Infrastructure as Code (IaC) automates the provisioning and management of IT infrastructure through machine-readable definition files, enabling consistent and repeatable deployments. Policy as Code (PaC) embeds governance rules and compliance policies directly into code to enforce security and operational standards during automation workflows. Integrating IaC with PaC ensures that infrastructure deployments not only build resources efficiently but also adhere to organizational policies and regulatory requirements from the outset.
Table of Comparison
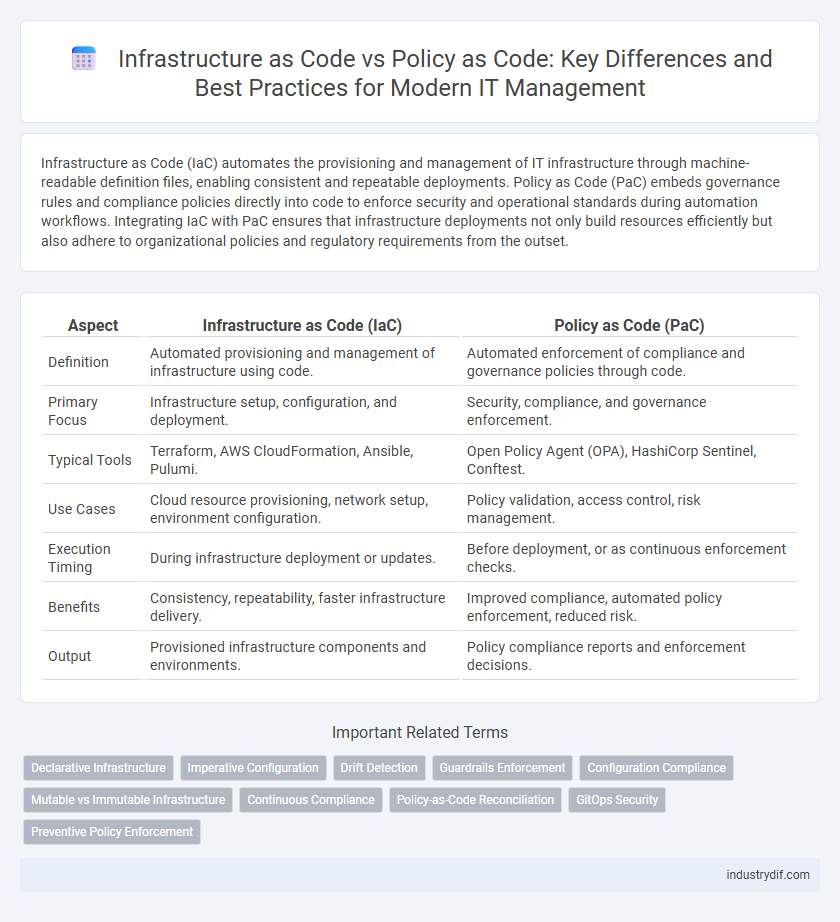
| Aspect | Infrastructure as Code (IaC) | Policy as Code (PaC) |
|---|---|---|
| Definition | Automated provisioning and management of infrastructure using code. | Automated enforcement of compliance and governance policies through code. |
| Primary Focus | Infrastructure setup, configuration, and deployment. | Security, compliance, and governance enforcement. |
| Typical Tools | Terraform, AWS CloudFormation, Ansible, Pulumi. | Open Policy Agent (OPA), HashiCorp Sentinel, Conftest. |
| Use Cases | Cloud resource provisioning, network setup, environment configuration. | Policy validation, access control, risk management. |
| Execution Timing | During infrastructure deployment or updates. | Before deployment, or as continuous enforcement checks. |
| Benefits | Consistency, repeatability, faster infrastructure delivery. | Improved compliance, automated policy enforcement, reduced risk. |
| Output | Provisioned infrastructure components and environments. | Policy compliance reports and enforcement decisions. |
Introduction to Infrastructure as Code (IaC)
Infrastructure as Code (IaC) automates the provisioning and management of computing resources through machine-readable definition files, enabling consistent and repeatable infrastructure deployment. IaC tools such as Terraform, AWS CloudFormation, and Ansible replace manual infrastructure configuration with scripts that define network, storage, and compute components. This approach reduces configuration drift, accelerates scalability, and enhances collaboration between development and operations teams by integrating infrastructure management into version-controlled codebases.
