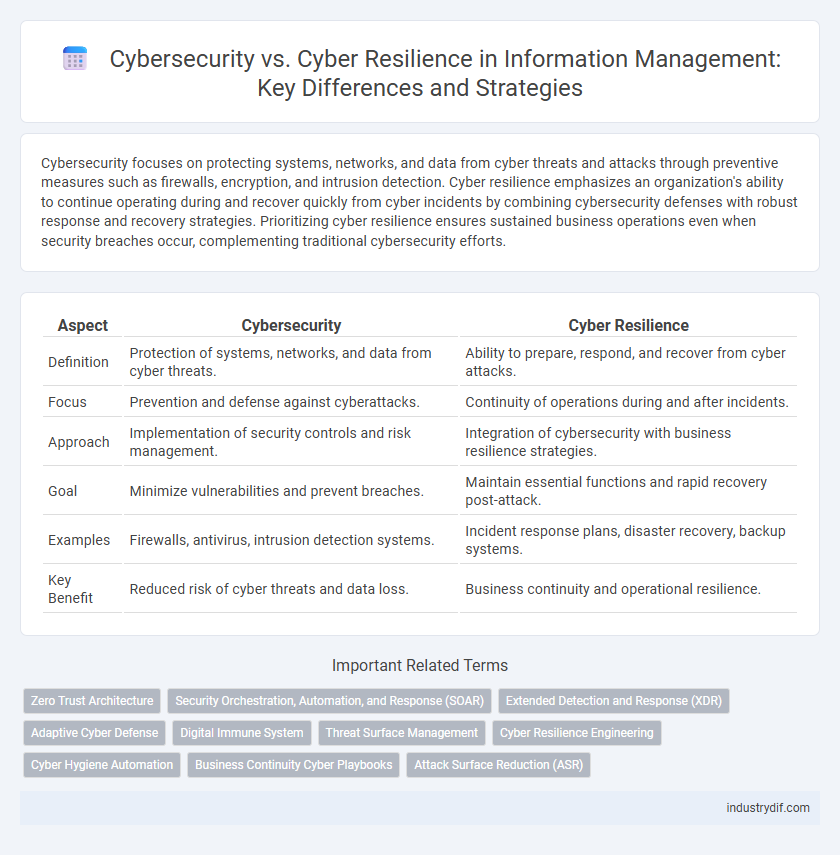
Cybersecurity focuses on protecting systems, networks, and data from cyber threats and attacks through preventive measures such as firewalls, encryption, and intrusion detection. Cyber resilience emphasizes an organization's ability to continue operating during and recover quickly from cyber incidents by combining cybersecurity defenses with robust response and recovery strategies. Prioritizing cyber resilience ensures sustained business operations even when security breaches occur, complementing traditional cybersecurity efforts.
Table of Comparison
| Aspect | Cybersecurity | Cyber Resilience |
|---|---|---|
| Definition | Protection of systems, networks, and data from cyber threats. | Ability to prepare, respond, and recover from cyber attacks. |
| Focus | Prevention and defense against cyberattacks. | Continuity of operations during and after incidents. |
| Approach | Implementation of security controls and risk management. | Integration of cybersecurity with business resilience strategies. |
| Goal | Minimize vulnerabilities and prevent breaches. | Maintain essential functions and rapid recovery post-attack. |
| Examples | Firewalls, antivirus, intrusion detection systems. | Incident response plans, disaster recovery, backup systems. |
| Key Benefit | Reduced risk of cyber threats and data loss. | Business continuity and operational resilience. |
Defining Cybersecurity: Core Concepts and Principles
Cybersecurity involves the protection of systems, networks, and data from cyber threats through measures such as encryption, firewalls, and access controls. It emphasizes preventing unauthorized access, detecting potential breaches, and responding to cyber incidents to safeguard confidentiality, integrity, and availability of information. Core principles include risk management, threat intelligence, vulnerability assessment, and implementing security policies aligned with organizational objectives.
