Cloud computing offers scalable and flexible resources by delivering services over the internet, enabling businesses to manage data and applications efficiently. Confidential computing enhances cloud security by protecting data in use through hardware-based trusted execution environments, preventing unauthorized access during processing. Combining both technologies ensures robust, secure, and efficient cloud infrastructures for sensitive workloads.
Table of Comparison
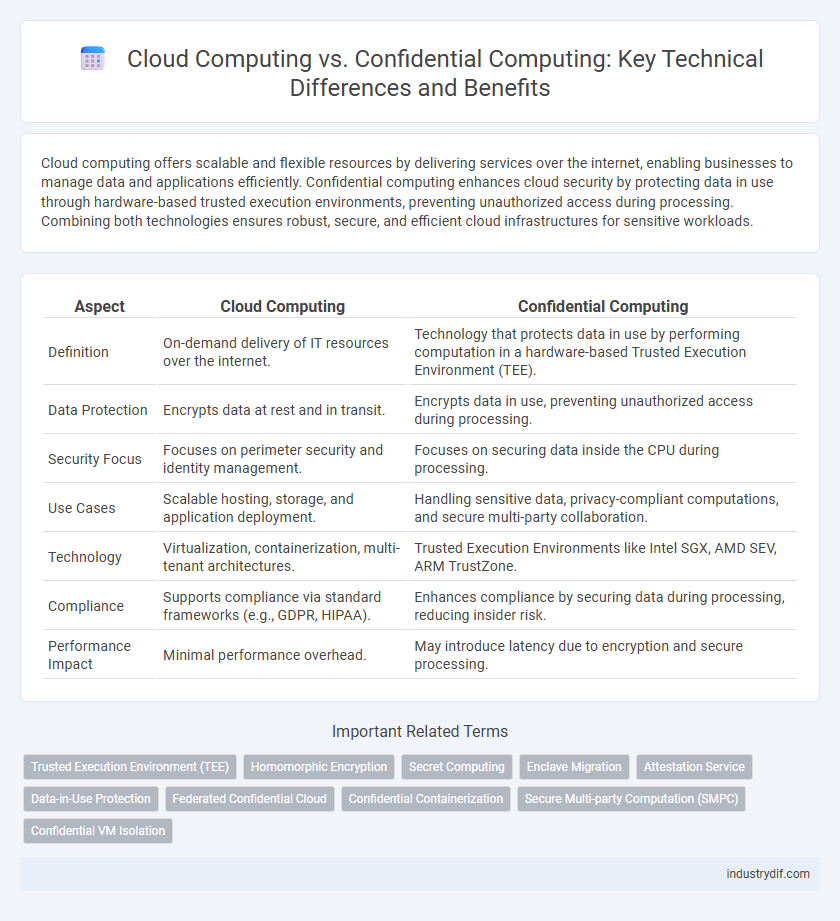
| Aspect | Cloud Computing | Confidential Computing |
|---|---|---|
| Definition | On-demand delivery of IT resources over the internet. | Technology that protects data in use by performing computation in a hardware-based Trusted Execution Environment (TEE). |
| Data Protection | Encrypts data at rest and in transit. | Encrypts data in use, preventing unauthorized access during processing. |
| Security Focus | Focuses on perimeter security and identity management. | Focuses on securing data inside the CPU during processing. |
| Use Cases | Scalable hosting, storage, and application deployment. | Handling sensitive data, privacy-compliant computations, and secure multi-party collaboration. |
| Technology | Virtualization, containerization, multi-tenant architectures. | Trusted Execution Environments like Intel SGX, AMD SEV, ARM TrustZone. |
| Compliance | Supports compliance via standard frameworks (e.g., GDPR, HIPAA). | Enhances compliance by securing data during processing, reducing insider risk. |
| Performance Impact | Minimal performance overhead. | May introduce latency due to encryption and secure processing. |
Understanding Cloud Computing
Cloud computing delivers scalable IT resources over the internet, enabling flexible storage, processing power, and application deployment without physical hardware constraints. Key elements include Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), each offering distinct levels of control and management. Cloud computing emphasizes cost efficiency, elasticity, and global accessibility, forming the foundation for modern enterprise digital transformation.
