Firewall technology acts as a barrier that filters incoming and outgoing network traffic based on predefined rules, primarily protecting the perimeter of a network. Zero Trust Security adopts a more granular approach by continuously verifying the identity and trustworthiness of every device and user attempting to access resources, regardless of their location inside or outside the network. While firewalls establish a basic level of security through boundary protection, Zero Trust enforces strict access controls and continuous monitoring to minimize risk from internal and external threats.
Table of Comparison
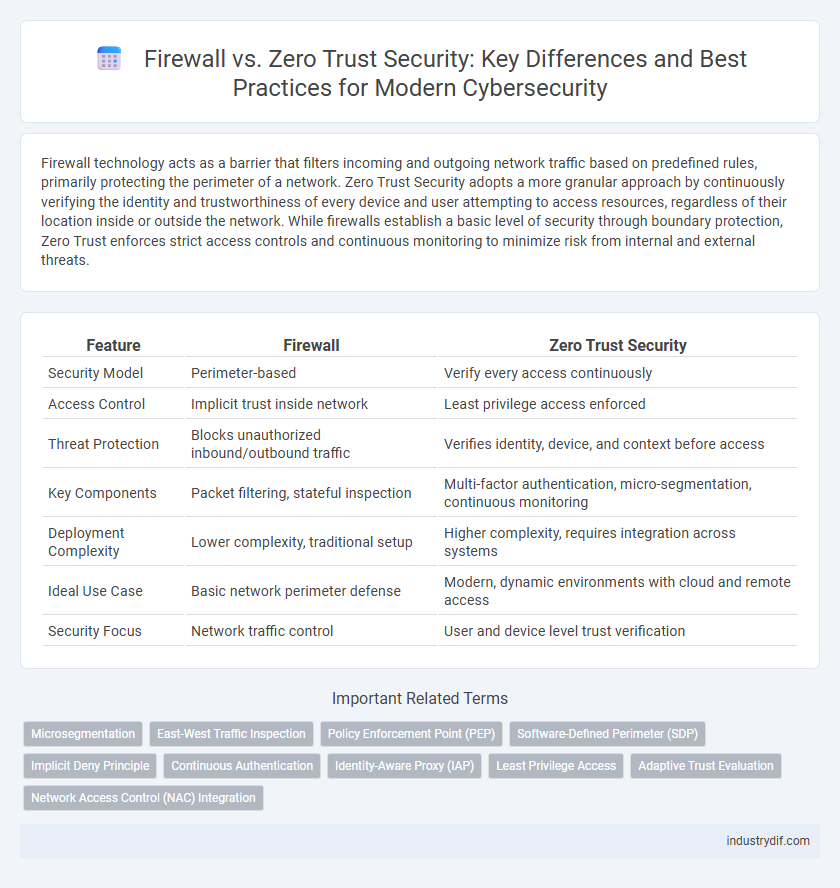
| Feature | Firewall | Zero Trust Security |
|---|---|---|
| Security Model | Perimeter-based | Verify every access continuously |
| Access Control | Implicit trust inside network | Least privilege access enforced |
| Threat Protection | Blocks unauthorized inbound/outbound traffic | Verifies identity, device, and context before access |
| Key Components | Packet filtering, stateful inspection | Multi-factor authentication, micro-segmentation, continuous monitoring |
| Deployment Complexity | Lower complexity, traditional setup | Higher complexity, requires integration across systems |
| Ideal Use Case | Basic network perimeter defense | Modern, dynamic environments with cloud and remote access |
| Security Focus | Network traffic control | User and device level trust verification |
Understanding Firewalls: The Traditional Approach
Firewalls serve as the foundational security barrier by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. Traditional firewalls rely on perimeter-based defense mechanisms to block unauthorized access and filter traffic between trusted internal networks and untrusted external networks. While effective for basic threat prevention, their rigid architecture often struggles against sophisticated cyber attacks that exploit insider threats or lateral movement within the network.
What is Zero Trust Security?