Understanding Policy as Code (PaC)
Policy as Code (PaC) enables organizations to automate governance and compliance by encoding policies directly into code, ensuring consistent enforcement across cloud and on-premises environments. Unlike Infrastructure as Code (IaC), which focuses on provisioning and managing resources, PaC integrates security, compliance, and operational policies early in the deployment pipeline. This approach reduces risks, accelerates audits, and provides continuous validation against regulatory standards through automated policy checks.
Key Principles of IaC and PaC
Infrastructure as Code (IaC) emphasizes versioned, declarative configurations that automate infrastructure provisioning, ensuring consistency and repeatability across environments. Policy as Code (PaC) integrates automated validation of compliance and security policies directly into the deployment pipeline, enforcing governance before infrastructure changes occur. Both IaC and PaC rely on immutability, automation, and version control, with IaC focusing on resource management and PaC concentrating on policy enforcement and risk mitigation.
Core Benefits of Infrastructure as Code
Infrastructure as Code (IaC) enables automated provisioning and management of cloud resources through declarative configuration files, significantly reducing manual errors and deployment times. Core benefits include enhanced scalability, consistent environments, and improved version control, facilitating rapid infrastructure changes and collaboration among development and operations teams. IaC also supports disaster recovery and auditability by maintaining infrastructure state in code repositories, ensuring reliable and reproducible infrastructure setups.
Core Benefits of Policy as Code
Policy as Code automates compliance enforcement by embedding security and governance rules directly into software development pipelines, reducing manual errors and accelerating deployment times. It ensures consistent policy application across heterogeneous infrastructure environments, enhancing auditability and traceability through version-controlled, human-readable policy definitions. By integrating with Infrastructure as Code, Policy as Code provides proactive risk management and accelerates remediation of misconfigurations before production deployment.
Differences Between IaC and PaC
Infrastructure as Code (IaC) automates the provisioning and management of IT infrastructure using declarative configurations, while Policy as Code (PaC) enforces governance by defining and automating compliance rules within those configurations. IaC focuses on creating and maintaining resources such as servers, networks, and storage, whereas PaC ensures these resources conform to organizational policies and security standards. Key differences lie in IaC's role in deployment versus PaC's role in validation and policy enforcement throughout the infrastructure lifecycle.
IaC Tools and Technologies
Infrastructure as Code (IaC) tools such as Terraform, AWS CloudFormation, and Ansible enable the automated provisioning and management of cloud resources using declarative configurations. In contrast, Policy as Code frameworks like Open Policy Agent (OPA) and HashiCorp Sentinel enforce compliance and governance by codifying security policies directly into the deployment pipelines. Integrating IaC with Policy as Code ensures consistent infrastructure deployment while maintaining regulatory requirements and operational standards across hybrid and multi-cloud environments.
PaC Frameworks and Integrations
Policy as Code (PaC) frameworks such as Open Policy Agent (OPA) and HashiCorp Sentinel enable automated policy enforcement by integrating with Infrastructure as Code (IaC) tools like Terraform and Kubernetes. These frameworks allow seamless validation of security, compliance, and operational policies during infrastructure provisioning, reducing manual intervention and risk of misconfiguration. PaC integrations enhance IaC workflows by embedding policy checks directly into CI/CD pipelines, ensuring consistent governance across cloud-native environments.
Best Practices for Combining IaC and PaC
Implementing best practices for combining Infrastructure as Code (IaC) and Policy as Code (PaC) involves embedding compliance and security policies directly within IaC templates to ensure automated enforcement during deployment. Version control systems should be used to track both infrastructure definitions and policy rules, enabling consistent audits and rollback capabilities. Integrating continuous integration/continuous deployment (CI/CD) pipelines with automated policy validation enhances risk mitigation by preventing non-compliant infrastructure from reaching production environments.