Defining Confidential Computing
Confidential Computing secures data in use by encrypting information during processing, unlike traditional Cloud Computing which primarily protects data at rest and in transit. This technology leverages hardware-based Trusted Execution Environments (TEEs) to ensure data confidentiality and integrity against internal and external threats. By isolating sensitive workloads, Confidential Computing enables secure collaboration and regulatory compliance in multi-tenant cloud environments.
Key Differences Between Cloud and Confidential Computing
Cloud computing delivers scalable and on-demand IT resources over the internet through shared infrastructure, prioritizing flexibility and cost-efficiency. Confidential computing enhances data security by encrypting data during processing using hardware-based Trusted Execution Environments (TEEs), preventing unauthorized access even in cloud environments. Key differences include cloud computing's focus on resource elasticity and multi-tenancy, while confidential computing emphasizes data confidentiality and integrity during computation.
Security Implications in Cloud Environments
Cloud computing enhances scalability and cost-efficiency by leveraging shared resources but poses risks such as data breaches and unauthorized access due to multi-tenancy and centralized storage. Confidential computing introduces hardware-based Trusted Execution Environments (TEEs) to protect data in use, ensuring that sensitive information remains encrypted even during processing, significantly mitigating insider threats and external attacks. Integrating confidential computing within cloud infrastructures elevates security frameworks by providing end-to-end data protection across storage, transit, and processing stages.
Data Privacy in Confidential Computing
Confidential Computing enhances data privacy by encrypting data not only at rest and in transit but also during processing, using hardware-based Trusted Execution Environments (TEEs). This approach minimizes exposure of sensitive information to unauthorized access, including from cloud service providers and system administrators. By isolating workloads in secure enclaves, Confidential Computing significantly reduces the risk of data breaches in cloud environments compared to traditional Cloud Computing models.
Use Cases for Cloud Computing
Cloud computing excels in scalable data storage, on-demand application deployment, and global collaboration through virtualized resources. Key use cases include disaster recovery solutions, big data analytics, and hosting machine learning models. Enterprises leverage cloud platforms like AWS, Azure, and Google Cloud for cost-efficient infrastructure management and seamless integration with DevOps pipelines.
Industry Applications of Confidential Computing
Confidential computing enhances cloud computing by protecting sensitive data during processing, making it vital for industries like healthcare, finance, and government where data privacy and regulatory compliance are critical. It enables secure multi-party computations, confidential AI model training, and protects intellectual property in cloud environments. Enterprises leverage confidential computing to securely handle regulated data, reduce data breach risks, and ensure trust in hybrid and multi-cloud deployments.
Performance and Scalability Considerations
Cloud computing offers extensive scalability through elastic resource allocation across distributed data centers, enabling high-performance workloads with minimal latency. Confidential computing enhances security by encrypting data in-use but may introduce processing overhead due to hardware-based Trusted Execution Environments (TEEs), impacting raw performance metrics. Balancing scalability and confidentiality requires evaluating the trade-offs between cloud-native resource flexibility and the computational costs of secure enclave operations.
Compliance and Regulatory Factors
Cloud computing offers scalable resources but poses challenges in meeting strict compliance and regulatory requirements due to multi-tenant environments and data sovereignty issues. Confidential computing enhances data protection by encrypting data in use, addressing compliance mandates such as GDPR, HIPAA, and PCI DSS through hardware-based trusted execution environments (TEEs). Organizations aiming for stringent regulatory adherence benefit from confidential computing's ability to ensure data confidentiality across cloud workflows without compromising scalability.