Zero Trust Security is a cybersecurity framework that mandates strict identity verification for every user, device, and application attempting to access resources, regardless of their location within or outside the network perimeter. Unlike traditional firewalls that rely heavily on perimeter defenses, Zero Trust operates on the principle of "never trust, always verify," implementing continuous monitoring, micro-segmentation, and least-privilege access controls to minimize attack surfaces. This approach reduces risks of lateral movement by cybercriminals and enhances protection against modern threats such as insider attacks and advanced persistent threats (APTs).
Core Principles: Firewall vs Zero Trust
Firewalls operate by establishing predefined network boundaries and filtering traffic based on IP addresses, ports, and protocols to block unauthorized access. Zero Trust Security enforces strict identity verification and least privilege access regardless of network location, ensuring continuous validation of all users and devices. Unlike traditional firewalls, Zero Trust minimizes implicit trust and assumes breach, focusing on granular access control and real-time monitoring.
Network Perimeter: Is it Still Relevant?
The network perimeter model, traditionally enforced by firewalls, is increasingly challenged by the rise of Zero Trust Security, which eliminates implicit trust regardless of network location. Firewalls focus on controlling traffic at defined boundaries, but the proliferation of cloud services, remote work, and mobile devices renders static perimeters obsolete. Zero Trust Security continuously verifies user identity and device integrity, making the concept of a fixed network perimeter largely irrelevant in modern cybersecurity strategies.
Access Control Mechanisms Compared
Firewalls primarily rely on perimeter-based access control, filtering traffic based on IP addresses, ports, and protocols to establish trusted network boundaries. Zero Trust Security enforces strict identity verification and micro-segmentation, granting access based on user identity, device posture, and real-time risk assessments regardless of network location. This granular, dynamic approach reduces attack surfaces and limits lateral movement more effectively than traditional firewall-based controls.
Authentication Strategies: Legacy vs Zero Trust
Legacy firewall authentication relies on perimeter-based access controls, granting users broad network access once inside, which increases vulnerability to lateral movement attacks. Zero Trust Security emphasizes continuous verification through multi-factor authentication (MFA), device posture checks, and adaptive access policies, ensuring that every access request is authenticated and authorized regardless of network location. This shift reduces attack surfaces by limiting implicit trust and enforcing least-privilege access across all network segments.
Threat Detection and Response Differences
Firewalls primarily function as perimeter defense mechanisms that filter incoming and outgoing network traffic based on predefined rules, offering limited visibility into internal threats. Zero Trust Security employs continuous verification and micro-segmentation, enabling real-time threat detection and adaptive response across all network layers and endpoints. Unlike traditional firewalls, Zero Trust frameworks utilize behavioral analytics and identity-based access controls to detect and respond to threats dynamically, reducing the risk of lateral movement within systems.
Scalability and Flexibility in Modern Infrastructures
Firewalls offer foundational network security but often struggle with scalability and dynamic adaptability in complex, cloud-native environments. Zero Trust Security frameworks provide enhanced flexibility by continuously verifying identities and device trustworthiness, enabling secure access control in hybrid and multi-cloud infrastructures. Their scalable architecture supports granular policy enforcement, crucial for modern, distributed systems undergoing rapid change.
Compliance and Regulatory Implications
Firewalls primarily enforce perimeter security, which may fall short of comprehensive compliance mandates such as GDPR, HIPAA, or PCI-DSS, requiring granular access controls and continuous verification. Zero Trust Security frameworks align more closely with regulatory requirements by enforcing strict identity verification, least-privilege access, and detailed audit trails, significantly reducing the risk of data breaches and non-compliance penalties. Organizations adopting Zero Trust reduce audit complexities through automated compliance reporting and real-time policy enforcement across hybrid environments.
Choosing the Right Security Model for Your Enterprise
Selecting the appropriate security model for your enterprise hinges on understanding the limitations of traditional firewalls, which primarily regulate perimeter access but struggle with modern threats inside the network. Zero Trust Security enforces strict identity verification for every person and device trying to access resources, minimizing lateral movement risks and insider threats. Enterprises prioritizing granular access control and adaptive security measures benefit significantly from adopting a Zero Trust framework over conventional firewall defenses.