Choosing the Right Approach for Your Organization
Infrastructure as Code (IaC) automates the provisioning and management of cloud resources, ensuring consistent and repeatable infrastructure deployment. Policy as Code (PaC) enforces compliance and security policies by embedding organizational rules directly into the infrastructure lifecycle, enabling real-time governance. Choosing the right approach depends on your organization's priorities: prioritize IaC for scalable infrastructure management, and PaC for robust policy enforcement and regulatory compliance.
Related Important Terms
Declarative Infrastructure
Declarative Infrastructure emphasizes defining the desired state of infrastructure using Infrastructure as Code (IaC) tools like Terraform and AWS CloudFormation, enabling automated provisioning and consistent environments. Policy as Code complements this by embedding compliance and governance rules directly into the deployment pipeline using frameworks such as Open Policy Agent (OPA), ensuring infrastructure adheres to organizational standards.
Imperative Configuration
Imperative configuration in Infrastructure as Code (IaC) emphasizes step-by-step instructions for resource provisioning, while Policy as Code (PaC) uses declarative rules to enforce compliance and governance across infrastructure. Managing imperative configurations through IaC requires detailed scripting, whereas PaC integrates automated policy enforcement to maintain system integrity and security.
Drift Detection
Infrastructure as Code (IaC) automates the provisioning and management of cloud resources, enabling consistent environment deployment, while Policy as Code (PaC) enforces compliance by defining and validating governance rules within the infrastructure lifecycle. Drift detection in IaC identifies unintended deviations between the declared configuration and the actual deployed state, whereas PaC continuously monitors policy adherence to prevent security or compliance drift in real time.
Guardrails Enforcement
Infrastructure as Code (IaC) automates the provisioning of cloud resources, enabling consistent and scalable deployments, while Policy as Code (PaC) enforces guardrails by embedding compliance and security rules directly into the deployment pipeline to prevent misconfigurations. Guardrails enforcement through Policy as Code ensures that Infrastructure as Code adheres to organizational policies before changes are applied, reducing risks and enhancing governance.
Configuration Compliance
Infrastructure as Code (IaC) automates provisioning and managing cloud resources through declarative configurations, ensuring consistent environment setup, while Policy as Code (PaC) enforces compliance by embedding governance rules directly into deployment pipelines to validate configurations against organizational policies. Combining IaC with PaC enhances configuration compliance by not only defining infrastructure but also automatically auditing and remediating policy violations before deployment.
Mutable vs Immutable Infrastructure
Infrastructure as Code (IaC) often manages mutable infrastructure by enabling dynamic changes and updates to existing resources, whereas Policy as Code enforces immutable infrastructure principles by codifying security and compliance policies that prevent unauthorized modifications. Immutable infrastructure ensures consistency and reliability by replacing whole components rather than altering them, aligning with Policy as Code's focus on automated governance and compliance enforcement.
Continuous Compliance
Infrastructure as Code (IaC) automates the provisioning and management of cloud resources, while Policy as Code (PaC) enforces compliance by embedding security and governance rules directly into the deployment pipeline. Continuous compliance is achieved by integrating PaC into CI/CD workflows, ensuring real-time validation of infrastructure against regulatory standards and organizational policies.
Policy-as-Code Reconciliation
Policy-as-Code reconciliation ensures that infrastructure deployed through Infrastructure as Code (IaC) adheres to predefined compliance and security standards by continuously validating policies against infrastructure state. This automated alignment minimizes configuration drift, enforces governance, and accelerates remediation processes within cloud environments.
GitOps Security
Infrastructure as Code (IaC) automates environment provisioning while Policy as Code enforces security and compliance policies within GitOps workflows, ensuring continuous, automated validation of infrastructure against defined standards. Integrating Policy as Code into GitOps strengthens security by embedding real-time policy checks in CI/CD pipelines, mitigating risks before deployment.
Preventive Policy Enforcement
Infrastructure as Code automates the provisioning and management of IT resources using declarative configuration files, while Policy as Code embeds organizational policies directly into automated workflows to enforce compliance. Preventive policy enforcement in Policy as Code proactively blocks non-compliant infrastructure changes before deployment, ensuring security and governance are maintained consistently across environments.
Infrastructure as Code vs Policy as Code Infographic
 industrydif.com
industrydif.com