Understanding Cyber Resilience: Beyond Prevention
Cyber resilience encompasses an organization's ability to continuously operate and recover quickly from cyberattacks, extending beyond traditional cybersecurity measures focused solely on prevention. It integrates risk management, incident response, and business continuity strategies to maintain essential functions despite disruptions. Emphasizing adaptability and recovery ensures sustained protection against evolving threats and minimizes potential operational downtime.
Key Differences Between Cybersecurity and Cyber Resilience
Cybersecurity primarily focuses on preventing, detecting, and responding to cyber threats by securing networks, systems, and data from unauthorized access or attacks. Cyber resilience extends beyond cybersecurity by emphasizing an organization's ability to continue operating and quickly recover during and after a cyber incident. Key differences include cybersecurity's proactive defense measures versus cyber resilience's adaptive capacity for maintaining business continuity amid disruptions.
The Importance of a Holistic Security Approach
Cybersecurity and cyber resilience both play critical roles in protecting digital assets, but a holistic security approach integrates prevention, detection, response, and recovery strategies to ensure comprehensive defense against evolving cyber threats. Prioritizing this integrative framework enhances an organization's ability to maintain operational continuity, minimize damage from breaches, and adapt to new attack vectors in real-time. Employing advanced technologies such as AI-driven threat detection and continuous monitoring strengthens resilience by enabling proactive risk management alongside traditional cybersecurity measures.
Threat Landscape: Evolving Cyber Risks Explained
The threat landscape in cybersecurity continuously evolves with increasingly sophisticated ransomware, phishing attacks, and zero-day exploits targeting organizations worldwide. Cyber resilience extends beyond traditional defenses by emphasizing rapid detection, response, and recovery to minimize operational disruptions caused by these dynamic threats. Understanding the distinction between cybersecurity's preventive measures and cyber resilience's adaptive strategies is critical for managing evolving cyber risks effectively.
Building Blocks of Cybersecurity Strategies
Core building blocks of cybersecurity strategies include robust threat detection systems, multi-layered access controls, and continuous vulnerability assessments to prevent unauthorized access and data breaches. Integrating advanced encryption methods and real-time monitoring ensures data integrity and rapid incident response capabilities, forming the backbone of effective cyber defenses. Emphasizing employee training and strict policy enforcement further strengthens the cybersecurity framework by reducing human error and enhancing organizational awareness.
Essential Pillars of Cyber Resilience Frameworks
Cyber resilience frameworks revolve around essential pillars including continuous risk assessment, robust incident response, and adaptive recovery strategies to ensure operational continuity despite cyber threats. Emphasizing proactive threat detection and comprehensive data protection, these frameworks integrate cybersecurity measures with organizational agility and business impact analysis. Effective cyber resilience combines technology, processes, and people to maintain mission-critical functions and rapidly restore normal operations after cyber events.
Integrating Cybersecurity with Cyber Resilience
Integrating cybersecurity with cyber resilience strengthens an organization's ability to prevent, detect, and respond to sophisticated cyber threats while ensuring continuity of critical operations. This approach combines proactive defense mechanisms like threat intelligence and vulnerability management with adaptive recovery processes such as incident response planning and business continuity strategies. Emphasizing both protection and recovery enhances overall cyber posture, minimizing downtime and data loss during cyber incidents.
Measuring Success: Metrics for Cybersecurity and Cyber Resilience
Measuring success in cybersecurity involves metrics such as the number of detected incidents, mean time to detect (MTTD), and mean time to respond (MTTR), which focus on prevention and rapid response to threats. Cyber resilience metrics emphasize recovery time objectives (RTO), system availability, and the ability to maintain critical operations during and after cyber incidents. Organizations increasingly integrate both cybersecurity and cyber resilience metrics to ensure comprehensive protection and operational continuity.