Related Important Terms
Microsegmentation
Microsegmentation enhances Zero Trust Security by dividing a network into granular zones to enforce strict access controls and minimize lateral movement of threats, unlike traditional firewalls that primarily focus on perimeter defense. This approach significantly improves security posture by ensuring continuous verification and limiting access based on context, user identity, and device compliance.
East-West Traffic Inspection
Firewalls primarily monitor North-South traffic by filtering data entering or leaving a network perimeter, whereas Zero Trust Security enforces strict East-West traffic inspection within the internal network to prevent lateral movement of threats. Implementing micro-segmentation and continuous authentication in Zero Trust models enhances real-time East-West traffic analysis, reducing the attack surface and mitigating internal breaches more effectively than traditional firewalls.
Policy Enforcement Point (PEP)
The Policy Enforcement Point (PEP) in firewall architectures serves as the primary barrier controlling inbound and outbound network traffic based on predefined rules, while in Zero Trust Security models, PEP operates continuously to verify every access request, enforcing granular, identity-based policies regardless of network location. Zero Trust's PEP integrates multi-factor authentication and real-time risk assessment to dynamically limit access, contrasting with traditional firewalls that rely on static perimeter defense mechanisms.
Software-Defined Perimeter (SDP)
Software-Defined Perimeter (SDP) enhances Zero Trust Security by dynamically creating secure, individualized network perimeters that restrict access based on strict identity verification and device posture assessment. Unlike traditional firewalls that rely on static IP filtering, SDP leverages software-driven, context-aware policies to minimize attack surfaces and deliver granular, adaptive security controls.
Implicit Deny Principle
Firewalls operate on predefined rules to filter traffic, but Zero Trust Security enforces the Implicit Deny Principle by assuming no trust and requiring continuous verification of every user and device. This principle minimizes attack surfaces by denying all access by default, allowing only explicitly authorized actions within a network.
Continuous Authentication
Zero Trust Security emphasizes continuous authentication by constantly verifying user identities and device integrity throughout the session, unlike traditional firewalls that grant access based on initial perimeter checks. This approach minimizes insider threats and lateral movement by enforcing real-time access decisions using adaptive policies and contextual data.
Identity-Aware Proxy (IAP)
Firewall technology primarily filters traffic based on IP addresses and port numbers, whereas Zero Trust Security leverages Identity-Aware Proxy (IAP) to enforce granular access controls by continuously verifying user identity and device context before granting application access. IAP integrates with multi-factor authentication and endpoint security, providing dynamic policy enforcement that reduces attack surfaces beyond traditional perimeter defenses.
Least Privilege Access
Zero Trust Security enforces least privilege access by continuously verifying user identity and device context before granting minimal necessary permissions, reducing attack surfaces. Traditional firewalls rely on perimeter defenses and static access rules, which often allow broader access levels, increasing vulnerability risks within internal networks.
Adaptive Trust Evaluation
Firewall systems primarily rely on predetermined rules and network perimeters to allow or block traffic, whereas Zero Trust Security continuously assesses user behavior, device posture, and contextual data through Adaptive Trust Evaluation to dynamically grant or restrict access, enhancing protection against evolving threats. This approach minimizes risks by treating all access requests as untrusted until verified, enabling real-time adjustments based on risk factors rather than static network boundaries.
Network Access Control (NAC) Integration
Firewall solutions provide perimeter-based defense by filtering traffic at network boundaries, while Zero Trust Security enforces strict identity verification and micro-segmentation for every access request. Integrating Network Access Control (NAC) with Zero Trust enhances continuous device posture assessment and dynamic policy enforcement, ensuring that only authenticated and compliant devices gain network access.
Firewall vs Zero Trust Security Infographic
 industrydif.com
industrydif.com