Communications interception involves the direct monitoring and capture of voice, data, or signal transmissions to gather intelligence, often relying on physical or digital access to communication channels. Cyber Electromagnetic Activities (CEMA) extend beyond interception to include offensive and defensive operations targeting electromagnetic spectrum assets, such as jamming, spoofing, and cyber attacks against command and control systems. Both approaches are critical in modern defense strategies, with communications interception providing raw intelligence and CEMA enabling disruption or degradation of adversary electronic capabilities.
Table of Comparison
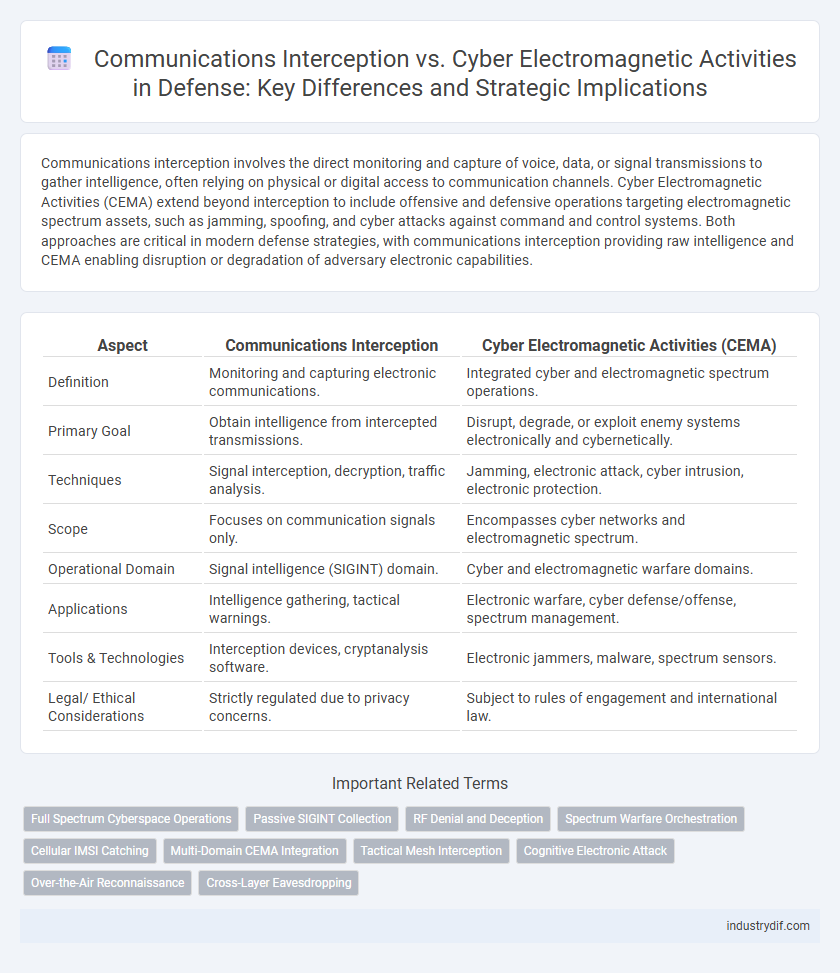
| Aspect | Communications Interception | Cyber Electromagnetic Activities (CEMA) |
|---|---|---|
| Definition | Monitoring and capturing electronic communications. | Integrated cyber and electromagnetic spectrum operations. |
| Primary Goal | Obtain intelligence from intercepted transmissions. | Disrupt, degrade, or exploit enemy systems electronically and cybernetically. |
| Techniques | Signal interception, decryption, traffic analysis. | Jamming, electronic attack, cyber intrusion, electronic protection. |
| Scope | Focuses on communication signals only. | Encompasses cyber networks and electromagnetic spectrum. |
| Operational Domain | Signal intelligence (SIGINT) domain. | Cyber and electromagnetic warfare domains. |
| Applications | Intelligence gathering, tactical warnings. | Electronic warfare, cyber defense/offense, spectrum management. |
| Tools & Technologies | Interception devices, cryptanalysis software. | Electronic jammers, malware, spectrum sensors. |
| Legal/ Ethical Considerations | Strictly regulated due to privacy concerns. | Subject to rules of engagement and international law. |
Introduction to Communications Interception and CEMA
Communications Interception involves the targeted monitoring and capturing of adversary transmissions to gain critical intelligence, enabling real-time situational awareness and threat assessment. Cyber Electromagnetic Activities (CEMA) integrate electronic warfare, cyber operations, and spectrum management to disrupt, exploit, and protect communications and information systems. Both disciplines are essential for modern defense strategies, enhancing operational superiority through the seamless collection and manipulation of electromagnetic and cyber domains.
