architecture with edge security nodes. |
| Scalability | Limited scalability; struggles with growing remote workforce. | Highly scalable; designed for cloud and hybrid environments. |
| Performance | Potential latency due to centralized VPN gateways. | Optimized routing via SD-WAN improves application performance. |
| Access Model | Network-based, granting broad network access. | Identity-driven, enforcing least privilege via Zero Trust principles. |
| Management | Complex management with multiple VPN appliances. | Centralized cloud management, automating policy enforcement. |
| Use Cases | Simple remote access for small teams or legacy environments. | Enterprise-wide secure access, cloud-first architectures, remote workforce. |
| Cost | Lower upfront cost but higher operational overhead. | Higher initial investment, but cost-effective at scale. |
Defining VPN and SASE: Key Technical Concepts
Virtual Private Network (VPN) is a technology that creates a secure, encrypted tunnel over the internet to connect remote users to a private network, ensuring data confidentiality and integrity. Secure Access Service Edge (SASE) is an integrated cloud-native framework combining wide area networking (WAN) and comprehensive security services such as Zero Trust Network Access (ZTNA), firewall-as-a-service (FWaaS), and secure web gateways (SWG). Unlike traditional VPNs, SASE delivers identity-driven, context-aware access control and security policies at the edge, optimizing performance and enhancing threat protection across distributed environments.
Architectural Differences Between VPN and SASE
VPNs create secure point-to-point connections through encrypted tunnels, primarily focusing on remote access to a specific network, whereas SASE integrates WAN capabilities with comprehensive cloud-delivered security services, including zero trust network access (ZTNA), secure web gateways, and firewall-as-a-service. VPN architecture relies on centralized data flow through corporate gateways, often leading to bottlenecks and limited scalability. In contrast, SASE shifts security enforcement to the cloud edge, enabling distributed policy enforcement and improved performance across global locations and remote users.
Security Protocols: VPN vs SASE
VPNs typically rely on protocols such as IPSec and SSL/TLS to create encrypted tunnels for secure remote access, but these can expose the network perimeter and provide broad access once connected. SASE integrates Zero Trust principles with security protocols like TLS 1.3 and Secure Web Gateways, enforcing continuous authentication and granular access controls at the cloud edge. This shift enhances protection against modern threats by verifying every user and device in real time, reducing lateral movement risk within the network.
Scalability and Performance Considerations
SASE (Secure Access Service Edge) outperforms traditional VPNs by offering cloud-native scalability, enabling seamless expansion across multiple locations without compromising speed or security. VPNs often struggle with increased latency and bandwidth limitations as user numbers grow, whereas SASE leverages distributed edge computing to enhance performance and reduce bottlenecks. Enterprises prioritizing agile, high-performance network access benefit from SASE's ability to dynamically allocate resources and maintain consistent service quality under heavy loads.
Network Access Control: Traditional vs Cloud-Native
Network Access Control (NAC) in VPN solutions typically relies on perimeter-based security models with predefined access rules, often limiting scalability and dynamic policy enforcement. Cloud-native SASE platforms integrate NAC by leveraging identity-driven, context-aware controls, enabling seamless and secure access across distributed environments. This shift from static to adaptive NAC improves threat detection and supports zero-trust architectures essential for modern enterprise networks.
Integration with Zero Trust Models
VPNs primarily offer secure remote access by creating encrypted tunnels but often lack comprehensive visibility and adaptive policy enforcement required for Zero Trust architectures. SASE integrates network security functions like secure web gateways, firewall-as-a-service, and zero trust network access (ZTNA) into a unified cloud-native framework, enabling granular access control based on user identity, device posture, and real-time risk assessment. This holistic approach aligns with Zero Trust principles by continuously validating trust and minimizing attack surfaces across distributed environments.
User Experience and Latency Comparisons
VPNs often lead to increased latency due to routing traffic through centralized data centers, which can degrade user experience, especially for remote or mobile employees. SASE architecture optimizes user experience by delivering security and networking functions closer to the user via cloud-native points of presence, substantially reducing latency. Real-world tests show SASE can decrease latency by up to 50% compared to traditional VPNs, improving application responsiveness and overall network performance.
Management and Monitoring Capabilities
VPNs primarily offer basic network access controls with limited visibility into user activity and device status, making centralized management challenging. SASE integrates security functions like firewall as a service, secure web gateways, and zero-trust network access with comprehensive monitoring dashboards, enabling real-time threat detection and policy enforcement across distributed environments. Advanced analytics and automated responses within SASE platforms enhance operational efficiency and simplify compliance reporting compared to traditional VPN management tools.