Future Trends in Secure Computing Technologies
Confidential computing enhances cloud computing by enabling data processing within hardware-based trusted execution environments, significantly improving data security and privacy. Emerging technologies like homomorphic encryption and secure multi-party computation are poised to integrate with confidential computing to further protect data during processing. Future secure computing trends emphasize collaboration between hardware manufacturers and cloud providers to create seamless, scalable solutions that address evolving cybersecurity threats.
Related Important Terms
Trusted Execution Environment (TEE)
Trusted Execution Environment (TEE) in Confidential Computing provides a hardware-isolated secure area within a processor, enabling sensitive data to be processed with higher confidentiality and integrity compared to traditional Cloud Computing environments. While Cloud Computing offers scalable and flexible resources, TEEs enhance security by protecting data in use from unauthorized access or tampering during computation.
Homomorphic Encryption
Homomorphic encryption enables computations on encrypted data without exposing sensitive information, significantly enhancing security in confidential computing environments compared to traditional cloud computing models. This technology allows organizations to leverage the scalability and flexibility of cloud infrastructure while maintaining data privacy and integrity during processing.
Secret Computing
Cloud computing offers scalable infrastructure and on-demand resources, while confidential computing enhances data security by encrypting data in use through hardware-based Trusted Execution Environments (TEEs). Secret computing, a subset of confidential computing, focuses on protecting sensitive computations from insider threats and external attacks by isolating data processing within secure enclaves.
Enclave Migration
Enclave migration in confidential computing enables secure transfer of sensitive workloads across different cloud environments by isolating data within hardware-based Trusted Execution Environments (TEEs), offering enhanced protection compared to traditional cloud computing models that rely on software-based security measures. This process ensures data integrity and confidentiality during migration, addressing critical challenges in multi-cloud and hybrid cloud deployments.
Attestation Service
Attestation services in cloud computing validate the integrity and trustworthiness of hardware and software environments by providing cryptographic proof that a system's state meets security policies. Confidential computing enhances this by using attestation to ensure that data remains encrypted and isolated in secure enclaves, preventing unauthorized access even during processing.
Data-in-Use Protection
Cloud computing provides scalable resources for data storage and processing, but traditional environments often leave data vulnerable during use. Confidential computing enhances security by encrypting data-in-use through hardware-based Trusted Execution Environments (TEEs), ensuring sensitive information remains protected even while being processed.
Federated Confidential Cloud
Federated Confidential Cloud integrates the security assurances of Confidential Computing with the distributed architecture of Federated Cloud, enabling encrypted data processing across multiple organizations without exposing sensitive information. This approach enhances data privacy and compliance by leveraging hardware-based trusted execution environments (TEEs) and secure multi-party computation within a decentralized cloud environment.
Confidential Containerization
Confidential containerization enhances cloud computing by encrypting data in use, ensuring workloads run securely within hardware-based trusted execution environments (TEEs). This technology mitigates risks of data exposure during processing, enabling compliance with stringent security frameworks while maintaining cloud scalability and efficiency.
Secure Multi-party Computation (SMPC)
Secure Multi-party Computation (SMPC) enhances data privacy by enabling multiple parties to jointly compute a function over their inputs while keeping those inputs private, a critical feature distinguishing Confidential Computing from traditional Cloud Computing. Unlike conventional cloud models where data is exposed during processing, SMPC leverages cryptographic protocols to ensure data confidentiality and integrity across decentralized environments.
Confidential VM Isolation
Confidential VM Isolation in Confidential Computing leverages hardware-based Trusted Execution Environments (TEEs) to protect data in use, ensuring that sensitive workloads remain encrypted and isolated from the host hypervisor and other VMs. Unlike traditional Cloud Computing, which primarily secures data at rest and in transit, Confidential VM Isolation provides robust defense against insider threats and unauthorized access by enforcing strict memory encryption and attestation within virtual machines.
Cloud Computing vs Confidential Computing Infographic
 industrydif.com
industrydif.com