Future Trends: Shaping Security and Resilience in the Digital Age
Cybersecurity and cyber resilience are evolving to address increasingly sophisticated threats with future trends emphasizing adaptive AI-driven defenses and proactive threat intelligence sharing. Integration of zero-trust architectures and quantum-resistant encryption algorithms is set to redefine how organizations protect digital assets and ensure continuous operations despite cyber incidents. Emphasizing resilience, businesses are prioritizing automated incident response and recovery frameworks to minimize downtime and maintain digital trust in the rapidly advancing digital age.
Related Important Terms
Zero Trust Architecture
Zero Trust Architecture enhances cybersecurity by consistently verifying user identity and device integrity before granting access, reducing the risk of breaches. Cyber resilience integrates this approach to ensure rapid detection, response, and recovery from attacks, maintaining operational continuity despite cybersecurity threats.
Security Orchestration, Automation, and Response (SOAR)
Cybersecurity focuses on protecting networks and systems from attacks, while cyber resilience emphasizes the ability to rapidly recover and maintain operations during incidents. Security Orchestration, Automation, and Response (SOAR) platforms enhance both by automating threat detection, streamlining incident response workflows, and enabling coordinated defense strategies to minimize downtime and damage.
Extended Detection and Response (XDR)
Extended Detection and Response (XDR) enhances cybersecurity by integrating multiple security products into a unified platform for comprehensive threat detection and automated response, improving visibility across endpoints, networks, and cloud environments. Cyber resilience leverages XDR capabilities to not only prevent and detect cyberattacks but also ensure rapid recovery and continuous operation despite security breaches.
Adaptive Cyber Defense
Adaptive cyber defense enhances cybersecurity by continuously monitoring threats and dynamically responding to attacks, ensuring systems maintain operational integrity. Unlike traditional cybersecurity, cyber resilience integrates adaptive strategies to anticipate, absorb, and recover from cyber incidents, minimizing damage and downtime.
Digital Immune System
Cybersecurity focuses on protecting digital assets from threats through prevention and detection, while cyber resilience emphasizes the ability to recover and maintain operations during and after cyber incidents. The Digital Immune System integrates advanced threat intelligence, automated response, and adaptive defense mechanisms to enhance both cybersecurity and cyber resilience in dynamic digital environments.
Threat Surface Management
Cybersecurity focuses on protecting systems from attacks by minimizing vulnerabilities, while cyber resilience emphasizes maintaining operational continuity despite breaches; Threat Surface Management plays a critical role by continuously identifying and reducing attack vectors across networks, endpoints, and cloud environments. Effective Threat Surface Management leverages real-time asset discovery, vulnerability assessments, and attack path analysis to enhance both cybersecurity defense and cyber resilience strategies.
Cyber Resilience Engineering
Cyber Resilience Engineering emphasizes the design and implementation of systems that maintain essential functions and recover quickly from cyber incidents by integrating risk management, adaptive response, and continuous monitoring. This approach extends beyond traditional cybersecurity by focusing on ensuring operational continuity despite attacks, leveraging techniques such as redundancy, segmentation, and real-time threat intelligence to minimize impact and accelerate recovery.
Cyber Hygiene Automation
Cyber hygiene automation enhances cybersecurity by systematically managing vulnerabilities and enforcing security policies, reducing human error and response times. Integrating automated tools within cyber resilience frameworks improves an organization's ability to detect, respond to, and recover from cyber threats efficiently.
Business Continuity Cyber Playbooks
Business continuity cyber playbooks enhance organizational preparedness by integrating cybersecurity measures with cyber resilience strategies, ensuring rapid recovery from cyber incidents. These playbooks provide structured protocols for incident response, minimizing downtime and maintaining operational integrity during cyber disruptions.
Attack Surface Reduction (ASR)
Cybersecurity focuses on defending IT systems by minimizing vulnerabilities and preventing unauthorized access, whereas Cyber Resilience emphasizes maintaining operational continuity despite attacks. Attack Surface Reduction (ASR) is a critical strategy in both, involving techniques like application whitelisting, network segmentation, and patch management to reduce exploitable entry points and limit attack vectors.
Cybersecurity vs Cyber Resilience Infographic
 industrydif.com
industrydif.com