Defining Communications Interception in Defense Operations
Communications interception in defense operations refers to the proactive monitoring and capturing of enemy transmissions, including voice, data, and signals, to gather critical intelligence. This process employs technologies such as radio frequency scanners, signal analyzers, and software-defined radios to extract actionable information without detection. Unlike cyber electromagnetic activities that encompass broader electronic warfare and cyber operations, communications interception specifically targets adversary communication channels to disrupt command and control capabilities.
Understanding Cyber Electromagnetic Activities (CEMA)
Cyber Electromagnetic Activities (CEMA) integrate cyber operations with electromagnetic spectrum capabilities to disrupt, deny, or exploit adversary communications and electronic systems. Unlike traditional communications interception, CEMA encompasses offensive and defensive actions across electronic warfare, cyber attacks, and electromagnetic spectrum management. Mastery of CEMA enables military forces to achieve information superiority by impairing enemy command and control networks while protecting their own.
Key Objectives: Communications Interception vs CEMA
Communications Interception aims to gather intelligence by covertly capturing and analyzing adversary signals, focusing on real-time information extraction and threat detection. Cyber Electromagnetic Activities (CEMA) integrate offensive and defensive cyber operations with electronic warfare to disrupt, degrade, or exploit enemy electromagnetic and information systems. The key objective of Communications Interception is intelligence acquisition, whereas CEMA prioritizes operational advantage through synchronized cyber and electromagnetic dominance.
Core Technologies and Tools Utilized
Communications interception relies heavily on advanced signal processing technologies, including radio frequency (RF) scanners, directional antennas, and encryption-breaking algorithms to capture and decode transmitted data. Cyber Electromagnetic Activities (CEMA) integrate electronic warfare tools, such as jamming devices, frequency spectrum analyzers, and cyber exploitation software, to disrupt or manipulate adversarial electromagnetic spectrum operations. Both domains increasingly utilize artificial intelligence and machine learning models to enhance real-time threat detection, data analysis, and adaptive response capabilities in complex electromagnetic environments.
Operational Scenarios: Tactical vs Strategic Implications
Communications interception primarily targets tactical scenarios by enabling real-time intelligence gathering from adversary communications, enhancing battlefield situational awareness and immediate decision-making. Cyber Electromagnetic Activities (CEMA), encompassing cyber operations, electronic warfare, and signals intelligence, extend their impact to both tactical and strategic levels by disrupting, deceiving, or exploiting enemy command-and-control networks and critical infrastructure. While communications interception offers localized battlefield gains, CEMA supports broader strategic objectives such as weakening adversary operational capabilities and shaping the electromagnetic spectrum to achieve long-term dominance.
Legal and Ethical Considerations in Modern Warfare
Communications interception involves monitoring and capturing data transmissions to gain intelligence, raising concerns about privacy rights and adherence to international laws such as the Geneva Conventions, which regulate wartime conduct. Cyber electromagnetic activities (CEMA) encompass offensive and defensive operations targeting enemy electronic systems, requiring stringent compliance with legal frameworks like the Tallinn Manual on the International Law Applicable to Cyber Warfare. Balancing operational effectiveness with ethical obligations demands transparent oversight and strict rules of engagement to prevent unlawful surveillance and cyberattacks that could harm civilians or violate sovereignty.
Integration of Communications Interception within CEMA Frameworks
Communications interception serves as a critical component within Cyber Electromagnetic Activities (CEMA) frameworks, enabling real-time collection and analysis of adversary communications for enhanced situational awareness. Integrating communications interception technologies with electronic warfare and cyber operations facilitates comprehensive spectrum dominance and threat disruption. This convergence optimizes intelligence fusion, accelerating decision-making and operational effectiveness in contested electromagnetic environments.
Emerging Threats and Countermeasures
Communications interception increasingly exploits advanced encryption bypass techniques, posing significant risks to military operations and intelligence integrity. Cyber electromagnetic activities (CEMA) integrate electronic warfare with cyber strategies to disrupt adversary command and control systems, representing a multifaceted emerging threat. Countermeasures emphasize adaptive signal processing, AI-driven anomaly detection, and resilient network architectures to mitigate interception vulnerabilities and CEMA attacks effectively.