Compliance and Regulatory Impact
VPNs provide encrypted tunnels for secure remote access but often lack granular control and visibility, posing challenges for compliance with evolving data protection regulations such as GDPR and HIPAA. SASE integrates security and network functions, offering real-time policy enforcement, detailed audit trails, and automated compliance reporting, which simplifies adherence to regulatory frameworks. Organizations adopting SASE can ensure continuous compliance monitoring and reduce the risk of data breaches through context-aware access controls and centralized governance.
Future Trends in Secure Network Access
Future trends in secure network access emphasize the shift from traditional VPNs to Secure Access Service Edge (SASE) architectures, leveraging cloud-native security and zero-trust principles. SASE integrates networking and security functions such as SWG, CASB, and ZTNA, delivering enhanced scalability and reduced latency for remote users and IoT devices. The adoption of AI-driven threat detection within SASE frameworks facilitates proactive security, aligning with increasing demands for dynamic, context-aware access controls in hybrid and multi-cloud environments.
Related Important Terms
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) within SASE frameworks offers dynamic, identity-centric access controls that surpass traditional VPNs by minimizing attack surfaces and eliminating implicit trust for all users. Unlike VPNs that provide broad network access, ZTNA enforces granular, context-aware policies ensuring continuous verification and secure access only to authorized resources.
Cloud-native VPN
Cloud-native VPNs leverage scalable, distributed architectures to provide seamless, secure access to cloud resources, minimizing latency and improving user experience compared to traditional VPNs. SASE integrates cloud-native VPN capabilities with security services like SWG, CASB, and ZTNA to deliver a unified, edge-based security model optimized for modern hybrid and remote work environments.
Secure Web Gateway (SWG)
Secure Web Gateway (SWG) functionality within SASE frameworks offers advanced threat protection, real-time URL filtering, and data loss prevention that traditional VPNs lack, optimizing secure internet access for distributed workforces. SASE's cloud-native SWG enables scalable, low-latency security enforcement directly at the edge, surpassing VPN's reliance on centralized, hardware-based security gateways.
Policy-based Routing (PbR)
Policy-based routing (PbR) in VPNs directs traffic based on predetermined policies, often limited to static configurations that can hinder flexibility and scalability. SASE integrates dynamic PbR with cloud-native security, enabling adaptive traffic steering and real-time policy enforcement across distributed networks for enhanced performance and security.
Edge-to-Edge Encryption
Edge-to-edge encryption in VPNs secures data from the user device to the VPN gateway, but traffic beyond the gateway often remains exposed in the network core. SASE integrates edge-to-edge encryption across multiple points including cloud services and remote access, ensuring continuous data protection throughout the entire network path.
Network as a Service (NaaS)
Network as a Service (NaaS) within SASE frameworks provides scalable, cloud-native network connectivity with integrated security, surpassing traditional VPNs by enabling seamless access to distributed resources and improved performance. VPNs primarily offer secure remote access, but lack the dynamic, policy-driven orchestration and embedded security features inherent in SASE's NaaS model.
Single-Pass Architecture
Single-Pass Architecture in SASE processes security functions and network traffic through a unified platform, reducing latency and improving performance compared to traditional VPNs that route traffic through multiple discrete security layers. This streamlined approach enhances scalability, simplifies management, and ensures consistent policy enforcement across distributed environments.
Microsegmentation
Microsegmentation in SASE (Secure Access Service Edge) provides dynamic, granular security controls by isolating network segments based on identity and context, significantly reducing lateral movement risks compared to traditional VPN architectures. Unlike VPNs that offer broad tunnel-based access, SASE's cloud-native microsegmentation enforces zero-trust policies at the application level, enabling adaptive, scalable protection across distributed environments.
Identity-aware Proxy (IAP)
Identity-aware Proxy (IAP) in SASE frameworks enhances secure access by continuously validating user identity and device posture before granting application-level permissions, unlike traditional VPNs that provide broader network access without granular control. This granular, conditional access minimizes the attack surface and aligns with zero-trust security models, offering superior protection for cloud applications and sensitive resources.
Digital Experience Monitoring (DEM)
Digital Experience Monitoring (DEM) integrated with SASE provides real-time visibility into user performance and security across distributed networks, surpassing traditional VPNs that often lack comprehensive insights into application-level metrics and cloud resource interactions. SASE's cloud-native architecture enables seamless monitoring and optimization of digital experiences by correlating network, security, and application data, enhancing end-user satisfaction and operational efficiency.
VPN vs SASE Infographic
 industrydif.com
industrydif.com