Future Trends in Defense Signal Exploitation
Future trends in defense signal exploitation emphasize the integration of advanced artificial intelligence and machine learning algorithms to enhance communications interception capabilities, enabling real-time threat detection and analysis. Cyber Electromagnetic Activities (CEMA) are evolving to encompass multi-domain operations combining electronic warfare, cyber operations, and signal intelligence to disrupt adversary networks and protect critical infrastructure. Emerging technologies such as quantum computing and 5G-enabled sensors will significantly increase the precision and scope of signal exploitation in complex battlespace environments.
Related Important Terms
Full Spectrum Cyberspace Operations
Communications interception involves the targeted capture and analysis of adversary signals and data transmissions, providing critical intelligence within Full Spectrum Cyberspace Operations. Cyber Electromagnetic Activities (CEMA) integrate offensive and defensive cyber capabilities with electronic warfare to disrupt, degrade, or exploit enemy networks, ensuring dominance across the electromagnetic spectrum and cyberspace domains.
Passive SIGINT Collection
Passive SIGINT collection involves intercepting electromagnetic signals without emitting detectable signals, enabling covert intelligence gathering on enemy communications and radar systems. Unlike Cyber Electromagnetic Activities (CEMA), which combine offensive and defensive cyber operations with electromagnetic spectrum actions, passive SIGINT prioritizes stealthy monitoring to provide actionable intelligence without alerting adversaries.
RF Denial and Deception
Communications interception targets enemy signals to extract intelligence, while Cyber Electromagnetic Activities (CEMA) integrate electronic warfare, cyber operations, and electromagnetic spectrum management to disrupt adversary command and control. RF denial and deception techniques under CEMA employ jamming, spoofing, and signal manipulation to degrade or mislead enemy communications, enhancing battlefield advantage and information dominance.
Spectrum Warfare Orchestration
Communications Interception primarily targets enemy transmissions within the electromagnetic spectrum to gather intelligence, while Cyber Electromagnetic Activities (CEMA) integrate cyber operations with electronic warfare capabilities to disrupt, deceive, and manipulate enemy spectrum use. Spectrum Warfare Orchestration synchronizes these elements, using advanced signal processing and cyber tools to achieve real-time dominance over contested communication and radar frequencies.
Cellular IMSI Catching
Cellular IMSI catching enables defense forces to intercept mobile communications by capturing International Mobile Subscriber Identity (IMSI) numbers, providing critical intelligence on enemy movements and network usage. Unlike broader cyber electromagnetic activities that encompass signal disruption and electronic warfare, IMSI catching specifically targets cellular networks to covertly track and monitor adversary communication patterns with minimal detection risk.
Multi-Domain CEMA Integration
Communications Interception enables real-time intelligence gathering by exploiting adversary signals, while Cyber Electromagnetic Activities (CEMA) encompass offensive and defensive operations across cyberspace and the electromagnetic spectrum. Integrating Multi-Domain CEMA synchronizes cyber, electronic warfare, and signals intelligence capabilities to achieve comprehensive situational awareness and operational dominance in contested environments.
Tactical Mesh Interception
Tactical Mesh Interception leverages decentralized network nodes to capture and analyze enemy communications within contested electromagnetic environments, enhancing situational awareness and operational security. Unlike traditional Communications Interception that targets specific signals, Cyber Electromagnetic Activities integrate real-time cyber operations with electronic warfare to disrupt, exploit, and manipulate adversary networks across multiple frequencies.
Cognitive Electronic Attack
Cognitive Electronic Attack (CEA) leverages artificial intelligence and machine learning to exploit enemy communication systems, disrupting signal integrity and decision-making processes more effectively than traditional Communications Interception, which primarily focuses on passive data collection. By manipulating electromagnetic environments and understanding cognitive behaviors, CEA enables dynamic, real-time countermeasures that degrade adversary command and control capabilities without direct cyber intrusion.
Over-the-Air Reconnaissance
Over-the-air reconnaissance in communications interception involves capturing and analyzing wireless signals to gather intelligence, whereas cyber electromagnetic activities encompass a broader range of operations including electronic warfare, spectrum management, and cyber defense targeting electromagnetic emissions. Advanced defense systems integrate signal processing and electromagnetic spectrum exploitation to enhance situational awareness and disrupt adversary communications effectively.
Cross-Layer Eavesdropping
Cross-layer eavesdropping in defense involves intercepting communications by exploiting vulnerabilities across multiple network protocol layers, integrating cyber electromagnetic activities (CEMA) with traditional signals intelligence to capture data undetectably. This technique enhances situational awareness by combining electromagnetic spectrum exploitation and cyber intrusion methods to intercept, analyze, and manipulate adversary communications in real-time.
Communications Interception vs Cyber Electromagnetic Activities Infographic
 industrydif.com
industrydif.com